
Comparative Study Results on Linux and Windows Ransomware Attacks, Exploring Notable Trends and Surge in Attacks on Linux Systems
Highlights:
-
Evolving Landscape: Check Point Research (CPR) unveils a comprehensive study exploring the surge in ransomware attacks on Linux systems, drawing comparisons to their Windows counterparts.
-
Simplification Trend: CPR’s analysis reveals a notable trend towards simplification among Linux-targeting ransomware families. Core functionalities reduced to basic encryption processes, making these threats elusive and challenging to detect
-
Encryption Insights: A comparative examination of encryption techniques between Windows and Linux exposes a preference for ChaCha20/RSA and AES/RSA algorithms in Linux ransomware.
In a recent study conducted by Check Point Research (CPR), an in-depth examination of ransomware attacks on Linux and Windows systems sheds light on evolving trends in cyber threats. As ransomware attacks on Linux systems, particularly on ESXi systems, have seen a surge in recent years, CPR delves into the intricacies of these incidents, drawing comparisons to their Windows counterparts.
Historically, ransomware threats have predominantly targeted Windows environments. However, the landscape is evolving, with Linux-focused ransomware gaining momentum. CPR’s study analyzes 12 prominent ransomware families that either directly target Linux systems or possess cross-platform capabilities, allowing them to infect both Windows and Linux indiscriminately.
The release of the Babuk source code in 2021 has played a pivotal role in the proliferation of various ransomware families. What sets Linux-targeting ransomware apart is its relative simplicity compared to its Windows counterparts. Many of these Linux-focused threats heavily rely on the OpenSSL library, with ChaCha20/RSA and AES/RSA emerging as the most common encryption algorithms across analyzed samples.
Examining the historical evolution of ransomware, the first identifiable sample dates back to 1989, affecting Windows systems. It wasn’t until 2015, with Linux.Encoder.1, that Linux-specific ransomware gained traction. Despite the maturity of ransomware in Windows systems, the capabilities did not directly transfer to Linux until recent years, marked by a significant increase in attacks since 2020.
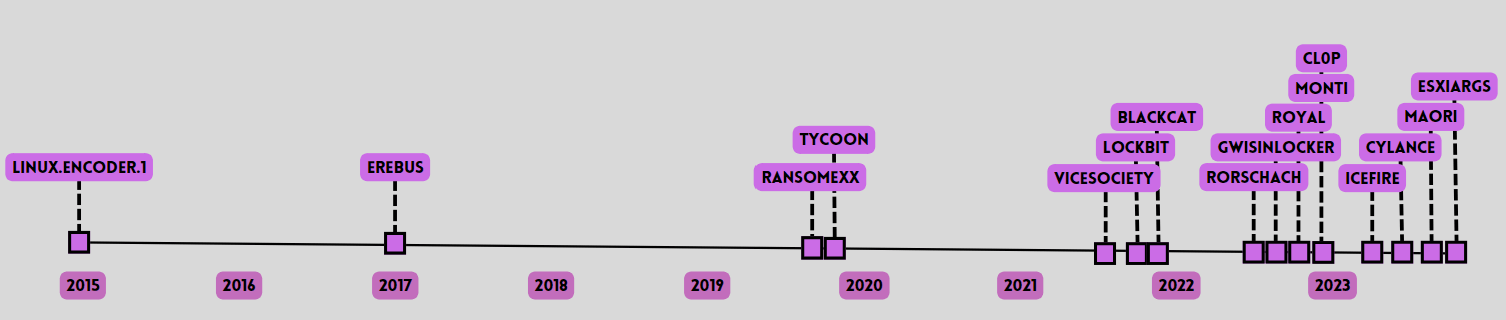
Figure 1 – Linux ransomware families.
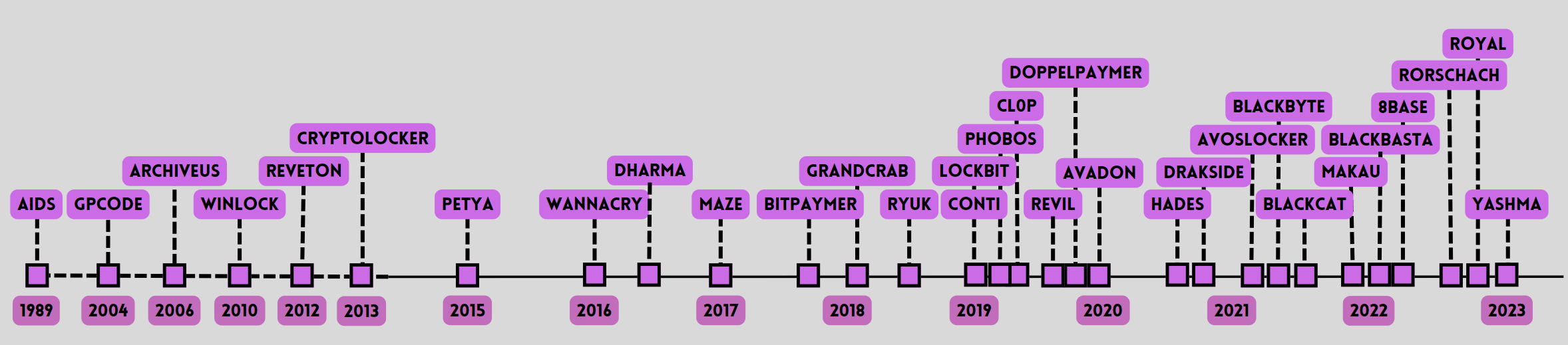
Figure 2 – Windows ransomware families.
CPR’s study uncovers a trend of simplification among Linux-targeting ransomware families. Core functionalities often reduce to basic encryption processes, relying heavily on external configurations and scripts, rendering them elusive and challenging to detect. The research also highlights distinctive strategies, particularly focusing on ESXi systems, and identifies vulnerabilities in exposed services as primary entry vectors.
Linux ransomware is strategically tailored for medium and large organizations
Linux ransomware diverges significantly from its Windows counterparts in terms of target and victim typology. While Windows is prevalent in personal computers and user workstations, Linux dominates certain server deployments. Linux ransomware primarily focuses on exposed servers or those within the internal network accessed by pivoting from Windows infections. This orientation indicates a clear trend—Linux ransomware is strategically tailored for medium and large organizations, unlike the more generalized threats posed by Windows ransomware. The distinctive internal structures of both systems also influence attackers’ approaches to folder and file selection for encryption, with Linux-oriented samples often avoiding critical directories to prevent system corruption. This underscores the targeted and sophisticated nature of Linux ransomware compared to its Windows counterparts.
Comparing encryption techniques between Windows and Linux systems, CPR reveals a preference for OpenSSL in Linux ransomware, with AES as a common encryption cornerstone and RSA as the primary asymmetric choice. This uniformity among different threat actors underscores the evolving landscape of cyber threats.
Check Point Customers Remain Protected Against Ransomware
Check Point customers remain protected against the threats covered by this research while using Check Point Harmony Endpoint , and Threat Emulation – which provide comprehensive coverage of attack tactics and file-types.
Check Point’s Anti-Ransomware, a Ransomware Protection solution protects organizations from the most sophisticated ransomware attacks, and safely recovers encrypted data. Anti-Ransomware is offered as part of Harmony Endpoint, Check Point’s complete endpoint security solution. Harmony Endpoint provides comprehensive endpoint protection at the highest security level
- Wins.HelloKitty.ta.D
- Wins.GwisinLocker.ta.A
- Wins.Clop.ta.I
- Wins.Royal.ta.B
- Wins.IceFire.ta.A
- Wins.Monti.ta.A
- Wins.ESXi.ta.B
- Wins.Babuk.ta.A
- Wins.LockBit.ta.AK
- Wins.BlackCat.ta.M
For a more detailed exploration of the comparative study on Linux and Windows ransomware attacks, readers are encouraged to visit the Check Point Research Blog for the full research findings.









