
Cyber Stakes: The MGM Ransomware Roulette
What we have learned and the steps to protect your enterprise
Highlights
-
MGM Resorts was hit by a major ransomware attack that took systems offline in locations across Las Vegas
-
Prolific ransomware group ALPHV claimed responsibility in a post published on its Dark Web site
-
Organizations must take action to remain protected against ransomware and other attacks
What happened?
On the 12th of September 2023, MGM Resorts was reportedly subjected to a ransomware attack that took multiple systems offline at some of its major locations in Las Vegas. The attack left guests locked out of their rooms and unable to transact both on site and through the MGM mobile app. Eventually the affected casino hotels had to process transactions manually. It is expected that this incident will have a material effect on its operations as it continues to deal with the fallout.
At the time of reporting the incident, it was unclear who was behind the campaign, although there was speculation circulating on social media platforms. What we now know is that prolific ransomware group ALPHV has confirmed responsibility, publishing a statement on their Dark Web website in a move that marks the first time the group has publicly disclosed their involvement in an attack.
In the statement, they discuss how they infiltrated MGM Resorts on the 11th of September after many attempts to reach out to them. They have not confirmed what PII (Personally Identifiable Information) has been exfiltrated while they continue negotiations with MGM. However, they stated they will notify external sites such as HaveIBeenPwned.com if conversations with MGM do not lead to a resolution in their favor. You can read the full statement below.
ALPHV and the rise of Mega Ransomware
Like many established ransomware groups, ALPHV has evolved to become a well-organized operation carrying out large-scale attacks on high profile companies.
ALPHV (also known as BlackCat) is a ransomware-as-a-service (RaaS) threat actor that emerged in late 2021. It is known for using the Rust programming language and has capabilities to attack Windows and Linux-based operation systems. ALPHV is marketed on cybercrime forums and operates an affiliate program. Some affiliates have targeted organizations in a variety of industries, including healthcare, manufacturing, and government. The group has been known to leak stolen data if its ransom demands are not met and operates several Dark Web blogs for this purpose.
ALPHV is one of the major RaaS threat groups, responsible for almost 9% of all published victims in the past 12 months on Dark Web shame sites, preceded only by cl0p and Lockbit.
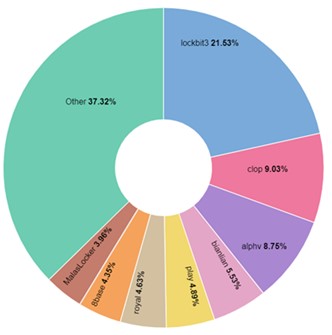
Figure 1 – Double extortion victims by threat actor, last 12 months
In the last 12 months, ALPHV published the identity of around 400 of its victims who refused to pay the ransom. The geographical distribution of its victims is typical of the ransomware ecosystem, with more than half based in the USA.
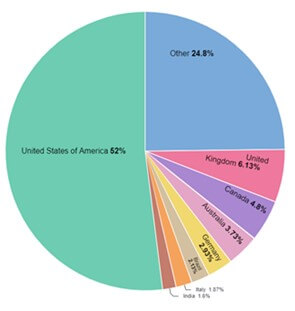
Figure 2 – ALPHV victims by Country, last 12 months
In August 2023, Check Point Research observed 918 average weekly cyberattacks per organization in the leisure/hospitality industry globally, with 396 occurring in the US. It was the 11th most attacked sector in H1. ALPHV has targeted victims across multiple sectors including manufacturing, healthcare and legal.
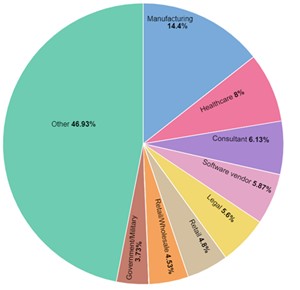
Figure 3 – ALPHV victims by sector, last 12 months
Sergey Shykevich, threat intelligence group manager at Check Point Research said: “This incident is yet more proof of the growing trend of ransomware attackers focusing on data extortion and targeting of non-windows operating systems. The model of ransomware as a service (RaaS) continues to be very successful, combining strong technological infrastructure for the attacks, with savvy and sophisticated affiliates that find the way to penetrate major corporations.
We can only speculate on what their next move may be, but what we do know is that organized groups like ALPHV are not afraid to publish data if their demands are not met. Regardless of their decision, MGM should keep hotel guests and visitors informed on what information may have been obtained. It is another cautionary tale for all organizations to regularly check their access controls and make sure they have end to end security processes in place.”
Summary of ALPHV GROUP STATEMENT :
A detailed statement was posted by notorious hacker group, ALPHV claiming responsibility for a widespread ransomware attack on MGM Resorts International, “MGM”, which led to MGM shutting down computers inside their networks as a result.
Claiming that no ransomware was initially deployed prior to the takedown of MGM’s infrastructure, ALPHV claim to have infiltrated MGM’s network since Friday, and had been monitoring MGM’s Okta Agent servers, with the aim of securing users’ passwords which could not initially be cracked. This led to the complete lockdown of MGM’s Okta environment by MGM themselves. However, ALPHV claim to “continue having super administrator privileges to MGM’s Azure tenant” despite MGM’s attempts to evict them. In what seemed like an uncoordinated response, MGM implemented conditional restrictions on their Okta environment, citing “inadequate administrative capabilities and weak incident response playbooks.” Network access issues persisted on Saturday due to MGM’s “network engineers’ lack of understanding on how the network functions”, which prompted MGM to “take offline” important components of their infrastructure, on Sunday. A day later, ALPHV then ‘successfully launched ransomware attacks against more than 100 ESXi hypervisors, despite the presence of external firms brought in to contain the attack. After attempts to reach out to MGM (even with a special link provided to prevent IT team access) were met with silence, ALPHV claim an unidentified user (unclear if this was authorized by the MGM leadership) surfaced in their MGM victim chat, visiting the chat room intermittently.
Assuming this user was from MGM, a threat was issued of posting a statement on the cyberattack, that was met with continued reluctance of a reply.
To prevent data leaks, ALPHV added a password allegedly made up of combined passwords of two senior MGM executives, to the link containing the exfiltrated materials, which allowed these two executives to view the files, together with employee IDs, for identification purposes.
Threatening that they had already secured PII information which would be notified to Troy Hunt from HaveIBeenPwned.com if there was no further response from MGM, the group then accused MGM of greed, incompetence and corruption, citing ‘insider trading behavior” as evidence of the company’s alleged disregard for customer privacy, encouraging the hotel’s
customers to choose other options instead.
The group also disputed rumours of teenagers from the US and UK for being responsible for the attack, calling for cybersecurity firms to provide solid evidence to support such claims, after criticizing outlets like The Financial Times for false event reports on their tampering of MGM’s slot machines.
They also denied prior claims of responsibility for attacks before this point, and suggest that this disclosure was instead made by unhappy employees or outside cybersecurity experts prior to their own disclosure.
They ended by claiming continued access to ‘some of MGM’s infrastructure” without any further details, threatening further attacks “if a deal is not reached” instead urging MGM to contact them
Check Point Customer using Harmony Endpoint and Anti Ransomware remain protected against such ransomware threats
Practical advice: Preventing ransomware and other attacks
Against a backdrop of advanced cybersecurity tools, organizations need to exercise good security hygiene across on-premise, cloud and hybrid networks all the way up to the board level. There are several actions that leaders can take to minimize exposure to and the potential impacts of an attack.
Here are a few simple tips to keep you safe:
- Robust Data Backup
The goal of ransomware is to force the victim to pay a ransom in order to regain access to their encrypted data. However, this is only effective if the target actually loses access to their data. A robust, secure data backup solution is an effective way to mitigate the impact of a ransomware attack.
- Cyber Awareness Training
Phishing emails are one of the most popular ways to spread ransom malware. By tricking a user into clicking on a link or opening a malicious attachment, cybercriminals gain access to the employee’s computer and begin the process of installing and executing the ransomware on it. Frequent cybersecurity awareness training is crucial to protecting the organization against ransomware, leveraging their own staff as the first line of defense in ensuring a protected environment. This training should instruct employees on the classic signs and language that are used in phishing emails.
- Up-to-Date Patches
Keeping computers up-to-date and applying security patches, especially those labelled as critical, can help to limit an organization’s vulnerability to ransomware attacks as such patches are usually overlooked or delayed too long to offer the required protection
- Strengthening User Authentication
Enforcing a strong password policy, requiring the use of multi-factor authentication, and educating employees about phishing attacks designed to steal login credentials are all critical components of an organization’s cybersecurity strategy.
- Anti-Ransomware Solutions
Anti-ransomware solutions monitor programs running on a computer for suspicious behaviors commonly exhibited by ransomware, and if these behaviors are detected, the program can take action to stop encryption before further damage can be done.
- Utilize Better Threat Prevention
Most ransomware attacks can be detected and resolved before it is too late. You need to have automated threat detection and prevention in place in your organization to maximize your chances of protection, including scanning and monitoring of emails, and scanning and monitoring file activity for suspicious files. AI has become an indispensable ally in the fight against cyberthreats. By augmenting human expertise and strengthening defense measures, AI-driven cybersecurity solutions provide a robust shield against a vast array of attacks. As cybercriminals continually refine their tactics, the symbiotic relationship between AI and cybersecurity will undoubtedly be crucial in safeguarding our digital future.









