
Summer Break Isn’t a Vacation for Cybercriminals: Education and Research Organizations are Top Targets According to Check Point Research
Highlights:
-
In comparison to other industries, the Education/Research sector experiences the highest rate of cyberattacks, with a vast disparity
-
This year, the Education/Research sector has witnessed an average of 2256 weekly cyber-attacks per organization
-
The APAC region recorded the highest rate of weekly cyberattacks per Education organization, with an average of 4529 attacks per week
In an ever-growing digitalized world, the education sector has already transformed itself into digitalization platforms, and elevated its services to the students and educators, widely using it across schools, universities, and other relevant organizations. However, as always, with progress comes risks and a variety of threats, and this domain is no exception.
In this report, Check Point Research (CPR) reveals that the education and research sector has been the most targeted domain compared to other industries. Furthermore, our data highlights a significant disparity between the domain and others.
Education under attack
So far this year, the Education/Research sector experienced an average of 2256 weekly cyber-attacks per organization. This reflects a slight decrease of 1% compared to the same period last year. However, despite this small decline, it is remarkable that the Education/Research sector still exhibits the highest rate of cyber-attacks among all industries, which is a significant contrast.
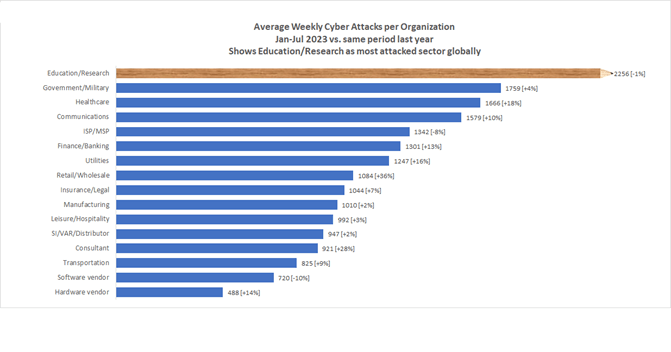
Figure 1- Average weekly attacks per org
Why is this happening?
The data shown here underscores the vulnerability of the education and research sector to cybercriminals. What are the reasons behind this trend? Why does this sector stand out as a preferred target?
One possible explanation is the pervasive digitalization within the sector and its heavy reliance on online platforms for various purposes such as studying, teaching, and testing. The proliferation of digitalization provides ample opportunities for attackers to exploit and amplify their attacks. Moreover, educational organizations store extensive amounts of sensitive student information, including personal and financial records, making them enticing targets for malicious actors.
In May it was widely reported that several U.S. Schools, colleges and universities have been impacted by ransomware attacks, causing severe disruption
Overall Attacks per Region:
So far in 2023, the APAC region recorded the highest rate of weekly cyber-attacks per Education organization, with a weekly average of 4529 attacks. Europe experienced the highest change compared to the same period last year, with an 11% increase YoY.
| Region | Average weekly Cyber Attacks per Organization | YoY Change |
| APAC | 4529 | -2% |
| Europe | 2427 | 11% |
| Africa | 1690 | -2% |
| Latin Americas | 1533 | 4% |
| North America | 1264 | -14% |
Phishing example – Golden Gate University Phishing Scam
In July 2023, a phishing email posing as Golden Gate University surfaced (see Figure 3). Pretending to be from “Golden Gate University”, but sent from an unrelated email address (mentor@skillmirrors[.]com), the email carried the subject “Seize Your Educational Opportunities – Explore Our Programs.” and showed information allegedly from an Ed-Tech firm named TalentEdge.
The email aimed to trick recipients into clicking an application link, which led to a website which is currently inactive (https://app[.]leadershipflag[.]com/campaigns) and has been flagged by multiple security vendors as a malicious phishing website. This could have potentially led users to give up their personal details or even perform an online payment on a fraudulent website.

HOW TO remain protected against cyberattacks
Educate and train- First and foremost, educating and training your work force to take security precautions to prevent a breach from occurring.
- Robust Data Backup- A robust, secure data backup solution is an effective way to mitigate the impact of a ransomware attack. If systems are backed up regularly, then the data lost to a ransomware attack should be minimal or non-existent. However, it is important to ensure that the data backup solution cannot be encrypted as well.
- Up-to-Date Patches– Keeping computers up-to-date and applying security patches, especially those labeled as critical, can help to limit an organization’s vulnerability to ransomware attacks as such patches are usually overlooked or delayed too long to offer the required protection.
- Anti-Ransomware Solutions– Anti-ransomware solutionsmonitor programs running on a computer for suspicious behaviors commonly exhibited by ransomware, and if these behaviors are detected, the program can take action to stop encryption before further damage can be done.
- Utilize better threat prevention– Most ransomware attacks can be detected and resolved before it is too late. You need to have automated threat detection and prevention in place in your organization to maximize your chances of protection.
How to protect against phishing
Check Point safeguards against the pervasive menace of phishing with its comprehensive 360° Anti-Phishing solutions, which provide all-encompassing security across various platforms such as email accounts, browsers, endpoints, mobile devices, and networks. It employs the revolutionary Check Point ThreatCloud AI, which, equipped with Zero-day phishing protection, scrutinizes hundreds of indicators of compromise in real time, efficiently distinguishing and blocking new and familiar phishing sites. The system meticulously inspects every attribute of incoming emails, including attachments, links, and textual content, substantially reducing risks before the messages even reach the mailbox. Check Point’s solutions, underpinned by ThreatCloud AI’s Zero-Day phishing engine, block 4X more attacks compared to signature-based technologies.
For organizations grappling with the ceaseless evolution and ingenuity of phishing attacks, Check Point Harmony Email & Office provides much-needed visibility and defense against diverse phishing strategies. Therefore, it’s crucial that organizations harness the power of advanced anti-phishing solutions such as these to counteract the cyber threats that exploit human nature as their weakest link.









