
Stop Neglecting Your Cloud Security Features
Check Point Research Found Thousands of Open Cloud Databases Exposing Data in the Wild
Highlights
- Check Point Research (CPR) warns against bad practices in cloud-based application development that could lead to serious security breaches.
- Thousands of new applications every month have their Firebase databasess open leaving data exposed.
- In a course of three months, CPR found 2,113 mobile applications using Firebase, which made their way to Virus Total leaving victims unprotected and easily accessible for threat actors to exploit.
- Exposed information includes: chat messages in popular gaming apps, personal family photos, token IDs on a healthcare applications, data from cryptocurrency exchange platforms and more
Introduction:
Cloud platforms have changed the way developers work and have become a standard in application development. While writing code, developers invest a lot of resources to harden an application against several forms of attacks. However, developers may neglect configuring the cloud database properly thus leaving real-time databases exposed, which could then results in a catastrophic breach if exploited.
Developers often manually change the default locked and secured configurations of security rules to run tests. If left unlocked and unprotected before releasing the application to production it leaves the database open to anyone accessing it and thus susceptible to read and write into the database.

Figure 1 – Security rules for Real-time Database in Firebase Console
While misconfigurations in the cloud are seen as the least sophisticated types of cloud exploits, it costs companies in all industries millions. Buckets are sometimes left opened for months or years before they are reported, and with sophisticated attacks increasingly prevalent in today´s the threat landscape, organizations cannot afford to have a bad security hygiene.
Overview and examples
CPR found a considerable amount of unprotected databases by simply creating a query in Virus Total that searched for Firebase URLs in APKs: content: “*.firebaseio.com” type: apk . This search gave all the applications communicating with Firebase services.
Researchers checked if access to the database was set on read by accessing the /.json URL. Here is an example of the URL: <DB_name>.firebaseio.com/.json. Any DBs containing sensitive data exposed here should not be accessible as a rule. Next, we filtered with keywords such as ”Token”, “Password” or “Admin” which led to many interesting findings. Below are a few examples that demonstrate the diversity of data available.
Disclaimer: CPR shared the information with the relevant entities to better protect their environments.
Department Store Application (10+ Million Downloads)
In the example below, this e-commerce application had mistakenly exposed its API gateway credentials and API keys. CPR was able to access this data without facing any kind of protective mechanism. The app owner is a very large shopping chain in South America.

Figure 2 – Open DB from a widely used e-commerce mobile application with cleartext credentials
Running Tracker Application (100,000+ Downloads)
This fitness application, developed to track and analyze running performances, left its users’ GPS coordinates and other health parameters, like heart rate, exposed because of their unsecured database. The victims’ coordinates could be used to create maps to track their whereabouts.

Figure 3 – Phone models and GPS coordinates exposed in a Running tracker application
Dating Application (10,000+ Downloads)
CPR found over 50,000 private messages in the open database of a dating application.

Figure 4 – Private chat messages exchanged in a dating app with pictures of the senders
Logo Design Application (10+ Million Downloads)
This widely used application for logo and graphic design creation exposed 130,000 usernames, emails and passwords.

Figure 5 – Usernames, passwords and emails in design creator application’s DB
Social Audio platform application (5+ Million Downloads)
CPR also found a very popular social audio platform where users can buy and share podcasts and various audio materials. The application’s open database exposed users’ bank details, location, phone numbers, chat messages, purchase history and more.

Figure 6 – Open DB of audio application with bank details and phone number
Bookkeeping Application (1+ Million Downloads)
This accounting services app for small and medium businesses exposed 280,000 phone numbers associated with at least 80,000 company names, addresses, bank balances, cash balances, invoice counts and emails.
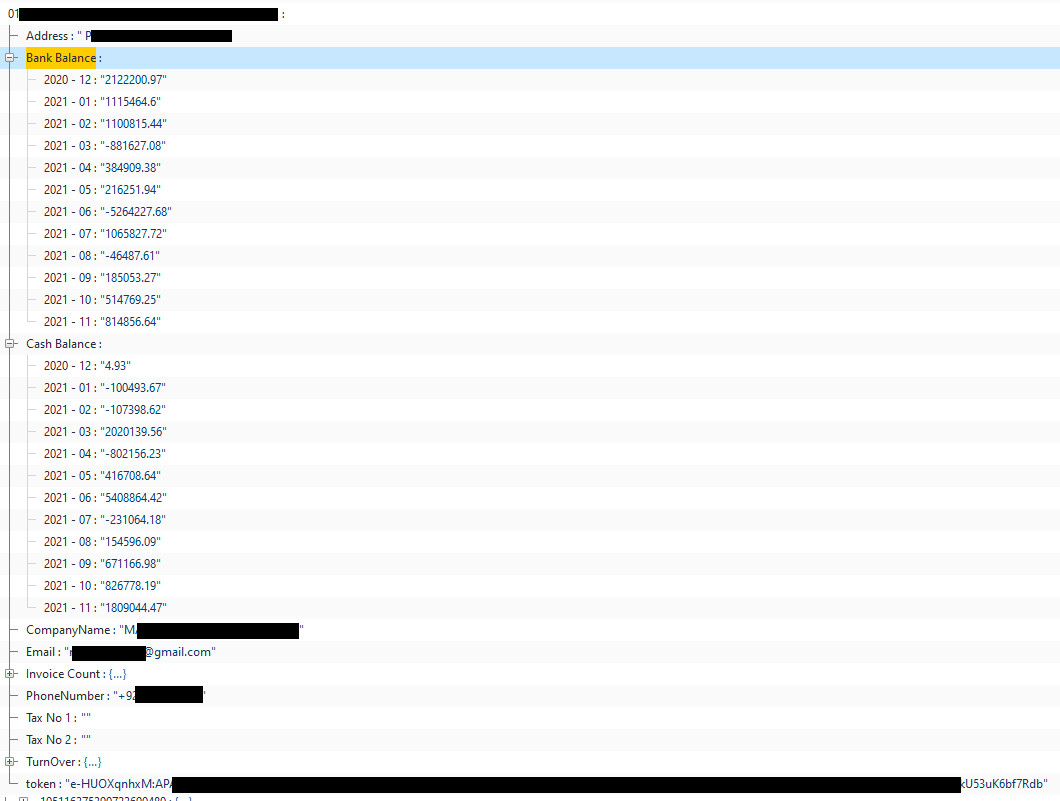
Figure 7 – Company name, email address, address and balances from accounting app DB
PDF reader Application (500,000+ Downloads)
Lastly, this PDF reader application had its OpenVPN configuration Base64file with private keys exposed. This could potentially be used by a hacker to connect to the company’s VPN and intrude their network.

Figure 8 – Base64 of openVPN configuration file in open DB

Figure 9 – Configuration file after decoding in ‘CyberChef’
Through further examination, researchers were able to find opened databases that shared a plethora of information including: chat messages in popular gaming apps, personal data (like family photos), token IDs on a healthcare application containing highly sensitive patient data, cryptocurrency exchange platforms and many more. Ironically, several of these database storages had disclaimers assuring the high security and privacy standards of the associated application.
How does it happen?
It isn’t uncommon for an application in development to be uploaded to publically accessible platforms like Virus Total. There are several reasons behind it. For instance, some developers check to see if their application is flagged as malicious (especially applications of invasive nature) and use sandbox features. Or when organizations’ security policies upload it automatically, sometimes without the developer’s knowledge. Out of all the Firebase applications uploaded to Virus Total, over 2,000 applications, which sums to 5%, were left with their databases open, equivalent to thousands of new applications every month.
Conclusion and Safety Tips:
These databases represent a gold mine for malicious actors, as they allow them to read and write new values in the database. A hacker could potentially change entries in the bucket and inject malicious content that could infect users or wipe the whole content. There were multiple cases of ransomware groups leveraging misconfigured cloud storages, demanding ransom payments after extracting and wiping databases that were left open. In a different occurrence, some threat actors even double extorted, threatening to report the organization’s bad practices to the General Data Protection Regulation (GDPR) authorities for failure to comply with data and privacy protection principles. Companies abiding to the GDPR regulations are entrusted and responsible for the data they gather and potentially risk penalties or fines that could cost them millions should they be found in violation of certain security standards.
The variety of possible attacks is subject to the type of exposed data. It is a bottomless pit of possibilities ranging from fraud, identity theft to ransomware or even supply chain attacks.
Cloud misconfiguration isn’t a new issue, but it currently affects millions of users and has the potential to damage thousands of organizations and businesses. In May 2021, ´CPR discovered multiple misconfiguration flaws in third party cloud services of Android applications, which led to the exposure of sensitive personal data of more than 100 million Android users and developers. Many flaws were the result of improper configuration of real-time databases.
Cloud misconfigurations are the consequences of lack of awareness, proper policies and security training that are further heightened and needed with the new work from home hybrid model. Bad security practices can cause extensive damage, and is yet only one simple click away from being remediated.
Here are some tips to ensure your different cloud services are secure:
Amazon Web Services
AWS CloudGuard S3 Bucket Security
Specific rule: “Ensure S3 buckets are not publicly accessible” Rule ID: D9.AWS.NET.06
Google Cloud Platform
Ensure that Cloud Storage DB is not anonymously or publicly accessible Rule ID: D9.GCP.IAM.09
Microsoft Azure
Ensure default network access rule for Storage Accounts is set to deny Rule ID: D9.AZU.NET.24
Check Point’s CloudGuard for Application Security Stops attacks against web applications with a fully automated, cloud native application security solution. It eliminates the need to manually tune rules and write exceptions every time an update is made on web application or APIs.
Check Point Harmony Mobile provides complete protection securing mobile devices across all attack vectors: apps, network and OS and delivers complete protection for mobile that is simple to deploy, manage and scale.









