
COVID-19 Impact: Cyber Criminals Target Zoom Domains
While the world is struggling with the Coronavirus outbreak, many countries have implemented precautionary measures. Schools are being closed, communities are asked to shelter-in-place, and many organizations have enabled their employees to work remotely. As a result, video communication platforms are the daily norm. As the interest and usage of these platforms increases, cyber criminals stay a step ahead. For instance, Check Point Research recently discovered a technique which could have allowed a threat actor to identify and join active Zoom meetings.
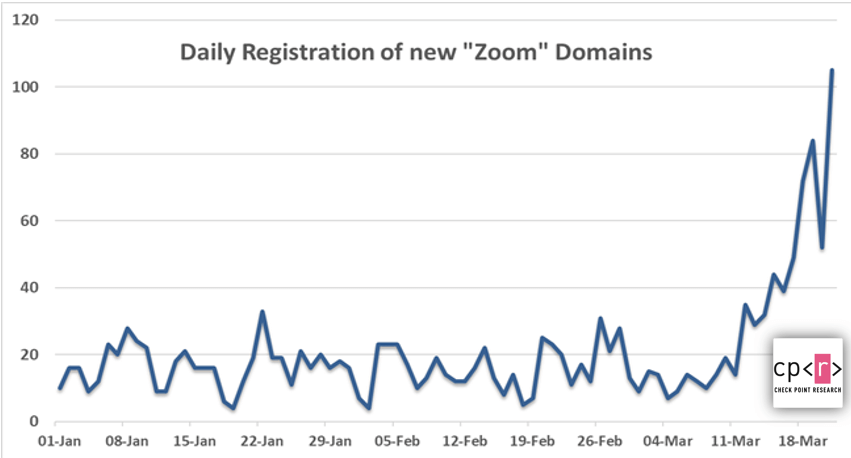
Online communication platforms have become essential for many households and organizations, but it is important to consider a few tips for a safe and secure Zoom experience. During the past few weeks, we have witnessed a major increase in new domain registrations with names including “Zoom”, which is one of the most common video communication platforms used around the world. Since the beginning of the year, more than 1700 new domains were registered and 25% of them were registered in the past week. Out of these registered domains, 4% have been found to contain suspicious characteristics. However, Zoom is not the only application targeted by cyber criminals. New phishing websites have been spotted for every leading communication application, including the official classroom.google.com website, which was impersonated by googloclassroom\.com and googieclassroom\.com.
Additionally, we have detected malicious files with names such as “zoom-us-zoom_##########.exe” and “microsoft-teams_V#mu#D_##########.exe” (# representing various digits). The running of these files leads to an installation of the infamous InstallCore PUA on the victim’s computer which could potentially lead to additional malicious software installation.
Staying safe
As business processes become virtual, safe browsing behavior is extremely important. Below are Check Point’s recommendations to help keep you protected:
- Be cautious with emails and files received from unknown senders, especially if they are offering special deals or discounts.
- Don’t open unknown attachments or click on links within the emails.
- Beware of lookalike domains, spelling errors in emails and websites, and unfamiliar email senders.
- Ensure you are ordering goods from an authentic source. One way to do this is NOT to click on promotional links in emails, and instead, Google your desired retailer and click the link from the Google results page.
- Prevent zero-day attacks with a holistic, end to end cyber architecture.
90% of cyber-attacks start with a phishing campaign. Are you doing enough to protect your organization’s attack vectors? Read the whitepaper Humans are Your Weakest Link to discover The daily risk of phishing emails







