
Check Point Research Warns of New Backdoor used in Targeted Espionage Attacks in North Africa
Highlights:
- Check Point Research identified a backdoor used for highly targeted espionage attacks in Libya.
- The new backdoor, dubbed “Stealth Soldier,” specializes in surveillance functions like file exfiltration, screen recording, keystroke logging, and stealing browser information.
- The infrastructure associated with Stealth Soldier has some overlaps with that of “The Eye on the Nile,” marking the possible reappearance of this threat actor since their activities targeting Egyptian civilian society in 2019.
Executive summary
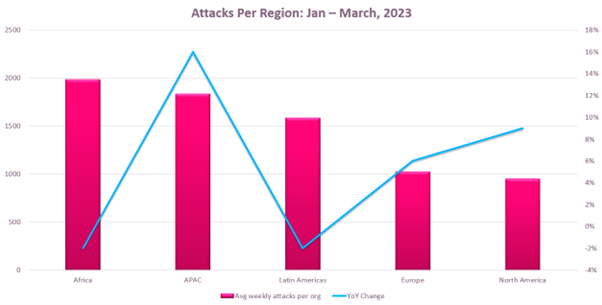
In the first quarter of 2023, the African region had the highest number of average weekly cyberattacks per organization – 1,983. Now, Check Point Research (CPR) has identified an ongoing operation against targets in North Africa involving a previously undisclosed multi-stage backdoor called “Stealth Soldier”. The malware Command and Control (C&C) network is part of a larger set of infrastructure, used at least in part for spear-phishing campaigns against government entities. Based on what we observed in the phishing website themes and VirusTotal submissions, the campaign appears to target Libyan organizations.
In this new research, CPR discusses the different techniques and tools used in this operation and its infrastructure. Researchers also provide technical analysis of the different Stealth Soldier versions and show similarities between this operation and “Eye on the Nile”. Eye on the Nile is a previous attack campaign targeting the region, which Amnesty International and Check Point Research linked to government-backed bodies.
CPR’s investigation began after they came across multiple files submitted to VirusTotal from Libya between the months of November 2022 to January 2023. The file names were in Arabic. Analysis of the files reveals that all of them are downloaders for different versions of the same malware, internally named Stealth Soldier.
Stealth Soldier is a custom implant, likely used in a limited set of targeted attacks. The implant enables surveillance operations and supports functionality such as keystroke logging and screenshot and microphone recordings. The different versions found suggest that Stealth Soldier is actively maintained as of January 2023.
Attribution
During CRP’s analysis, researchers found some overlaps in the infrastructure used in this operation with another campaign, Eye-On-The-Nile, which is aimed at targets in the North Africa region.
Eye on the Nile
The 2019 report by Amnesty International describes how Egyptian civilian organizations and individuals were targeted with sophisticated phishing attacks using third-party applications, such as Google and Yahoo, to steal sensitive information and monitor their activities. In a follow-up report Eye on the Nile, CPR uncovered the background of this operation, tracked its origin, and connected it to a surveillance-focused Android backdoor.
Throughout the analysis of Stealth Soldier campaigns, CPR was able to identify several infrastructure overlaps with Eye on the Nile ones.
Check Point Customers remain protected against the malware described in this report.
Check Point Threat Emulation provides comprehensive coverage of attack tactics, file types, and operating systems, and has developed and deployed a signature to detect and protect our customers against the threat described in this research.
Read the full research at: https://research.checkpoint.com/?p=28273









