
Preventing DNS Tunneling with AI Deep Learning
DNS Tunneling is probably considered a relic of the early Internet days, back when the first firewalls were deployed and malware analysis was a little bit simpler than it is today.
Though attackers have evolved, using steganography and encryption to communicate over HTTP, DNS Tunneling is not obsolete. In fact, modern malware actors continue to engage in DNS Tunneling, as evidenced by the CoinLoader infections, first reported by Avira. Even today, we see new uses of DNS Tunneling by hackers. In fact, our analysis of DNS Tunneling confirms threat actors are still using this technique, including state-sponsored actors and cybercriminals.
As security vendors, it’s important to spend time guarding against all attack forms, no matter how common or uncommon they might be. Just one successful attack—phishing, ransomware, DNS tunneling with exfiltration of sensitive data or otherwise—can cause untold damage. This year, we launched DeepDNS, an artificial neural network that hunts and blocks campaigns abusing DNS.
This engine is an integrated part of ThreatCloud AI, which trained on a huge amount of DNS traffic.
Another engine protects against DGA technique – Domain Generation Algorithm that is commonly used by attackers in the first communication to the command-and-control infrastructure. DGA means the domain is generated by the infected host and registered by the attacker at the same time, thus bypassing traditional domain reputation services because these are newly seen domains.
Both techniques represent anomalies either in the domains or the subdomains, where ThreatCloud AI scans and flags them as malicious in seconds.
When tested, the DNS Security engines were able to prevent 5x more zero-DNS attacks than traditional DNS solutions, and 47% more detection compared to AI-based security vendors.
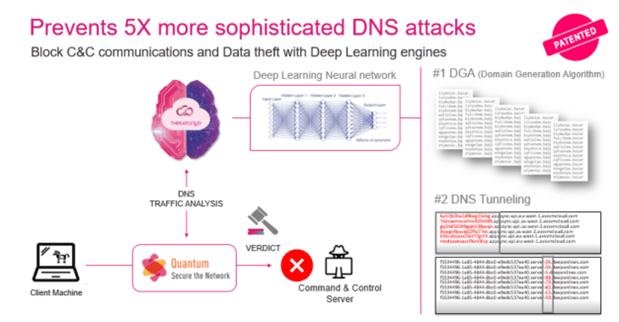
Figure 1 – Prevents X5 more sophisticated DNS attacks
A full explanation of the DeepDNS engine can be found on Check Point Research’s blog. But essentially, it works like this. ThreatCloud AI DNS tunneling protection uses an advanced Deep Learning Data Driven engine for DNS Query analysis to understand tunneling attempts. The sensor forwards the DNS Query to ThreatCloud AI for analysis and the query is analyzed with Deep Learning logic with a verdict provided back.
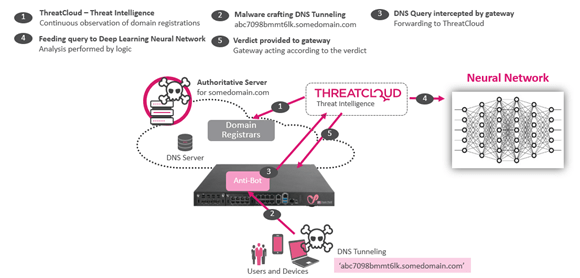
According to a latest Check Point Research (CPR) report, the research team conducted a search for anomalies across the available telemetry and ran DeepDNS on this corpus. Among the numerous findings flagged as anomalous, one previously unknown cluster of domains drew their special attention:
-
rqmetrixsdn[.]info
-
candatamsnsdn[.]info
-
mapdatamsnsdn[.]info
A closer look at the infrastructure connected with these domains suggests they are part of a DNS backup channel used for CoinLoader infections.
CoinLoader was described in this extensive report by Avira, but we could not find prior documentation describing this specific feature. Samples were found in an archive, typically a rar or a zip, containing several files. While the names varied, what you see below is more or less representative of the file structure in each sample.
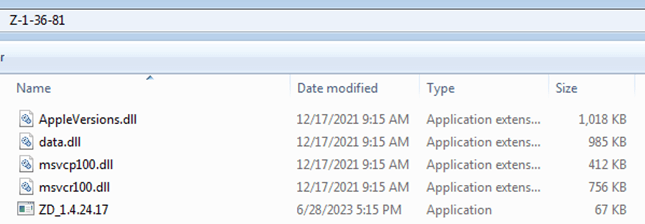
The executable (ZD_1.4.24.17 in the image) is always some legitimate tool which is used for DLL sideloading. The main malicious logic is in the sideloaded DLL (here AppleVersions.dll). Upon being loaded, it goes through several layers of unpacking, including a well-obfuscated check that its parent process was launched from inside the Z-1-36-81 directory (again, the directory name varies from sample to sample) that is buried inside some complex control flow structures.
DeepDNS is able to parse out these differences, and prevent it from infecting your network. The DeepDNS conclusions drawn are automatically pushed to Check Point ThreatCloudAI.
AI is all the rage now, but Check Point has been using it for years and we continue to innovate in this field. No attack is too large or too small for our customers—every attack matters, and we will continue to push the pace. Our DeepDNS engine is yet another example.
Read Check Point Research’s full report about DNS tunneling here.









