
Secure Your Netflix Account: Limited Sharing Can Result in Dark Web Sales for €2 per Month
Check Point Research Sees Illicit Sale of Premium Subscriptions on the Dark Web
Netflix, the globally renowned streaming and entertainment platform, recently discontinued one of its popular features: shared accounts. This controversial decision caused a significant user exodus, with Netflix losing over one million subscribers in Spain alone during the first quarter of 2023, according to a Kantar study. This indicates that many users are reluctant to pay for individual account plans.
Unfortunately, this situation has created an ideal scenario for cybercriminals. Check Point Research, Threat Intelligence division of Check Point, has identified numerous illicit businesses selling Netflix subscriptions on the Dark Web.
Researchers have uncovered Telegram channels affiliated with these cybercriminal portals offering access to Netflix’s monthly Premium plan for as little as 190 Indian rupees, which is just over €2. These channels promote “full access effectiveness and legitimacy” to entice potential buyers.
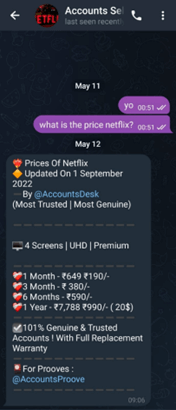
Figure 1. Example of Netflix account sales on Telegram
However, it is crucial to note that accounts sold through these portals are often linked to other cybercrimes. Most of these accounts are obtained from compromised credentials or breached accounts. Consequently, cybercriminals can offer significantly reduced prices, reaping full profits without incurring any costs.
It’s important to highlight that, like any criminals, these cybercriminals may not uphold their end of the bargain. Check Point Research has encountered instances where users either failed to gain access or had their access blocked after a few days, weeks, or months.
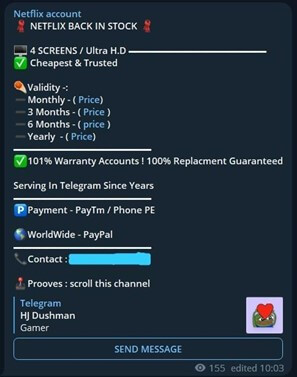
Figure 2. Example of Netflix account sales on Telegram
Ironically, it is now time for users to implement the measures that Netflix previously criticized and restrict shared access to their accounts, particularly with individuals they do not wish to share them with. To assist with this, Check Point Software offers tips to ensure Netflix account security, password integrity, and prevention of unauthorized usage:
- Lengthy and Diverse Passwords: Increase password complexity by utilizing a combination of 14 to 16 characters comprising various letters (upper and lower case), symbols, and numbers.
- Memorable but Difficult to Guess: Avoid using personal data such as birthdays, names of yourself or family members, or easily discoverable information. What may be easy for the user is also accessible to cybercriminals.
- Unique Passwords: Avoid reusing passwords across different accounts. If a cyber attacker compromises one password, they gain unrestricted access to all other registered services, leading to more significant damage. Consider using a password manager to securely store and manage passwords.
- Keep Passwords Private: Never share passwords with anyone or store them in close proximity to the computer, including digital files. Utilize password manager tools for secure storage.
Additionally, if any suspicious activity is detected on an account, such as the appearance of new profiles or unusual content playback, users should check for unauthorized access and immediately change their passwords.
Cybercriminals often exploit users’ needs and desires, aligning their attacks with ongoing trends. As with any other domain, it is important to remember that if an offer seems too good to be true, it probably is. Reducing demand is an effective way to counter illegitimate sales on the Dark Web and subsequently disrupt revenue streams from these services.









