
Getting started: Deploy Azure Virtual WAN security in just a few minutes
Introduction
Many organizations are transitioning to Azure Virtual WAN as their preferred networking service. Their objective is to reduce the operational effort required for connectivity and to reduce possible misconfiguration issues. However, the challenge they face lies with their need to secure this connectivity, without losing the benefits enabled by Azure Virtual WAN. To answer this need, Check Point recently announced the general availability of CloudGuard Network Security for Azure Virtual WAN.
The objective of this blog post is to help you with the quick and easy adoption of Check Point’s best-of-breed security natively into your Azure Virtual WAN hub, supporting the operational efficiency that you expect from Azure.
Meeting your security requirements
First, you should define your needs and the security use cases you want to address. Check Point’s CloudGuard Network Security for Azure Virtual WAN is a one-stop-shop for most security use cases:
- Network security: Consistently prevent advanced threats; gain full cloud visibility and control.
- Prevent lateral attacks: Reduce cloud attack surfaces and segment different parts of the organizational IT.
- Scale rapidly: The tight integration with Azure Managed Application enables quick automation, easy scaling and orchestration.
- Secure VPN Connectivity: Enable secure and centralized connectivity to additional parts of your networks.
- Unified Security Management console: Consistent visibility and control for public, private, hybrid and on-premises networks from a single pane-of-glass.
For more details, please read the launch blog post here.
Meeting your operational requirements
Now, let’s review the list of operational benefits you will receive from the native integration of CloudGuard with Azure Virtual WAN. We call it the “5 easy-tos” for operational simplicity:
- Easy-to-deploy – It takes under 30 minutes to deploy CloudGuard inside your Azure Virtual WAN hub. If you have are already using Check Point management, you can easily connect the new deployment. If not, it’s easy to use Check Point’s management-as-a-service solution.
- Easy-to-configure – The best practices configuration is automatically deployed for you. Advanced configurations may be applied using the UI or APIs.
- Easy-to-scale – The security gateways deployed into your Virtual WAN support dynamic changes in your traffic capacity (up to the maximum capacity you defined when creating the Azure Virtual WAN).
- Easy-to-consume – You pay for what you consume based on throughput only, transacted on Azure Marketplace.
- Easy-to-maintain – There are no resources to manage on your Azure account. Upgrading and updating the security gateways are simply “rip and replace”.
Getting started: How to deploy CloudGuard into Azure Virtual WAN
Account Setup:
If you have a Check Point account team or channel partner, please contact them for account setup. Otherwise, please use this link to submit your details and Check Point will contact you as soon as possible.
(Please note that there is no need to wait with your deployment until account setup is complete.)
Follow these steps in the Admin Guide to deploy CloudGuard:
- Select Check Point to secure your Virtual WAN:
- If you haven’t set up your Azure Virtual WAN, you can use these Azure instructions (in sections “Create a virtual WAN” and ” Create a hub”).
- Navigate to the offering of CloudGuard Network Security for Azure Virtual WAN on Azure Marketplace.
- Alternatively, you can use your Azure Portal to navigate to your “Azure Virtual WAN Hub/Security Configuration”.
- Deploy and configure the security gateways:
- Select your desired configurations, including Subscriptions, Virtual WAN Hub Capacity and Region.
- For an example of this process, see the onboarding video here.
- Connect to Check Point management
- If you are already using Check Point Management: Using Check Point Management, navigate to “GWs”. Click “Add a new GW”, and follow the steps in the Admin Guide to add secured, authenticated connectivity between your Check Point Management and the new security gateways.
- If you do not have Check Point Management, please set up Check Point’s management-as-a-service (see this document; you can refer to the Admin Guide and onboarding video).
- Setup security policy:
- If you have an existing security policy, you can just Install it.
- If you do not have a security policy, CloudGuard will automatically apply the best practices for advanced threat prevention; you can set your required access rules after the deployment is completed.
- Steer traffic to the security gateways:
- Go to the Azure Virtual WAN hub (see below) and configure Routing Intent and Routing Policies to steer the traffic you want to secure.
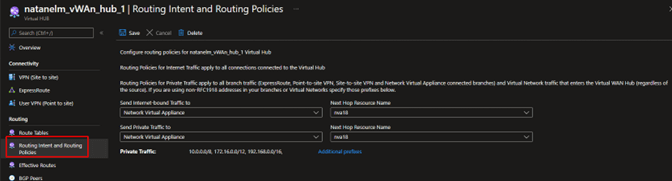
Set Routing Intent and Routing Policies to steer traffic to the security gateways (source: Microsoft)
Additional resources for getting started:
- Read the Admin Guide
- Watch the deployment demo video
- Advanced videos on CloudGuard Network Security for Azure Virtual WAN:
Congratulations!
You have now deployed Check Point CloudGuard Network Security into to your Azure Virtual WAN hub, and you can enjoy industry-leading Virtual WAN security with maximum operational efficiency.
Getting started: Next Steps
To read more about CloudGuard Network Security for Azure Virtual WAN, read the press release or visit the dedicated webpage.
To watch the Microsoft and Check Point joint customer pre-launch webinar, click here.
If you would like to schedule a deep-dive personalized workshop around CloudGuard or best practices for secure migration, please fill in the form here and a cloud security architect will contact you to discuss your needs and schedule next steps.
To see CloudGuard in action, please schedule a demo, and a cloud security expert will help to understand your needs.
If you have any other questions, please contact your local Check Point account representative or channel partner using the contact us link.
Follow and join the conversations about Check Point and CloudGuard on Twitter, Facebook, LinkedIn and Instagram.









