
Securing a Hyperconnected World: The Case for Check Point’s Hybrid Mesh Security Architecture
Introduction:
AI is reshaping cyber security—accelerating both innovation and attack sophistication. As enterprises expand across cloud, remote, and on-prem environments, cyber criminals are leveraging generative AI to launch faster, more convincing, and more damaging campaigns.
Traditional firewalls and siloed solutions cannot keep pace. Defending the modern enterprise requires a unified, flexible architecture—and a relentless focus on efficacy. It is not enough to detect threats; they must be stopped.
This paper explores the rise of Hybrid Mesh Firewalls, why traditional models fall short, and how Check Point delivers industry-leading prevention and protection in the AI era with the Hybrid Mesh Network Security Architecture.
The New Attack Surface: AI-Enabled Threats in a Hyperconnected World
The same technologies that power modern business—cloud computing, ubiquitous access, and artificial intelligence—are increasingly being weaponized by cyber criminals. As organizations expand their digital footprint, the attack surface grows in parallel.
Case in point, according to the IBM Cost of a Data Breach Report 2024, breaches involving data distributed across multiple types of environments (e.g. public cloud and on premises) occurred more often (40%) than those in public cloud (25%), on-premises (20%) or private cloud (15%).
At the same time, adversaries are evolving at breakneck speed. Generative AI has significantly lowered the barrier to entry for cyber crime. Threat actors are leveraging it to craft highly convincing phishing campaigns, automate exploit code generation, and even create realistic deepfakes for sophisticated social engineering attacks. According to the KnowBe4 Phishing Threat Trends Report, over 82.6% of phishing emails observed between September 15, 2024 and February 14th, 2025 exhibited some use of AI.
This rapid evolution in cyber threats is outpacing organizations’ defenses. Fueled by increasingly sophisticated actors and the continued rise of cloud and remote work environments, today’s attacks easily bypass traditional perimeter-based security models. A stark example comes from the Check Point 2025 State of Cyber Security Report, which details how the financially motivated threat group Storm-0501 executed multi-stage campaigns in 2024. They infiltrated hybrid cloud environments, moved laterally between on-prem and cloud systems, and deployed backdoor accounts before triggering widespread ransomware across networks.
To meet this new threat landscape, defenders must rethink their strategies. It starts with a hard look at the foundations of network security—and a commitment to modernizing their approach to keep pace with the adversary.
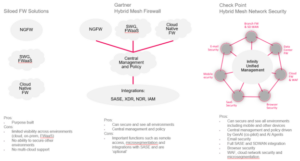
Why SiloedModels Fall Short in a Hyperconnected World
As enterprises expand across data centers, clouds, and remote users, siloed security models struggle to keep up. On-prem NGFWs, cloud-only services, and cloud-native controls each address pieces of the puzzle—but none fully protect today’s distributed, dynamic environments.
Where Legacy and Siloed Models Miss the Mark
On-Prem NGFWs:
Designed for fixed perimeters, NGFWs cannot secure cloud workloads or remote users.
Key Gaps: Limited cloud visibility, perimeter focused.
Cloud-Only Services (e.g., Zscaler):
Great for remote access and internet-bound traffic, but lack internal visibility and can add complexity.
Key Gaps: No on-prem coverage, limited for internal apps, potential latency.
Cloud-Native Firewalls (e.g., AWS Network Firewall):
Scalable within their own cloud but siloed. An AWS firewall cannot see into Azure or private data centers.
Key Gaps: No multi-cloud visibility, inconsistent policies.
Each model addresses part of the challenge—but securing the hyperconnected enterprise requires more than siloed solutions.
Enter the Hybrid Mesh Firewall: A Unified Model for Network Security
Recognizing the complexity of today’s enterprise environments, Gartner published the Market Guide for Hybrid Mesh Firewall Platforms, as a modern architectural model to address the limitations of fragmented, perimeter-centric security. This model aligns network protection with how applications, data, and users truly operate—across hybrid cloud, on-premises, remote, and mobile environments.
A hybrid mesh firewall provides centralized policy control and distributed enforcement across a variety of deployment types, with capabilities grouped into existing, core, and optional categories. Together, these capabilities enable a unified approach to managing risk in a hyperconnected world.
Existing Capabilities: Proven Foundations of Network Protection
These are the core functions that most mature NGFWs already deliver, forming the baseline of any enterprise firewall deployment. They remain essential within the hybrid mesh firewall framework. Furthermore, the efficacy of these core functions sets the stage for how well attacks are prevented:
- Stateful Inspection: Monitors all active connections and enforces policies based on session state.
- Intrusion Detection and Prevention (IPS): Blocks known and unknown threats in real time, including vulnerability exploits and evasion techniques.
- Application Identity and Control: Provides granular control over application usage, regardless of port or protocol.
These existing capabilities continue to play a critical role—but they must now be extended across environments and integrated with newer tools and deployment models.
Core Capabilities: What Makes the Hybrid Mesh Firewall “Hybrid”
These are the defining features of the hybrid mesh firewall model—what distinguishes it from legacy NGFWs or cloud-only point solutions. Gartner considers these capabilities as core to supporting distributed enterprise environments:
- Multiple Deployment Options: At least two or more of the following must be supported—hardware appliances, virtual firewalls, cloud-native firewalls (e.g., AWS, Azure), containerized firewalls for Kubernetes environments, and firewall-as-a-service (FWaaS).
- Cloud-Based Centralized Management:
- A unified management console for all deployments.
- Policy auto-tuning and recommendations.
- Visibility into cloud-native microsegmentation controls.
- CI/CD and DevSecOps Integration:
- Automation hooks via tools like Jenkins or Red Hat Ansible.
- Tag import to dynamically enforce policy based on DevOps context or cloud asset metadata.
- Support for change management within agile application development pipelines.
- Application Observability:
- Application discovery.
- Application connectivity mapping.
- Application usage visibility.
- Advanced Threat Prevention for IoT and DNS attacks:
These core capabilities provide the scalability, intelligence, and operational efficiency needed to secure modern enterprise networks from the edge to the cloud.
Optional Capabilities: Enhancing Reach, Flexibility, and User Experience
Gartner also identifies a set of optional capabilities that are increasingly valued by organizations seeking to extend firewall functionality into new domains, such as remote access, home offices, and extended detection:
- Zero-Touch Home Office Firewall Appliances:
- Plug-and-play security for branch offices or remote employees with minimal IT intervention.
- Secure Remote Access:
- SSL VPN and IPsec VPN capabilities.
- Zero Trust Network Access (ZTNA).
- Unified Endpoint Client:
- Single agent to manage endpoint access control, VPN, and other security functions.
- Can simplify endpoint security deployment and improve user experience.
- Microsegmentation (Agent-Based or Agentless):
- Enforce fine-grained policy within cloud and containerized environments.
- Prevent lateral movement in case of compromise.
- Third-Party and Ecosystem Integrations:
- Integration with XDR, SASE, IAM, and NDR platforms.
- Enables a cohesive security operations architecture and streamlined incident response.
The Importance of Firewall Efficacy in Cyber security
One thing notably absent from Gartner’s Market Guide for Hybrid Mesh Firewall Platforms is the most important requirement of all: your firewall—hybrid mesh or otherwise—must be effective at preventing attacks. Without that, nothing else matters.
Firewall efficacy is fundamental to cyber security. As the first line of defense, firewalls monitor and control network traffic to block unauthorized access, data breaches, and malware. Whether cloud-based or on-premises, their ability to detect and stop threats is essential to protecting sensitive systems and maintaining business continuity.
However, not all firewalls are equally effective—especially those offered by cloud service providers (CSPs). Microsoft Azure, Google Cloud Platform (GCP) and Amazon Web Services (AWS) network firewalls were rated 0% by a CyberRatings.org report published on April 2. According to the report, “[n]ative cloud firewalls from Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure offer a convenient alternative, but all received 0% Security Effectiveness as they allowed attacks to bypass existing defenses.” Third party vendors scored much better with Check Point delivering 100% security effectiveness.
These findings underscore the need to assess your security requirements carefully and consider proven third-party firewalls. In a threat landscape that evolves daily, effectiveness is not optional—it is essential.
The Check Point Approach – Providing the Best Prevention for a Hyperconnected World
This is why Check Point is focused on delivering a solution for the hyperconnected world that is the most efficient, as shown in Miercom’s Enterprise and Hybrid Mesh Firewall 2025 Q1 report. It addresses the needs identified in Gartner’s report and then takes that a step further with the Check Point Hybrid Mesh Network Security Architecture.
Check Point Hybrid Mesh Network Security Architecture
Check Point’s Hybrid Mesh Security Architecture (hybrid mesh) provides organizations with the flexibility to enforce security where it makes the most sense for their particular use cases and needs. It eliminates reliance on a single enforcement point, making security more resilient, distributed, cost-effective and scalable.
The diagram below shows how security has evolved to cover each edge of the mesh network.
Key Features
A hybrid mesh architecture supports:
- Hybrid Mesh Connectivity: Connect directly to the resource or via the cloud
- Hybrid Security: Deploy security where needed—on-prem, on-device or in the cloud.
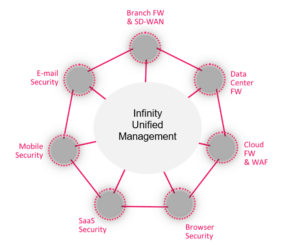
Figure 1: Hybrid Mesh Network Security Architecture
Sample Use Cases
With a hybrid mesh architecture, organizations can deploy security where it makes most sense, for example:
- On-device mobile security: Ideal for remote users access to the internet.
- Cloud-based security: For remote users without agents.
- Cloud-native security: Closer to IaaS and cloud workloads.
- On-premises security: For branches and IoT devices.
Over and Above the Hybrid Mesh Firewall
In addition to providing the full existing, core and optional capabilities of a Hybrid Mesh Firewall, the Check Point Hybrid Mesh adds the following:
- Email security, an essential layer of defense against ransomware.
- Browser security.
- Mobile device security.
- Full SASE solution, including SDWAN connectivity.
- Unified policy, with centralized policy configuration, zero trust access and granular threat prevention.
- AI-enhanced security operations with Generative AI assistants, XDR with over 100 out of the box playbooks, API integrations with 3rd party vendors.
The diagram below summarizes the evolving architectural approaches to secure a hyperconnected enterprise and the pros and cons of each.
Miercom Security Efficacy Assessment for Enterprise & Hybrid Mesh Firewalls (2025)
Check Point goes beyond marketing claims to demonstrate that its Hybrid Mesh Architecture delivers the strongest protection.
Miercom, an independent testing lab, released a 2025 Q1 report comparing the security efficacy of firewall solutions from Check Point, Cisco, Fortinet, Palo Alto Networks, and Zscaler. The assessment focused on preventing modern threats like zero-day malware, phishing, and known vulnerabilities.
Objectives and Methodology
The goal: measure how well each firewall prevents (not just detects) threats. “Prevention” means blocking attacks before they enter the network; “Detection-Only” means the threat was flagged but still got through. Over 90 days, each solution was assessed under real-world conditions using:
- Fresh, obfuscated malware samples from VirusTotal.
- Phishing URLs less than 24 hours old.
- BreakingPoint simulations for intrusion prevention.
- SSE/FWaaS threat scenarios.
All products were configured per vendor best practices and tested simultaneously.
Key Findings
- Zero+1 Day Malware Prevention
This test evaluated blocking malware within 24 hours of discovery.
- Check Point scored 99.9% across all file types.
- Zscaler: 90.9%; Fortinet: 87.7%; Cisco: 67.1%; Palo Alto: 62.7% (plus 25.2% detection-only).
Check Point delivered strong real-time protection against advanced threats. It also blocked every piece of detected malware, unlike Fortinet, Palo Alto Networks, and Cisco.
- Phishing URL Blocking
Phishing remains a top attack vector.
- Check Point blocked 99.74%, missing just one URL.
- Palo Alto: 98.69%; Fortinet: 97.39%; Zscaler: 91.12%; Cisco: 55.87%.
Check Point’s AI-driven content inspection outperformed others significantly.
- SSE/SASE Malware Protection (FWaaS)
For remote workforce security:
- Check Point: 99% block rate
- Cisco: 96%; Fortinet: 84%; Zscaler: 83%; Palo Alto: 74%
- CISA The Cybersecurity and Infrastructure Security Agency (CISA)’s Known Exploited Vulnerabilities (KEV) Catalog is an authoritative list of vulnerabilities actively used in real-world attacks, helping organizations prioritize high-risk threats. Firewall vendors should focus on mitigating as many vulnerabilities as possible from this catalog. Additionally, they must avoid introducing any Known Exploited Vulnerabilities (KEVs) in their own products. The number of KEVs in their products indicates how well-protected they are against potential breaches. Moreover, the more KEVs a product has, the more patches will need to be applied to maintain security.
Patching a firewall carries higher risk and cost compared to other software due to its critical role in controlling network traffic. A failed or misconfigured patch can cause widespread service disruptions, block remote access, or introduce security gaps, often requiring skilled personnel and after-hours work to test and implement safely. Rollbacks are complex, and changes can impact integrations with other security systems. In contrast, patching endpoint or business software typically poses less risk, can often be automated, and affects only specific functions rather than core connectivity. As a result, firewall patches require more planning, validation, and caution than most other updates.
Vendor ability to mitigate vulnerabilities in CISA’s KEV catalog:
- Check Point mitigated 866 KEVs, Fortinet 830, Cisco 756 and Palo Alto Networks mitigated 745.
Vendor Specific KEVs:
- Check Point – 1 KEV, Fortinet – 16, Cisco – 21, Palo Alto Networks – 11
Check Point demonstrates superior prevention capabilities by mitigating more vulnerabilities from the KEV catalog than other vendors. It is also the most hardened solution available, with only a single KEV vulnerability reported. Choosing Check Point helps organizations minimize risk, reduce operational disruptions, and avoid unnecessary costs.
- Intrusion Prevention System (IPS) Performance
Simulated high/critical CVEs (2022–2024) from the BreakingPoint network security testing platform:
- Check Point: 98% block rate
- Fortinet: 94.6%; Palo Alto: 91.6%; Zscaler: 72.5%; Cisco: 42.6%
Testing Approach
Malware prevention used 1000 daily VirusTotal samples, lightly altered to evade signature-based detection. SSE tests focused on common file types (e.g., PDFs, DLLs), and phishing tests used links discovered within 24 hours. IPS testing used Breaking Point to simulate CVE-based attacks.
Miercom Test Summary
Check Point led across all vectors—malware, phishing, remote protection, KEV, and IPS—proving itself the most effective solution. Fortinet and Zscaler performed well in select areas, but Palo Alto and Cisco revealed gaps in threat prevention. The report underscores the value of unified architectures, real-time prevention, and AI-driven threat intelligence—where Check Point sets the benchmark.
Conclusion: Keeping current and future networks secure with Check Point
Check Point’s Hybrid Mesh Network Security Architecture stands out as a comprehensive and adaptable solution for the hyperconnected world. By addressing the needs identified in Gartner’s report and outperforming competitors in Miercom’s 2025 Q1 assessment, Check Point demonstrates its commitment to providing resilient, scalable, and cost-effective security. The integration of advanced capabilities such as AI-enhanced security operations, unified policy management, and full SASE solutions ensures that organizations can effectively protect against modern cyber threats while maintaining flexibility and efficiency. Check Point’s innovative approach sets a high standard for network security, making it an asset for any enterprise looking to safeguard its digital infrastructure.
Download Miercom’s Enterprise and Hybrid Mesh Firewall 2025 Q1 report.



