
What You Need to Know about the Pennsylvania Water Authority’s Breach
- Pennsylvania Water Authority hit by supply chain attack, demonstrating it’s possible to be a victim without being the main target of a cyberattack
- Iran affiliated hackers are claiming responsibility
What Happened?
Over the weekend, threat actors took control of a system associated with a booster station at the Municipal Water Authority of Aliquippa in Pennsylvania. The compromised system monitors and regulates water pressure for nearby towns.
A hacking group called Cyber Av3ngers has claimed credit for the attack.
Who is Cyber Av3ngers?
Cyber Av3ngers is an Iranian government-affiliated hacktivist group which has operated for a long time on and off, along different telegram channels focusing on Israeli targets.
The main goal of the group is information operations, while as part of it, the group mostly tries to target critical infrastructure in areas of electricity, transportation and water supply. The group has some technological capabilities, but like similar hacktivists groups, this group constantly exaggerates its achievements and in some cases, completely falsifies it.
Since the beginning of the Israel-Hamas war, the group expanded and accelerated their activities trying to target Israeli critical infrastructure and CCTVs.
On October 23rd, in an attempt to expand even further its operation, the group opened a Telegram community channel called “Mr.Soul,” to recruit additional hackers who can assist in attacking victims as per Cyber Av3ngers decision. As part of this operation, the group provides the volunteers with the names of the victims they want them to target.
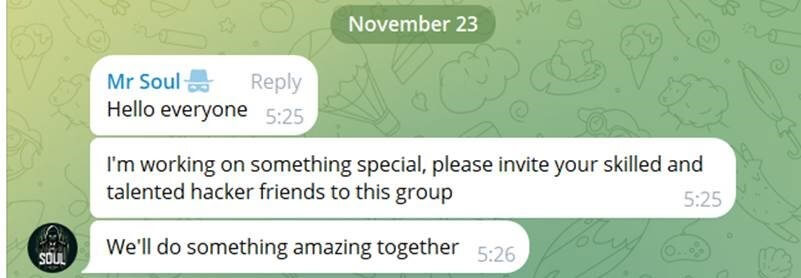
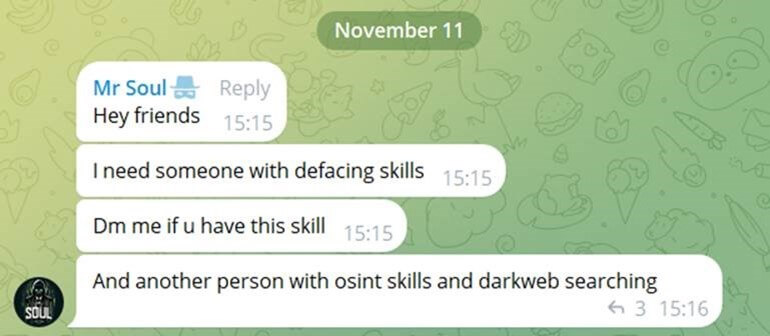
Mr. Soul – Cyber Av3ngers proxy is seeking for “talents” in specific areas.
For the targeting purposes, the group focuses on exploitation of vulnerabilities in internet facing devices. As part of their modus operandi, the group also seeks to utilize Microsoft Exchange vulnerabilities as an initial intrusion vector (most likely including CVE-2023-36745, but not limited to this one specifically).
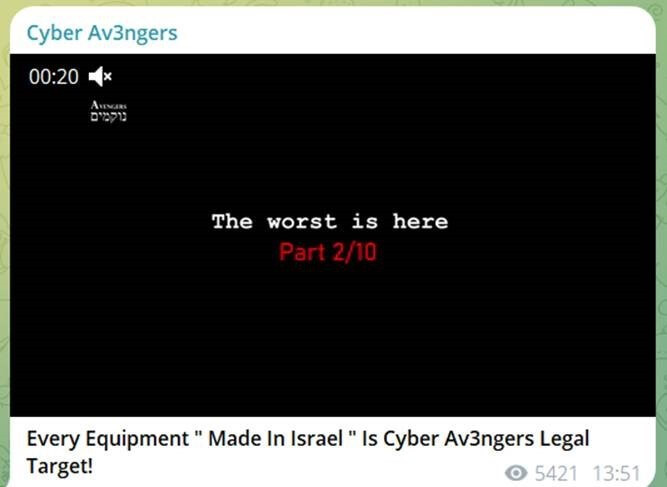
In the recent attack, we see an example that while most likely the actual victim wasn’t a real target of the group, it was attacked because they used equipment of an Israeli company which was the actual target of Cyber Av3ngers.
Announcement about attacking Israeli made equipment (Nov 26th):
Unique Challenges of Securing Critical Infrastructure
ICS and OT networks play a vital role in the global modern world but are also attractive targets to criminal groups, like in the Cyber Av3ngers example covered above. Threat actors are drawn to critical infrastructure and SCADA/ICS due to their inherent ability to cause economic disruption, espionage, intellectual property theft, and for geopolitical motives.
To mitigate the inherent risks effectively, organizations must prioritize implementing an ICS security solution, minimizing risk exposure in both IT and OT environments. The solution must be proactive, block attacks before they compromise critical assets, and ensure uninterrupted industrial operations.
Best Practices for Protecting ICS and OT Networks
Protecting ICS and OT networks for critical infrastructure presents distinct challenges including maintaining service uptime, ensuring data integrity, compliance adherence, and public safety. The increasing connectivity of critical infrastructure systems significantly expands the attack surface for ICS/SCADA systems and OT networks.
Businesses in this era must seriously consider adopting seamless and automated security measures. To address this need, Check Point’s ICS Security solution and the newly introduced Quantum Rugged 1595R security gateways offer a combination of network segmentation, automated security protocols, and advanced threat intelligence. An integrated approach aims to fortify critical infrastructure, ensuring protection against even the most sophisticated cyberattacks without disrupting production operations.
How Check Point Can Help
Check Point provides comprehensive ICS security, offering a broad range of cybersecurity solutions. Check Point’s threat prevention technologies have a 99.7% catch rate of Gen-V cyberattacks and provide full visibility of connected assets in a unified Infinity cybersecurity architecture.
The Check Point Quantum 1595R, an integral part of the Quantum Rugged line of NGFWs, ensures comprehensive visibility and precise control over all network traffic, effectively protecting against attacks on networks, devices, and logical processes. Specifically designed for deployment in challenging environments, this new security gateway enhances the Quantum Rugged series by offering proven integrated AI security, high-speed secure 5G connectivity, and other advanced features. It stands as a key component of a robust end-to-end ICS security solution.
Check Point Quantum Rugged 1595R delivers harsh environment resilience with:
- 400Mbps of artificial intelligence (AI)-powered threat prevention
- Comprehensive asset discovery
- IT-OT network segmentation
- Secure 5G connectivity at 1Gbps
- Supports 1,830 SCADA and ICS Protocols & Commands
To learn more about how Check Point can help protect you against threats to your ICS and OT Networks, please visit the following detailed article introducing our Quantum Rugged products.









