
New ThreatCloud AI engine designed to prevent IPFS attacks
By Adi Babai
In the ever-evolving landscape of cyber threats, the rise of decentralized technologies, particularly the Interplanetary File System (IPFS), has ushered in both challenges and opportunities for attackers. In this blog post, we embark on a journey into the realm of IPFS phishing attacks, shedding light on their intricacies and how they work. We will also show how Check Point’s new ThreatCloud AI engine can prevent IPFS attacks and safeguard users in this decentralized frontier.
Understanding IPFS
The Interplanetary File System (IPFS) is a decentralized networking protocol, which was designed to enhance the speed and openness of the web by eliminating the need for central servers. IPFS employs a peer-to-peer network for the distribution and retrieval of files, websites, applications, and data (figure 1). Each piece of content carries a unique identifier (CID), which allows it to be accessed via a global namespace. Any computer worldwide can become a host by downloading the IPFS software.
Despite its numerous advantages, IPFS introduces a fresh avenue for cyber threats. IPFS phishing attacks are emerging as a novel and growing menace, capitalizing on users’ unfamiliarity with decentralized systems.
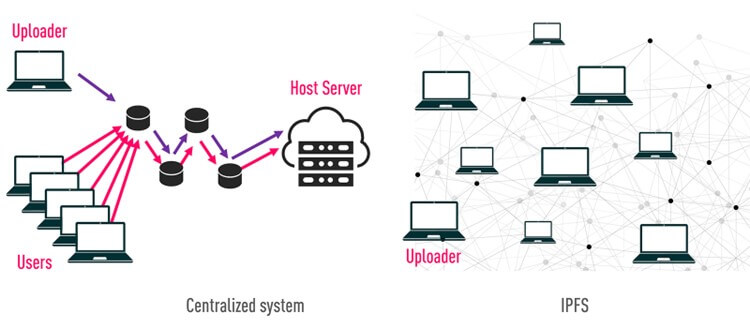
Figure 1 – IPFS vs centralized systems
What distinguishes IPFS attacks from traditional phishing attacks?
Like traditional phishing methods, IPFS attacks aim to manipulate users into divulging sensitive information. However, a distinctive twist lies in the attackers’ use of the IPFS protocol to host deceptive websites across a distributed network of nodes. This decentralized structure poses a formidable challenge for security solutions because it complicates the detection and mitigation of such attacks.
How IPFS Phishing Attacks Work:
- Domain Spoofing: Attackers create a malicious website that closely mimics the appearance of a legitimate site, often using cloned content, logos, and designs.
- IPFS Hosting: The attacker then uploads the fake website’s content to the IPFS network, obtaining a unique content-based hash that serves as the site’s address.
- Propagation: The malicious IPFS address is shared through various channels, such as phishing emails, social media, or messaging platforms, luring users to click on the link.
- User Interaction: When users click the link, their web browsers retrieve the content from the IPFS network and display the fake website, which appears genuine to the user.
- Data Harvesting: Users are prompted to enter sensitive information like login credentials, credit card details, or personal information. In some cases, the username has already been written in the username field (as it sent via the email address). This data is then captured by the attacker.
- Exit Scan: After collecting enough information, the attacker may suddenly take down the malicious IPFS content, leaving victims with no recourse for tracking or recovering their stolen data.
IPFS site addresses usually have a common :
- IPFS gateway
- Content ID – unique ID for the malicious site.
- Dynamic email parameter – the user’s email, uses as Username. This is not a mandatory parameter.
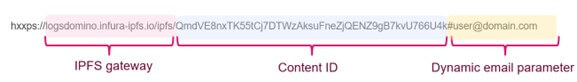
Figure 2 – IPFS Site’s address
New ThreatCloud AI Engine prevents IPFS attacks
Check Point introduces a new engine to ThreatCloud AI, designed to prevent IPFS attacks. The engine scans the URL and detects suspicious IPFS patterns and by combining other phishing indicators prevents the malicious .
Case study: IPFS attack blocked by Check Point IPFS new :
In the 2nd week of September, an email with a similar format was sent to Check Point email customers:
Email subject: “unread inbox messages”
Sender: test@it-supporting.com
The email body included a link with a similar structure, with the only difference being the username and the domain at the end of the link (figure 3):
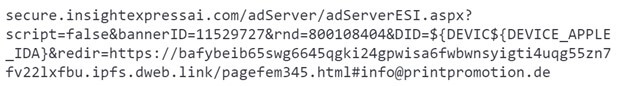
Figure 3 – Link with a similar structure but different username and domain
How does the attack work?
First, when the user clicks on the link, they were redirected to the following web page, with a login popup that already included the username:
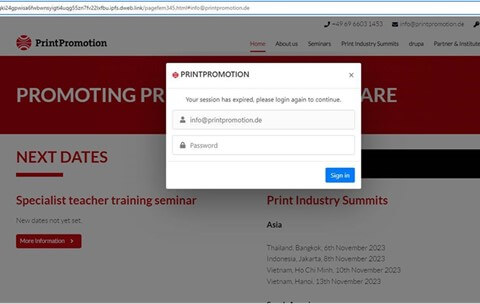
Figure 4 – Login popup including user name
The login popup and the web page behind are derived from the dynamic email parameter that is concatenated to the end of the link – #info@printpromotion.de. This parameter is not but makes the attack more personal.
The site address included the IPFS gateway and a content ID that is unique to this attack (figure 5):

Figure 5 – Site address includes hashed content ID
The same content ID can be used on different IPFS , which makes it harder to block the attack with signature-based .
The domain can be easily replaced by any other genuine domain – the page and the login window will be replaced accordingly (figure 6). For example:
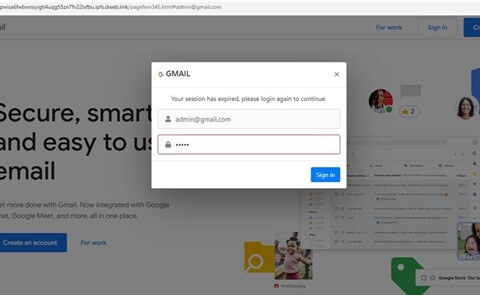
Figure 6 – Changing the domain to another official domain
Since the login window appeared to be related to the original web page behind, the user may have thought that they were logging on to the original page and entered their password.
Once the user typed the password, it was sent to the attacker and the sensitive information was revealed immediately (figure 7):
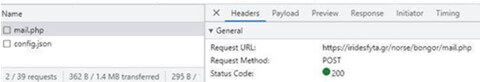
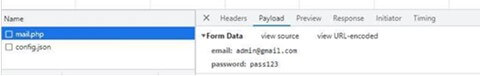
Figure 7 – The sensitive information is revealed to the attacker
This attack was successfully blocked by the new IPFS engine to all of Check Point’s customers.
Check Point customers using Quantum and Harmony products are now automatically protected against this kind of attack, With Check Point’s new ThreatCloud AI engine for prevention of IPFS attacks.
ThreatCloud AI boasts an array of over 40 engines, each infused with AI-based functionalities and capabilities. ThreatCloud AI makes 2 billion security decisions daily, ensuring comprehensive, consolidated and collaborative protection to our customers, across cloud, mobile, network, endpoint and IoT.









