
Verify You Are Human (So We Can Steal Your Credentials)
Web server management faces numerous security challenges. Distributed Denial of Service (DDoS) attacks are one such threat. These attacks involve multiple bots bombarding the server with a high volume of requests in a short period of time, resulting in a congested network and potentially disrupting or blocking access for legitimate clients.
To defend against such threats, website owners employ various mitigation techniques such as traffic filtering, rate limiting, and CAPTCHA. CAPTCHA, which stands for “Completely Automated Public Turing test to tell Computers and Humans Apart,” serves three main purposes in protecting websites:
- Mitigate automated attacks
- Prevent unauthorized account creation
- Reduce spam from comments and forms
Turnstile is an alternative to CAPTCHA that offers a user-friendly approach to differentiate between human users and bots. It utilizes various techniques such as behavioral analysis, device fingerprinting, or biometrics to identify and block automated attacks while providing a seamless user experience. Turnstile aims to strike a balance between security and usability, offering an effective solution for protecting websites from automated threats without relying on traditional CAPTCHA challenges.
However, it is important to note that the same mechanisms that make Turnstile a user-friendly CAPTCHA alternative also present a potential risk if exploited by malicious actors. It’s possible to use Turnstile to block security probes and anti-phishing tools from effectively scanning phishing pages, thereby enabling attackers to evade detection by sophisticated anti-phish crawlers. As we show below, one such attack scenario involves using Cloudflare’s Turnstile to hinder web crawlers and phishing scan tools from accessing the malicious webpage. This allows the landing page to remain undetected for an extended period.
Additionally, the presence of CAPTCHA or CAPTCHA alternatives can create a false sense of security for unsuspecting or naive users. CAPTCHA’s presence may lead users to believe that the website or online form they are about to interact with is trustworthy and secure. This false perception can make individuals more susceptible to phishing attacks, as they may be less cautious when entering sensitive information or performing actions, assuming that the CAPTCHA provides adequate protection.
The following is a real phishing attack which was detected and blocked by Check Point’s Zero Phishing. The attackers utilized a Turnstile verification mechanism to evade detection by anti-phishing tools. The attackers utilize the verification process to remain under the radar of most anti-phishing bots for a longer period of time, compared to regular attacks, which results in a higher number of potential victims interacting with this page.
Cloudflare’s sophisticated “human verification” mechanism is not easily fooled, and takes into account many variables before confirming the user is not a bot.
For the user, most of the verification process is transparent; all that’s needed is to click on the blank square to start the verification process, which usually takes a few seconds.
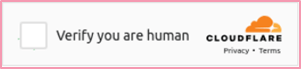
Figure 1: Cloudflare’s “Verify you are human” CAPTCHA alternative.
After passing the verification process, the victim was presented with a carefully designed phishing page which closely mimicked an authentic Microsoft login page. The unsuspecting victim proceeded to enter their credentials.
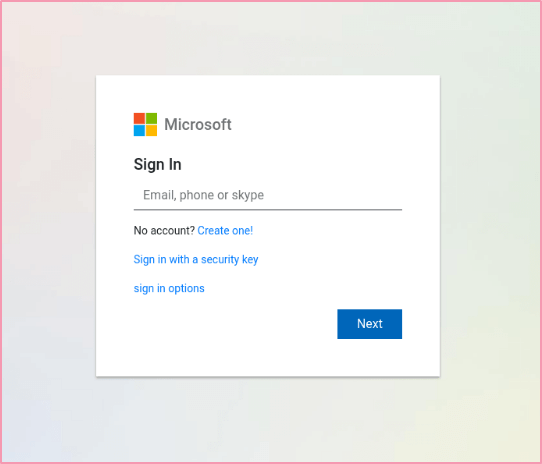
Figure 2: A phishing page which closely resembles an authentic Microsoft login page.
This case highlights the deceptive techniques employed by malicious actors who leverage Turnstile to deceive users and enhance the effectiveness of their phishing campaigns.
To enhance online safety and security, Check Point introduced an industry first, inline security technology, called ‘Zero Phishing’ in our Titan release, R81.20, leveraging patented technology based on dedicated AI engines.
Making Zero-Phishing Security available for all Check Point product lines – Quantum, Harmony, and CloudGuard.









