
Is Your Peloton Attracting Security Threats?
A Deep Dive Into the Vulnerabilities Found In America’s Largest Internet-Connected Exercise-as-a-Service Company.
Highlights:
- Check Point security experts unveil vulnerabilities found in internet-connected workout equipment such as Peloton.
- Exploiting these vulnerabilities could potentially grant threat actors access to user databases, exposing sensitive data of Peloton users.
- The research findings were responsibly disclosed to Peloton.
Amidst the increasing popularity of internet-connected gym equipment, such as the widely known Peloton Treadmill, a new concern arises regarding potential security threats. As fitness enthusiasts embrace the convenience and connectivity of these advanced workout machines, it becomes imperative to explore their potential vulnerabilities. Internet-connected workout equipment, including the Peloton Treadmill, carries the possibility of posing security risks. The widespread usage of these machines raises the likelihood of them becoming prime targets for malicious hackers who aim to acquire sensitive information or cause deliberate harm.
Driven by my passion for cybersecurity, I conducted an investigation to explore the security vulnerabilities associated with internet-connected workout equipment. My exploration into the security vulnerabilities of internet-connected workout equipment led me to the realization that awareness of non-typical ways to compromise IoT devices is crucial. As more and more devices become connected to the Internet, it’s vital to understand the potential risks involved and take steps to mitigate them.
In this blog post, I’ll discuss the most common security vulnerabilities found in internet-connected workout equipment based on my experience with the Peloton Treadmill. I’ll also provide tips on how to protect your devices from potential attacks and explain why it’s essential to take these risks seriously. Whether you’re a fitness enthusiast or someone who’s concerned about cybersecurity, I encourage you to read on.
I’ll be discussing my findings based on three attack vectors: The OS, The Applications, and The Malware. All the findings mentioned below have been responsibly communicated to the corresponding Vulnerability Disclosure Program, and the engineering team will address them opportunistically.
The Operating System
The tested treadmill operates on the Android operating system, essentially making it an Android device. A few months ago, the operating system version was updated from Android 9 to Android 10. As of the time of writing this article, the treadmill’s current version is based on Android 10 with a build number of QT.22082.A. It’s important to note that the latest available Android version is Android 13, which implies that there could be potentially over 1100+ vulnerabilities from 2022 and 2023 alone that could theoretically be exploited to compromise this treadmill. ***.
- See image below of OS versions and build number.
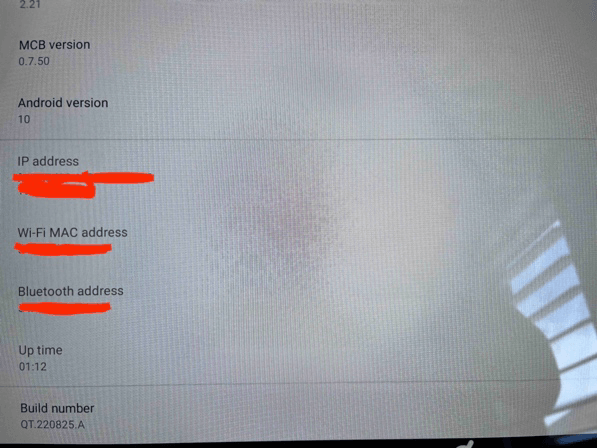
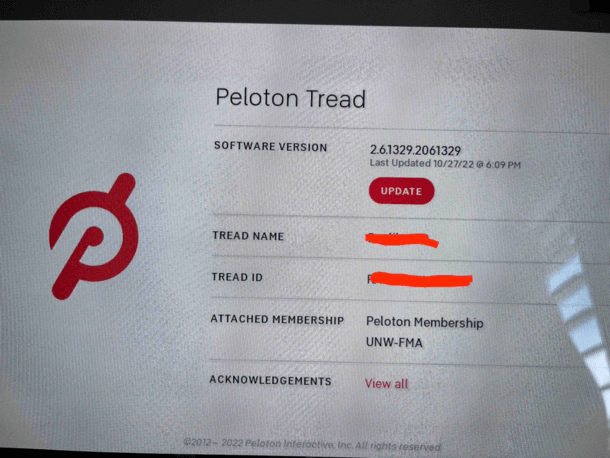
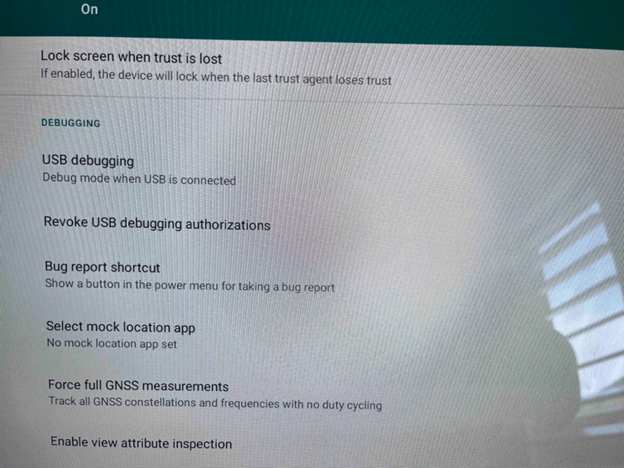
- Interestingly enough, a malicious actor could potentially enable USB debugging and gain access to the shell. Leaving USB debugging enabled increases the attack surface and is not recommended. ++++
admin@lossantos:~$ adb devices
List of devices attached
QAPLCS210929XXXX device
- You can also obtain a list of all installed packages (Please note that the complete list is not included here).
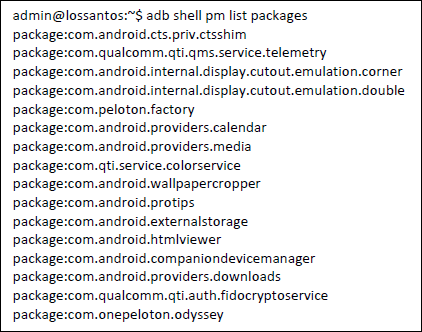
- The image below displays a selection of installed apps:
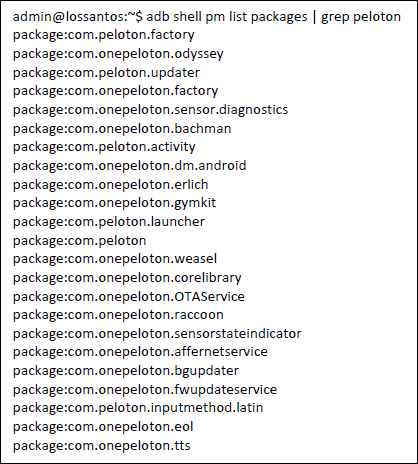
- Shell is fully accessible, which means that the application can be fetched for further security analysis. Cybercriminals could exploit vulnerabilities on apps and take advantage of the embedded binaries in /shell to make lateral movements. For instance, by using just ping**, a compromised treadmill could exfiltrate data. Additionally, the fact that applications are compiled using different versions of the SDK could make them even more vulnerable to exploitation.
![]()
Applications
As I explained before, apps can be fetched directly from the treadmill for further reverse engineering and other malicious purposes such as extracting secrets and discovering APIs vulnerabilities in the backend.
- Certain apps on the treadmill (not all of them) incorporate rooting detection mechanisms to prevent unauthorized software from running on non-approved hardware. While root detection is a basic security measure, it is well known that there are techniques, such as those based on Fryda****, able to bypass rooting detection. It means that a malicious actor could potentially use these techniques to discover more vulnerabilities within the apps in-runtime.
Below is an example of discovered root detection capabilities: 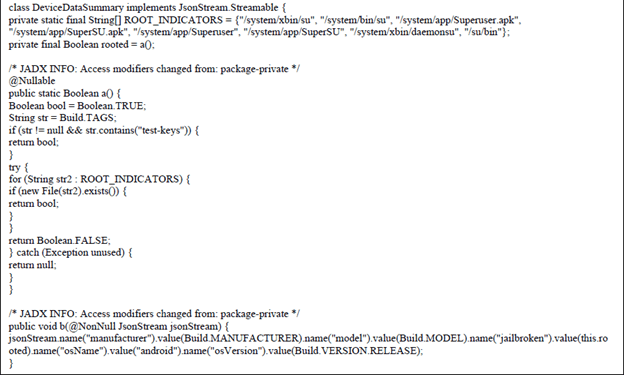
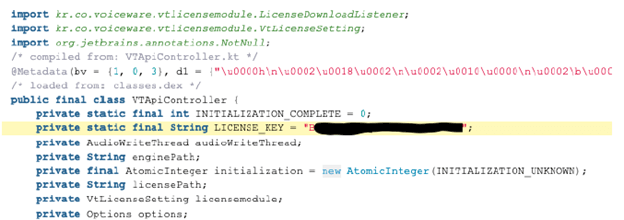
- During the testing, hardcoded sensitive information was discovered.
Text-to-Speech voice services are embedded, and during the development process, a license key was included in the code. However, storing sensitive information in cleartext is a security flaw(++). This means that a hacker could potentially misuse this key and abuse the service, which could have serious consequences such as Denial of Service
- We discover a number of unprotected services too, which means that non-Peloton apps running on the platform could escalate privileges and gain access to personal data (+++). For instance, malware could exploit this lack of security control to obtain tokens.
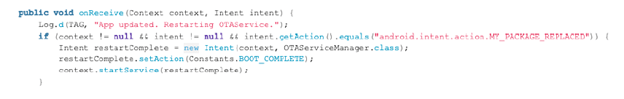
Another potential risk is a malicious app abusing broadcast receivers+++++. As an example, it could let the treadmill in an infinite loop that could potentially disable update processes. It would prevent vulnerability management and patching, fact that will facilitate keeping the treadmill under the malicious actor’s control.
- We identified differences in the signature scheme of the installed apps. While some apps, such as “com.peloton.launcher,” are signed with the latest signature scheme, others, such as “com.onepeloton.weasel.apk,” are only signed with version 1. Although Android 10 has measures in place to prevent attacks such as Janus#, this situation could potentially pose a risk in the future.
Malware
The treadmill operating system includes numerous standard APIs that can be exploited to execute Android code, allowing attackers to carry out nefarious actions from a networking perspective and take advantage of the device’s always-on nature. Moreover, the presence of a webcam and microphone makes the treadmill vulnerable to eavesdropping attacks if a malware is installed. Our team successfully compromised it, by sideloading a mobile remote access tool (MRAT), effectively turning it into a zombie IoT device that can be remotely controlled by a C&C center. The MRAT gave us full access to the treadmill’s functionalities, enabling us to record audio, take pictures, access geolocation, and abuse the network stack. With a compromised treadmill, we were able to acquire full access to the local area network and carry out any number of nefarious activities. For instance, we were able to capture the image below using the MRAT.

Now that we’ve covered the technical aspects, what comes next?
Let’s consider a scenario where a malicious actor targets a high-profile individual by compromising their treadmill. The attacker may use social engineering tactics, such as posing as a treadmill support representative, to gain access to the individual’s household or office. By claiming that there is an ongoing safety recall that requires immediate attention, the attacker can convince the individual to grant access. They may even wear vendor’s gear purchased online to add credibility.
Once access is granted, the attacker can quickly install a backdoor on the treadmill and gain access to the network. With this access, the attacker can carry out lateral movement, steal personally identifiable information, launch ransomware attacks, access corporate credentials, or perform a Denial-of-Service attack. Essentially, once the attacker has remote control over the treadmill, they have a significant advantage and can escalate their attack surface.
Since the compromised treadmill is difficult to detect, it is highly unlikely for investigators to suspect it as the source of the attack. Even if the compromised treadmill is discovered, the malicious actor may have already covered their tracks and accomplished their goal.
Therefore, this scenario highlights the need for proper security measures and awareness to protect against potential threats. With the increasing prevalence of Internet of Things (IoT) devices, it’s crucial to implement appropriate security protocols and remain vigilant to prevent attacks.
…GAME OVER…
Responsible Disclosure to Peloton
Once the risks were identified, Check Point alerted Peloton of their existence. Peloton provided the following statement:
‘At Peloton we are committed to providing top-level security of our systems. We have reviewed the reported issues and determined that they meet expected security measures for Android-based devices. The concerns raised in this report pertain to scenarios that require an attacker to have physical access to the device. We appreciate the opportunity to work with all security researchers and appreciate their willingness to observe our Coordinated Vulnerability Disclosure practices.’
Lessons Learned from Analysis
To ensure the security of your IoT devices, it is crucial to develop a comprehensive cybersecurity strategy. This involves gaining a thorough understanding of the software components of your devices, including your Peloton treadmill, and being prepared to mitigate cyber-attacks using non-standard methods. By taking these measures, you can effectively safeguard your personal data, prevent unauthorized access to your network, and minimize the impact of any cyber-attacks on your IoT devices.
Check Point offers Quantum IoT Protect, a comprehensive solution designed to enhance the security of IoT devices by addressing vulnerabilities and protecting against various cyber threats. This solution provides extensive protection against malware, botnets, DDoS attacks, and more, ensuring the integrity of IoT networks.
Quantum IoT Protect enables organizations to gain visibility into all connected IoT devices within their network and monitor their communications, both internally and externally. By leveraging learned profiles that understand the expected behavior of IoT devices, the solution establishes autonomous zero-trust access policies, allowing only necessary communications for normal IoT operations. Suspicious connection attempts that deviate from the expected behavior can be promptly detected and blocked.
Given the rapidly evolving landscape of IoT security, it is crucial to remain updated with the latest security trends and technologies to safeguard the reliability and safety of your IoT ecosystem. By implementing a robust IoT security solution like Quantum IoT Protect, you can proactively protect your organization against emerging threats, ensuring peace of mind, and enabling you to focus on your core business operations.
For more information about how Check Point can help secure your IoT/OT environment, head over to our IoT home page and get in contact.
References
* (CVE Details Android 10, n.d.)
** https://curesec.com/blog/article/blog/Exfiltrate-Data-using-the-old-ping-utility-trick-23.html
***https://www.cvedetails.com/product/19997/Google-Android.html?vendor_id=1224
**** https://frida.re/
++ https://cwe.mitre.org/data/definitions/312.html
+++ https://i.blackhat.com/asia-21/Thursday-Handouts/as-21-Johnson-Unprotected-
Broadcasts-In-Android-9-and-10-wp.pdf
++++https://learn.microsoft.com/en-us/mem/intune/user-help/you-need-to-turn-off-usb-debugging-android
+++++https://attack.mitre.org/techniques/T1624/001/
# https://research.checkpoint.com/2019/agent-smith-a-new-species-of-mobile-malware/









