Check Point Threat Emulation Finds “Joke-of-the-day” Chain Letter is No Joke
Summary
Check Point’s Threat Emulation Cloud Service recently detected an Excel document that runs a macro in order to change the computer’s background “as a joke”. Like other email chain letters, the message propagates when end users receive the document via email, open it, and then forward it to colleagues and friends at other organizations.
An analysis shows that while this document does not carry a malicious payload, it highlights how even today end users remain unwary of simple attacks, creating a ready distribution mechanism for a malware among many organizations.
Details
Detection of Suspicious Document in an Email Message
On October 28, a user working at a large manufacturer in France received an email message with the Subject title “Blagounette du jour”, or “Joke of the day.” Attached to the email message was a 6MB Microsoft Excel file (MD5: c82f970b3c5ec996d8a0bbd8949b016a).
This Check Point customer has configured their threat prevention gateway to send suspicious incoming documents to the ThreatCloud Emulation Service for analysis within a virtual sandbox. During emulation, the system detected that the Excel file
- Extracts an image from the Excel application into the computer’s file system, and
- Changes the registry to point the wallpaper key (HKCUControl PanelDesktopWallpaper) to the new image
As a result, the desktop’s wallpaper was changed to this new image; because the image is often perceived as humorous, the unsuspecting end user will be likely to share this “joke” by forwarding the email message friends and co-workers.
Further analysis of ThreatCloud data by the Check Point Malware Research Group reveals that this was exactly what happened, as the document was forwarded to at least three additional large French organizations.
Who Has the Last Laugh?
Fortunately for organizations that received this message and were not protected by Check Point Threat Emulation, this specific document did not carry a malicious payload and was not designed to cause any damage to the computers of the users who opened it. However, it includes all ingredients of a malware campaign intended to infect the computers of the target organizations with any variety of malicious content by running a VBA script that allows it to copy embedded content to the computer, change files, registry keys, edit the Hosts file, or make any number of other changes to the configuration and security of the computer. Users who opened this document exposed their computers and their organizations to a significant risk; and those who forwarded it to co-workers and to friends working at other organizations compounded this risk and became vector in the spread of a joke-of-the-day that was really no laughing matter from a security perspective.
It’s said that a joke is really two stories: the first story leads the listener to make an assumption; and the second story upsets that assumption. This particular email exploit could be considered a failed joke, in that it delivers exactly what it promised, a quick laugh at work thanks to an email from a friend. No organization should count on being so lucky, and that the ‘funny’ email their user assumes is harmless won’t actually deliver a malicious payload that leaves the IT security team crying while the attacker laughs all the way to the bank.
Recommendations for all organizations
- Disable “Microsoft Office Macros” for users who do not need to work with macros in their job function.
- Lock down the ability of end-users to personalize desktop images and screensavers.
- Educate users to beware of suspicious documents, and to be wary in particular of documents that ask to enable macros, empty documents, documents that minimize or crash Microsoft Office. In those cases users should consult with their IT security group, and of course not forward the message to other recipients.
- Enable internal and outbound filtering on email messages and attachments to prevent your organization from contributing to the spread of chain-letter emails.
Appendix
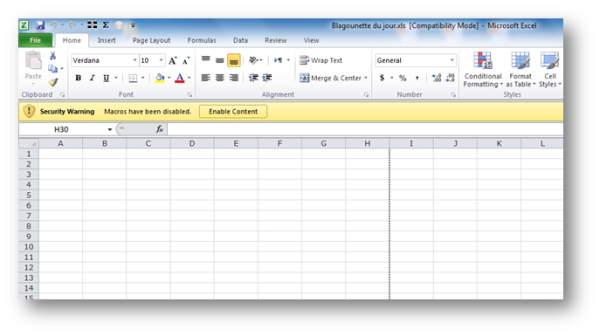
The below is an example of end-user view from a computer that opened the Excel file that changes the desktop’s wallpaper. This computer disabled macros by default.
- Note that the Excel spreadsheet has no contents, even though the file size was 6MB.
- By clicking “Enable Content”, the VBA scripts runs, copies an image to the computer and changes the wallpaper.