
Understanding and Minimizing the Security Risks of the Quantum Revolution in Computing
Recently we covered the state of quantum computing and its potential societal benefits. Now we will cover the potential impact of quantum computing on cybersecurity and how we at Check Point Software are innovating to ensure our customers receive the best security today and in the future.
Today’s cybersecurity solutions utilize public key cryptography to achieve secure communication and data protection. Public key algorithms are employed to ensure confidentiality, authentication, and data integrity. The security of cryptographic operations, such as signing, encryption, and key exchange, is dependent on the security of public key algorithms – mostly on RSA, Diffie-Hellman, Elliptic Curve – which rely on mathematical problems involving discrete algorithms and integer factorization. The fact that classical computers are unable to solve these problems, and therefore unable to break these algorithms, reinforces the security of the majority of cryptographic systems used today.
Quantum computers operate on the principles of quantum mechanics, which allow them to manipulate and process information in ways that classical computers cannot. As a result, quantum computers have the potential to solve certain types of problems exponentially faster than classical computers.
Quantum Computing’s Impact on Cybersecurity
Quantum computing’s exponential performance advantage, combined with dedicated algorithms (like Shor’s algorithm) focused on resolving specific cryptographic problems, could significantly reduce the computational time required for breaking any public key algorithm based on integer factorization and discrete log. Breaking public key algorithms enables the computer to extract the encryption key and therefore decrypt all data. Unfortunately, algorithms used today by all major networking protocols are public key based and therefore are vulnerable. Or put another way: quantum computing could effectively make it possible to break today’s encryption.
Encryption protects private and sensitive data. Every time a consumer makes a purchase through an app or a website, encryption is used to protect their financial and personal information. Encryption also protects medical data, company intellectual property and so much more.
So far, this breaking algorithm operation cannot be performed with today’s quantum computers. It will require a cryptographically relevant quantum computer (CRQC) to put the security of the Internet’s data transmissions via TLS, SSH, FTP and VPN networking protocols at risk.
Timing Question
The strongest quantum computer we have today is from IBM. It has 433 qubits. Researchers expect a CRQC will require approximately 8K qubits to decrypt encrypted data. The industry expectation is that commercial CRQC will be available around 2030.
However, there is another risk that needs to be taken into consideration. The “harvest today, decrypt later” attack assumes that some elements may record encrypted data communications today, store it and decrypt it later with CRQC to extract sensitive data. The following famous figure, created first by Dr. Michele Mosca and known as Mosca’s Theorem, illustrates timelines associated with the risk of this attack:
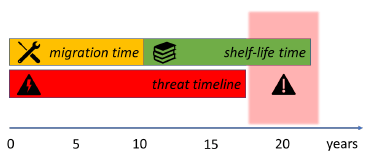
Given that CRQC will likely be available in less than 10 years and that in most cases data shelf-life time is 7-10 years, the industry should migrate to quantum safe solutions ASAP.
How Can We Protect Sensitive Data?
Addressing this security issue requires a consolidated effort between government, research and cybersecurity organizations worldwide.
To protect against this threat, the National Institute of Standards and Technology (NIST) established a Post-Quantum Cryptography Standardization Forum to unite the crypto experts from different countries, private, government and academic organizations. The forum aims to define and standardize new algorithms that are “quantum safe” (resistant against quantum computer attacks). The new algorithms should gradually replace the non-quantum safe algorithms used today by the industry.
Lately there has been significant progress in the work led by NIST. With the completion of the third round of quantum safe algorithm validations, the Forum came to conclusion that they are ready to announce the first four algorithms that are quantum safe.
Quantum safe solutions
What is the quantum safe solution? It’s а solution that cannot be broken using CRQC. Such solutions can be built in at least two ways:
- Software upgrade approach: the vulnerable public key algorithms are completely replaced with the quantum safe ones. This approach addresses all spheres where the vulnerable algorithms are used – identification and authentication, confidentiality and data integrity. The main risk associated with this approach is related to reliability of the new algorithms from the security perspective.
- Quantum key distribution (QKD) approach: the encryption key produced by one of the existing and potentially vulnerable public key algorithms is enhanced with additional key material or fully replaced with an external key. The additional key material or external key is generated independently and delivered over a dedicated quantum channel. The data transmission operates on the principles of quantum mechanics. This QKD solution is relatively new and still have certain physical limitations. This approach addresses only the issue of confidentiality in the data networking scenarios (e.g. VPN).
Of note, the National Security Agency (NSA) in the USA, the National Cyber Security Centre (NCSC) in the UK, and the Federal Office of Information Security (BSI) in Germany have clearly stated their recommendation to follow the software upgrade approach as the safest and most reliable approach.
Recent Developments
In the past year and a half, government agencies have started to publish guidelines and recommendations in the push for post-quantum encryption.
- January `22: the White House published “Memorandum on Improving the Cybersecurity of National Security, Department of Defense, and Intelligence Community Systems,” that directed the NSA to publish updated guidelines related to the transition to quantum safe computing, including timelines.
- March `22: following the White House directives, the NSA published an updated CNSA 1.0 (CNSS-15) specification, naming recommended algorithms to be used during the transition period.
- July `22: the NIST Post Quantum Cryptography Standardization committee announced four Post-Quantum Cryptography candidates for cybersecurity in the quantum computer era.
- September `22: the NSA released the Future Quantum-Resistant (QR) Algorithm Requirements for National Security Systems, the first explicit requirements declaring quantum safe algorithms for all functional areas as well as migration and enforcement timelines.
- January `23: Germany’s BSI published Security Requirements with guidelines and recommendations on algorithms and key sizes to be used for the transition period.
What Should Happen Now?
All software (and impacted hardware) vendors should begin providing solutions in the data communication and networking areas to ensure compliancy to the latest security recommendations for the migration period, while the non-quantum safe algorithms are still in use.
- All software (and impacted hardware) vendors providing solutions in the data communication and networking areas, need to start mapping all services and solutions that are using not quantum safe algorithms and plan the migration process to the quantum safe algorithms.
- The standards for the new algorithms replacing classic public key algorithms should be published by relevant international standardization organizations.
- All protocols and digital entities (like certificates) should enable hybrid operational mode. This means that when old algorithms will coexist with the new ones, they should be updated to enable smooth migration to the quantum safe solutions.
- All commonly used open source libraries like openSSL and openVPN should be updated by the community, adding support for the new algorithms.
- All companies relying on data protection and exchange solutions should identify all impacted products and ensure that software vendors providing these solutions are aligned with the industry migration roadmap drawn by CNSA 2.0 and other regulations.
Check Point’s Transition Plan to Quantum Safe Computing
As a preparation for the quantum computing era, Check Point is taking concrete steps to ensure customers will remain secure and their data private:
- As an immediate step, Check Point published a knowledge base article (sk178705) outlining the steps customer can take to implement NSA recommendations for using stronger keys for site-to-site encryption.
- Upon demand, Check Point Security Gateways will be ready for proof-of-concept implementation of quantum key distribution (QKD) deployments by allowing an external system to provide symmetric encryption keys. Research suggests that QKD will be able to detect the presences of an eavesdropper, which is not possible in standard cryptography.
- Additionally, Check Point will support Kyber, a post quantum computing (PQC) safe algorithm by July 2024, allowing customers to implement a backward compatible, quantum safe, site-to-site IPsec encryption.
We live in an exciting time of innovation. As researchers make progress toward realizing the benefits of quantum computing, at Check Point Software we remain dedicated to ensuring that our customers have the best security to protect them against advanced cyber attacks. We will continue to share updates as the field progresses.









