
MemDive AI Engine Prevents Malicious Payloads from Evading Security Measures
By Asaf Avisar, Arie Olshtein and Shiri Yaakobson
Highlights:
-
In recent months, MemDive allowed our Threat Emulation engine to prevent various attempts of a shellcode-based packer, aiming to execute STOP ransomware and the RedLine Stealer.
-
Check Point customers using Quantum and Harmony products (with the engine activated) are now protected against this pernicious attack vector.
-
Check Point’s Threat Emulation engine allows users to send files to ThreatCloud AI for inspection. The Threat Emulation engine uses internet-connected sandboxes to prevent multi-stage attacks by analyzing the full infection chain. We’ve recently implemented an advanced approach to detect and preventing encrypted malicious payloads, which we call MemDive.
MemDive uses AI algorithms to dynamically extract the hidden malicious payloads out of process memory and run a static scan during runtime, within the isolated environment of the Threat Emulation engine. The model is trained based on executables, assembly code and binary data, to distinguish between malicious and benign samples. Previously, the Threat Emulation Engine primarily analyzed file structure and behaviorals. Now, by using this approach, malware that can evade static or dynamic monitoring can now be detected.
What is an encrypted malicious payload?
Attackers frequently employ encrypted malware payloads to elude detection and analysis by antivirus software, firewalls, and other security utilities. Unpacking or downloading encrypted payloads at runtime is a common technique to evade static detection methods.
Following this, to avoid dynamic detection the attackers employ additional steps to further obfuscate their malicious activities. One common tactic used by malware at run-time is to camouflage their malicious code within the context of legitimate processes, away from the watchful eyes of antivirus solutions or security monitoring systems. Another frequently employed method is decrypting and running a small piece of shellcode directly into memory, enabling the execution of a backdoor into the system.
How does MemDive work?
To counter such techniques MemDrive implements dynamic memory extraction which managed to prevent the payload even before it is having the chance to run, and even if the attacks delete forensic evidence out of the memory.
The new implementation continuously scans the system memory for any modifications or any signs of manipulation. It extracts from memory any modifications and manipulation, such as decrypted payloads, for thorough analysis. With this improved implementation, we are also exposing the status of file’s running process memory and we can reconstruct and repair the files using the Portable Executable format.
This approach of dynamic memory extraction significantly advances the state of the art in forensic memory scanning detection.
Case in point – dynamic memory extraction prevents evasive malware
In this case study we demonstrate an example of a real-life attack prevented at the first stage.
Dynamic memory extraction only filters the relevant sections exposed in memory at run time. With this extracted memory we are getting almost the original (pre-encryption) binary that was intended to be executed by the attacker. This allows much more effective identification of malicious content.
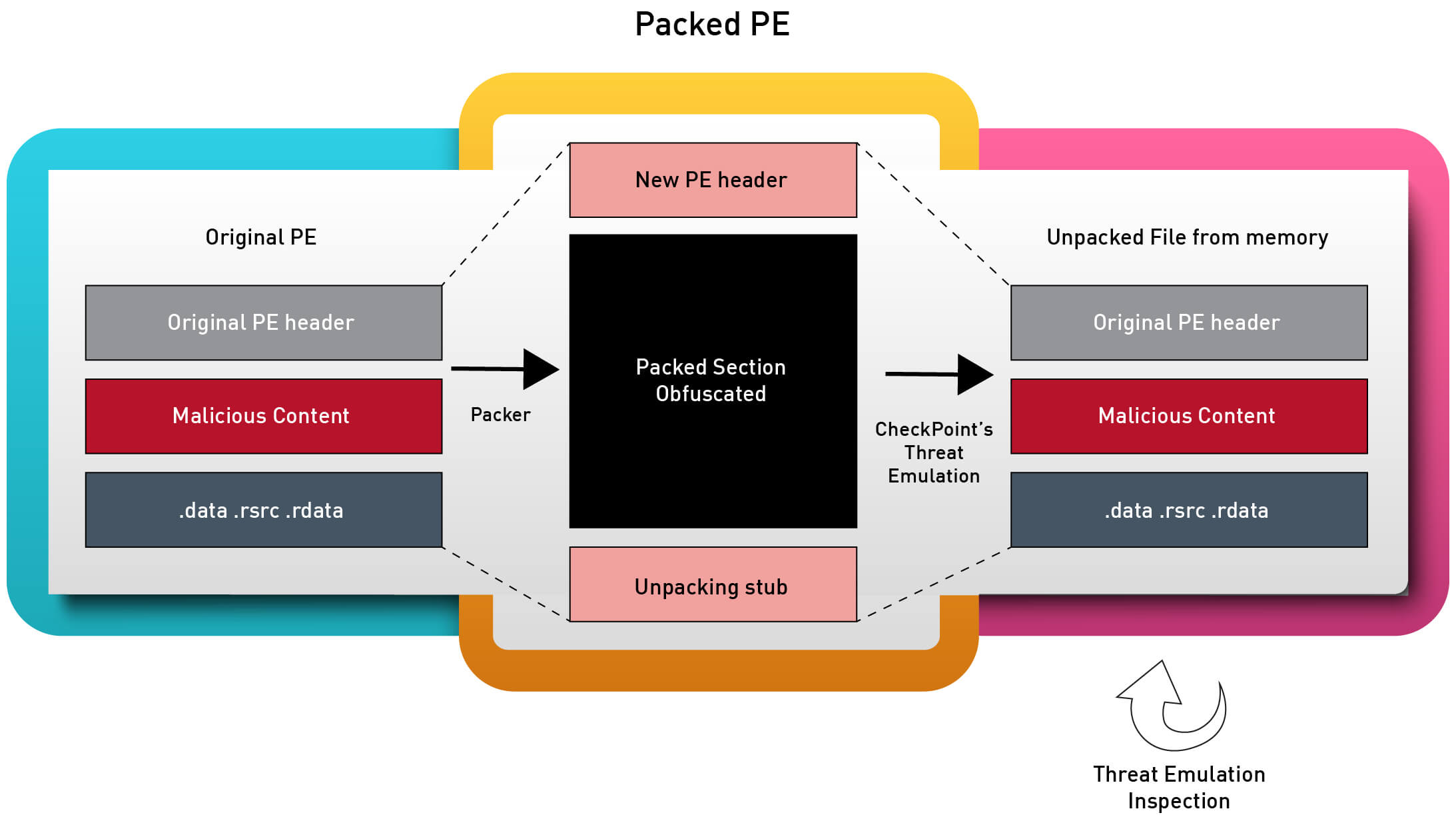
Figure 1 – memory extraction process
Between June and July 2023, MemDive allowed the Threat Emulation engine to successfully prevent multiple exploits using AceCryptor. AceCryptor involving memory, followed execution the shellcode for dynamically decrypting, loading, and executing the final malicious payload.
The payloads detected during this period were identified as either STOP ransomware (also known as KeyPass or Djvu) or the RedLine Stealer. Both malwares might not be detected by behaviors due to several evasion techniques.
This is how a section of AceCryptor’s shellcode appears in memory both before and after decryption. The snippet on the left is encrypted and contains invalid instructions. When the decryption routine runs at runtime, the malicious code becomes present in memory (on the right side of the image). This decrypted shellcode has been extracted using MemDive:
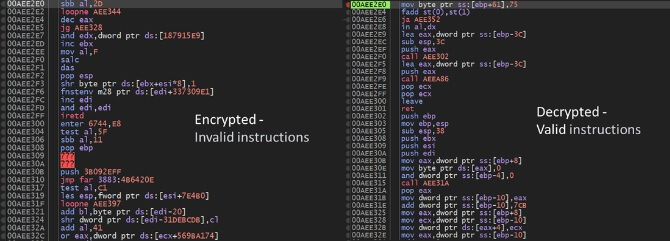
Figure 2 – before and after memory extraction
This is how a section of AceCryptor’s shellcode appears in memory both before and after decryption. The snippet on the left is encrypted and contains invalid instructions. When the decryption routine runs at runtime, the malicious code becomes present in memory (on the right side of the image). This decrypted shellcode has been extracted using MemDive. As you can see, the code is completely different after encryption.
Check Point customers using Quantum and Harmony products (with the Threat Emulation activated) are now protected against this pernicious attack vector.
Schedule a free demo of Check Point Quantum , the new release of Check Point’s cyber security platform, revolutionizes threat prevention









