
Five business use cases for evaluating Azure Virtual WAN security solutions
Are you using Microsoft Azure Virtual WAN, or considering using it?
If so, what is the best way to secure your Virtual WAN deployments?
This is not a trivial question, because not all firewalls are equal or even similar in terms of their ability to protect their customer, future-proof their business growth and meet operational requirements.
To help organizations who are evaluating security solutions to protect their Virtual WAN deployments, this article considers five business use cases and explains how Check Point enhances and complements Azure security with its best-of-breed, enterprise-grade cloud network security.
Background
More and more organizations are using public clouds. According to ESG, organizations using infrastructure as a service (IaaS) report a majority (55%) of their production applications and workloads now reside in public clouds. This was expected to increase to 62% by the end of 2023.
Azure Virtual WAN is a popular networking service. It enables a global “hub-and-spoke” transit network architecture, where the cloud hosted network “hub” enables transitive connectivity between endpoints that might be distributed across different types of “spokes” (including on-premises sites and branch offices, remote users and virtual networks), and traffic is routed through the Microsoft global network. Virtual WAN is well suited for enterprise customers, especially those with diverse, distributed, and heterogeneous IT environments.
A key component of every Virtual WAN deployment is how best to protect its data, workloads and assets. A foundational layer is cloud network security, where organizations should deploy virtual security gateways to provide advanced threat prevention, traffic inspection and micro-segmentation. Such security solutions use multiple layered security technologies including Firewall, IPS, Application Control, DLP and others. Cloud network security solutions enables broad risk mitigation with the greatest ROI and cost/benefit.
Azure Virtual WAN customers may choose Microsoft’s cloud network security solution because they perceive it easy to use and scale due to the native integration into the Virtual WAN hub, and also because of the ease of purchasing and bundling Azure security together with Virtual WAN and other Azure services.
However, there are business scenarios where organizations prefer to enhance and complement Azure security with recognized cybersecurity vendor solutions, to achieve enterprise-grade cloud network security and secured connectivity.
Five business use cases
1: Extending on-premises network security to the cloud
Organizations with on-premises network security, in the form of Next Generation Firewalls (NGFWs) or security gateway appliances, prefer to extend their existing security posture to the cloud, for reasons of consistency, to maintain compliance with regulatory requirements, to mitigate risk, and to maximize operational efficiency.
Recommendation:
The obvious choice for these organizations is to use the same security solution from their on-premises network security vendor, assuming it is easily available as a cloud firewall. They will receive the same level of security effectiveness without hiring new security engineers and with minimal training of the existing security team, contributing to lowest Total Cost of Ownership. They are also confident with their existing vendor’s ease-of-use, UI, and support. Most importantly, their security policies are now consistent between their on-prem and Azure Virtual WAN and other cloud deployments, minimizing organizational risk.
2: Organizations sensitive to security risk
Some organizations are especially sensitive to security risk, especially in financial services, healthcare, government and public sector, energy and utilities, and retail and e-commerce. Even outside of these verticals, most companies have critical business applications and assets that are essential for the success and sustainability of the organization. The IBM Cost of a Data Breach report states the global average cost of a data breach in 2023 was USD 4.45 million, and 82% of breaches involved data stored in the cloud.

Cost of a data breach by industry, in USD millions (source: IBM)
Recommendation:
Some organizations believe their security is good enough, until they realize it is not.
In other words, not all firewalls are equal or even similar in terms of their ability to protect their customer.
Organizations should choose cloud network solutions with the highest industry catch rate of malware and other threats, especially for their critical business applications. (For non-business critical applications, they may choose to use less-recognized solutions and take the chance they won’t get breached.)
3: Multi-clouds and hybrid-clouds
This article is focused on Azure Virtual WAN; however, it is clear that organizations are embracing multi-cloud. According to the 2024 State of the Cloud report by Flexera, 89% of survey respondents use more than one cloud, with the majority using multiple public clouds and multiple private clouds.
And if an organization is using a single cloud provider today, this may change in 6 months or a year because of M&A activity, new direction from the board of directors or even new cloud pricing models.
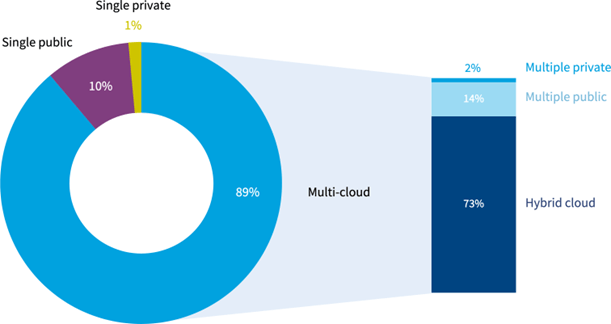
Source: Flexera 2024 State of the Cloud Report
Recommendation:
Organizations using multi-clouds or hybrid clouds should choose a security solution that provides consistent and efficient management of cloud network security over their entire IT infrastructure, preferably from a single pane-of-glass management console.
And organizations with single clouds are strongly recommended to “future-proof” their cloud security by investing in hybrid-cloud network security solutions.
4: Security teams want efficiency and ease-of-use
The global shortage of security engineers leaves many organizations with overworked and overwhelmed security teams with limited bandwidth, and who desire efficient solutions with high ease-of-use.
Recommendation:
This overload is often caused by multiple “point” solutions that are not integrated together, influencing the recent preference for established security vendors with integrated security platforms. Organizations should focus their efforts on established and well-respected security vendors with solutions that have been fine-tuned by customer needs and requirements over many years. One vendor with one platform is always better than multiple vendors and/or multiple different solutions, interfaces and processes.
5: Analyst recommendations
According to CCGroup, “On average, 61% of cybersecurity technology purchases now involve industry analysts. And that number is even higher in the United States, at 65%.” Additionally, many organizations are required to provide analyst justifications for their decision-making.
Objective third-party testing labs also provide valuable insight into quantitative differences between the effectiveness of different network security solutions in various threat prevention areas, including IPS, Anti-Malware, Zero-Day Protection, and other advanced threat prevention technologies.
Recommendation:
Organizations evaluating cloud network security solutions can benefit from industry analyst recommendations and lab testing results for several reasons, including their objective evaluation, expertise and insight, market intelligence and industry credibility. Some valuable reports include the Gartner® Magic Quadrant™ for Network Firewalls, Forrester® Wave™: Enterprise Firewalls, Forrester Wave™ for Zero Trust Platform Providers, Miercom Next Generation Firewall Benchmark, and the GigaOm Radar for Cloud Network Security.
Check Point enhances and complements Azure security
Check Point CloudGuard Network Security protects thousands of Microsoft Azure customers. CloudGuard Network Security for Azure Virtual WAN was the first Microsoft partner security solution to be integrated with Azure Virtual WAN, and its security gateways are provisioned automatically into the Virtual WAN hub directly from Azure Marketplace using an Azure Managed Application.
When considering the five business use cases above, it is the ideal choice for existing CloudGuard customers who are planning or already using Azure Virtual WAN:
- Extending on-premises network security to the cloud: CloudGuard customers minimize organizational risk easily and intuitively, using the same security policies and increasing operational efficiency without the complexity of additional security solutions.
- Organizations sensitive to security risk: CloudGuard provides industry-leading cloud network security with the highest security effectiveness, and is the best choice for customers with critical business applications.
- Multi-clouds and hybrid-clouds: CloudGuard customers manage their on-prem, multi-cloud and hybrid-cloud security using Check Point unified Security Management from a single pane-of-glass, ensuring consistent visibility, policy management, logging, reporting and control.
- Security teams want efficiency and ease-of-use: Check Point testing shows CloudGuard is easiest to use over standard cloud network security use cases (time taken, number of mouse-clicks and number of menus navigated).
- Analyst recommendations: Check Point is recognized as a long-term leader by third-party analysts, including 23 consecutive years as a Leader on the Gartner® Magic Quadrant™ for Network Firewalls, with testing lab results showing the highest security effectiveness score with 99.8% block rate for malware, and 100% block rate for malicious URLs and phishing attacks.
Can your cloud network security do all that?
Additionally, if you’re a Microsoft Azure customer with a MACC agreement, you can purchase CloudGuard Network Security for Azure Virtual WAN on Azure Marketplace, and the purchase will contribute towards your Azure consumption commitment. Read more here.
Summary
This article assessed five common business use cases for Azure Virtual WAN customers who are evaluating Virtual WAN security solutions, and why CloudGuard Network Security is the best choice.
It is important to emphasize that in almost every business scenario, the attack surface is large and growing, and organizations need best-of-breed security solutions from industry-recognized security companies. According to ESG, “nearly two-thirds (61%) of respondents cite security efficacy ratings as a significant influence on their organization’s decision to purchase third-party network security tools for public cloud infrastructure.”
Please note that these use cases focus on business-level consideration and does not deep-dive into the technical advantages of Check Point’s solution for Azure Virtual WAN security. For more information, please reach out to your Check Point account team or channel partner, or contact us.
For additional insight into evaluating cloud network security solutions, download the Buyer’s Guide to Cloud Network Security to understand the top 10 considerations when evaluating and choosing a cloud network security solution, and the relative benefits of solutions provided by cloud providers and third-party security vendors.
Next Steps
To join a live webinar with Microsoft and Check Point about Azure Virtual WAN security:
- APAC: May 28 at 1pm HK/SG: Register here
- AMER+EMEA: May 28 at 8am Pacific, 11am Eastern, 4pm UK/Ireland, 5pm CEST: Register here
If you are in the process of planning your Azure Virtual WAN security, please schedule a demo and a cloud security expert will help to understand your needs.
To replay technical webinars about CloudGuard Network Security, please see here.
If you would like to schedule a personalized technical workshop around best practices for secure cloud migration, or CloudGuard Network Security, please fill in this form and a cloud security architect will contact you to discuss your concerns and schedule next steps.
Follow and join the conversations about Check Point and CloudGuard on X/Twitter, Facebook, LinkedIn and Instagram.









