
A Hole in the (fire) Wall: Check Point Research reveals technique allowing attackers to bypass Firewall rules designed to stop NTLM credential thefts, and provides protection methods
Highlights:
- Check Point Research (CPR) reveals a technique abusing Microsoft Access’s feature (Part of the Office suite) that might allow attackers to bypass Firewall rules designed to stop NTLM (NetNTLM) credential theft.
- Attacks against NTLM vary between brute force attacks to Man In the Middle “pass-the-hash” scenarios, all aimed at stealing personal information and impersonating identities and with the firewall bypass capabilities and without any specific protection against the NTLM leakage through non-standard ports, the firewall’s defenses will be unable to protect the user.
- CPR responsibly disclosed the information to Microsoft, and provides protection and mitigation methods in this blog
Background: What is NTLM and how does attacks leverage it?
NTLM is an authentication protocol introduced by Microsoft in 1993. It is a challenge-response protocol: the server “keeps a secret” called an “NTLM hash” derived from the user’s password, every time that a user wants to log in, the server issues a randomized “challenge” and the user consults the password to compute the correct response.
Below are the three most well-known attacks against NTLM:
Brute-force attack uses inherent weaknesses in the NTLM hash function specification to recover the original password from the NTLM hash stored on the server.
Pass-the-hash attack abuses the fact that the NTLM hash itself is enough to correctly answer challenges[1], making the fact that a hash is used instead of the plain password substantially meaningless.
Relay attack is what is classically known as a “Man in the Middle” attack, where an attacker intercepts a handshake transaction, posing as the client when talking to the server and vice-versa — inconspicuously passing their messages on to one another until the crucial moment where the session is authenticated, at which point the attacker cuts the legitimate client out and carries on the conversation in their stead.
Weaponization of Legitimate Tools
In our earlier 2023 Cyber Security Report we have dedicated a chapter to the subject of threat actors ‘Weaponization of legitimate IT tools’ for attacks.
In this chapter, we explained that to combat sophisticated cybersecurity solutions, threat actors are developing and perfecting their attack techniques, which increasingly rely less on the use of custom malware and shift instead to utilizing non-signature tools. They use built-in operating system capabilities and tools, which are already installed on target systems, and exploit popular IT management tools that are less likely to raise suspicion when detected. Commercial off-the-shelf pentesting and Red Team tools are often used as well. Although this is not a new phenomenon, what was once rare and exclusive to sophisticated actors, has now become a widespread technique adopted by threat actors of all types.
When used for legitimate purposes, with linked tables, users can connect to an external database, such as a remote Microsoft SQL server.
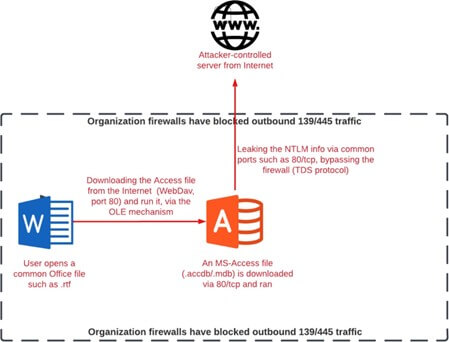
Would there be a gap before the feature can be weaponized and turned into an NTLM relay attack? Not a large one. An attacker can set up a server that they control, listening on port 80, and put its IP address in the above “server alias” field. Then they can send the database file, including the linked table, to the victim.
The attack can be launched as long as the victim opens the file he had been sent in this authentication process. This technique allows the attacker to bypass existing Firewall rules designed to block NTLM information stealing, initiated by external attacks. This is because the transferring port of the traffic that carries the NTLM information can be changed to more common ports such as 80/tcp.
The whole attack chain may look like the following:
Defense and Mitigation – Check Point Customers remain protected
This research has been shared with the Microsoft Security Response Center (MSRC). MSRC has acknowledged our findings and responded as follows:
We have successfully reproduced the attack on all available default Windows + Office environments, including the latest Windows 10/11 + Office 2021 environment. Check Point Research has been working with MSRC on this issue since early January, 2023, during which CPR supported in developing and delivering various protections for our customers against this attacking technique.
On July 17th, CPR tested our PoC again on the latest Office 2021 (Current Channel, version 2306, build 16529.20182), and found that Microsoft already mitigated the attack in this Office version. When the PoC runs, a warning dialog is now displayed to the end user, like the one shown below:
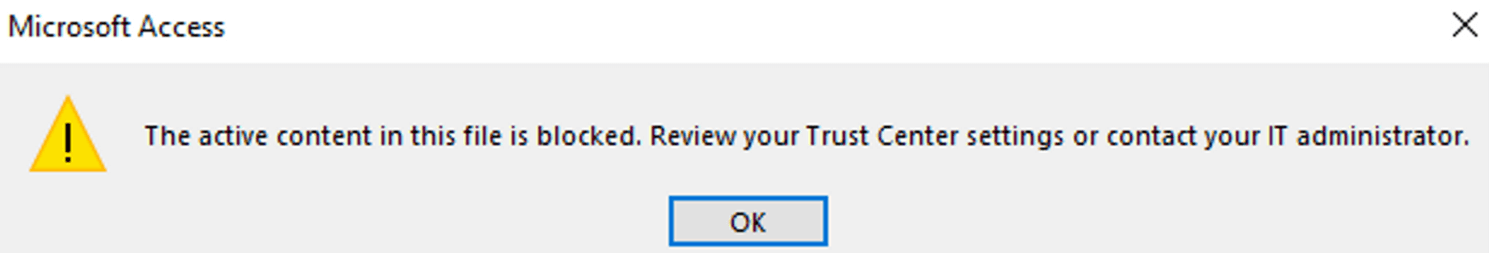
Please note that, even with the new warning dialog, there is no elegant way for the users to stop the NTLM leaking, because the only option for the user to choose is “OK”, as shown in the picture. Our tests showed that clicking the “OK” button would continue the exploitation. If the user does not click the “OK” button, the exploit would not continue. To remain protected against this attacking method, we recommend the following:
- Check Point has released an IPS signature named “Microsoft Windows NTLM Information Disclosure” to protect our If you are a Check Point IPS customer, you would be immune to this type of attack.
- Check Point customers are further protected and Microsoft Access files (.accdb) containing objects leading to NTLM leakage will be detected as Trojan.Wins.LinkedTable.A or Trojan.Wins.LinkedTable.B.
- Consider disabling macros in MS-Access, or removing it from your system altogether if it is not essential to your Office suite install.
- Always be wary of opening attachments from unsolicited sources
Check Point Research will continue to monitor for such exploitation and update on such exploits and suggested security measures for the industry.
For the full technical report please refer to the Check Point Research (CPR) blog.









