Cryptomining to The Dark Side
Key Findings:
- A once legitimate video download software site, OSDSoft, has moved into crypto-mining.
- Around 6000 machines have been infected in just a few months.
- Distributed by a fraudulent Adobe Flash Player update service, the malware is mining $700 of Monero crypto currency for the perpetrator each day.
Check Point researchers have recently discovered a site that although once (almost) legitimate has now moved closer to the Dark Side.
Back in 2011, OSDSoft was a site offering its audience free video download software to thousands of users around the world. Registered under the name of Ivan Koslov, it also had Facebook, Twitter and YouTube accounts marketing the website’s main and only product. It was to all intents and purposes a legitimate site.
In 2014 however, OSDSoft started to appear in more suspicious contexts as several Adwares and Potentially Unwanted Programs (PUPs) downloaded from it were spotted in the wild.
These adwares and PUPSs acted stealthily in order to evade regular anti-virus protections and performed environment checks to make sure they were not running on a virtual machine. It seems though that these PUPs and software bundles were only the beginning of this increasingly malicious campaign.
Ivan Darker
Towards the end of 2017, as the popularity of crypto currency miners grew, OSDSoft shifted some of its efforts toward mining the Monero crypto currency. As discussed on this blog previously, Monero cryptominers are becoming more popular due to the increased anonymity they provide and the profitability of mining Monero on regular PCs.
After some analysis, the Check Point Research team estimates that around 6000 machines have so far been infected and are earning the perpetrator behind OSDSoft approximately $700 per day from this mining operation alone. This stands out from other similar operations by infecting so many machines in a matter of months and spreading these PUPs for so many years.
How is OSDSoft’s Cryptominer Distributed?
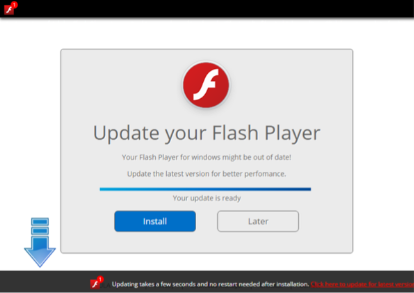
The miners are currently distributed by websites disguised as a legitimate Adobe Flash Player update service, telling the victim that their Flash version is outdated. Clicking anywhere on the screen would result in the malicious executable being downloaded. OSDSoft’s author does not want to waste any time in this campaign either, for while waiting for the Monerominer to download, the malignant websites additionally use the CoinHive cryptomining malware to mine through the browser and maximize his profits.
Fake Adobe Flash Player update service that distributes the cryptominer.
Furthermore, it is interesting to note that in this and other connected campaigns, it is legitimate hosting and file storage services such as AWS (Amazon Web Services), Dropbox and Github, that are being used to store and distribute the malicious cryptomining samples.
Victims are then directed to misleading malicious Flash Player domains such as flash2update[.]xyz, flashdownload[.]club, flashplayers[.]club and others via malvertising and referrals from shady websites.
Summary
Lately, security vendors are becoming more aware of the threat that PUP files pose and are increasingly treating them as malware. Dangers of a PUP can range from data theft and hijacking user traffic to possible remote code execution, as we have seen with our previous Fireball research.
OSDSoft, a website that started with seemingly innocent intentions serves as a case study in the need to be on constant alert. Although its author initially promoted video download software, the lure of high value crypto currencies lured him over to the dark side as the site became a PUP and cryptomining distribution platform.
For full technical details of this crypto-miner, please visit the Check Point Research blog.