
Winning the war against unknown zero-day malware
In recent years, cybersecurity experts have been severely challenged by unknown zero-day malware attacks. This latest malware has been devised to evade traditional signature-based AV and older sandboxing techniques. According to Check Point Threat Intelligence, unknown malware attacks are capable of bypassing an organization’s spam and web filters over ten times a day.
In response, Check Point’s multi-layered detection capabilities such as dynamic emulation on the OS and CPU levels and static scanning can detect such evasive malware before they’re able to discharge destructive payloads. Users can now see activity at the processor-instruction level during the malware’s critical exploit phase or at the moment of the attack.
To complement our SandBlast Network protection, we developed SandBlast Agent, a second layer of defense for endpoint devices. It logs suspicious activity and communicates with ThreatCloud, the intelligence center for our SandBlast solutions.
SandBlast Agent’s zero-day prevention engines and automated forensic reports allow customers to understand attack origins and the different modules of execution. Together, the layered protection approach offers shared intelligence throughout the attack life cycle.
How does this work?
To illustrate this, let’s see how advanced sandboxing technology and our endpoint agent work in tandem to combat a current real-world attack example. You’ll see the value of the dual layers by tracking the attack behavior using an online forensic report that’s automatically generated for this attack.
Picking up the track of a previously unknown malware
On October 22nd, Check Point threat prevention engineers spotted a suspicious file detected by one of our SandBlast Zero-Day engines. The Suspicious Activity screen below identifies how this event was first recorded.
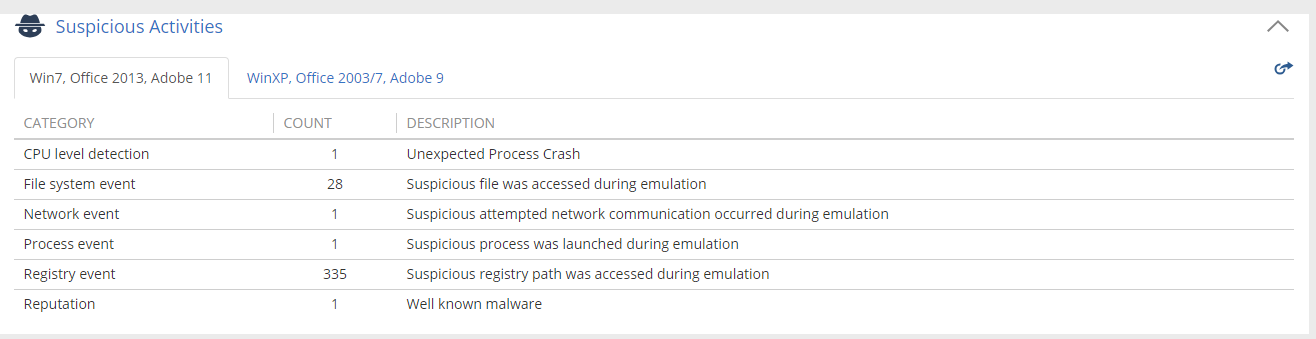
Figure 1. Suspicious Activity – CPU level detection
An initial scanning of the file with AV engines failed to detect any suspicious activity. Several hours later, only 1 out of 57 AV engines were able to detect this attack.
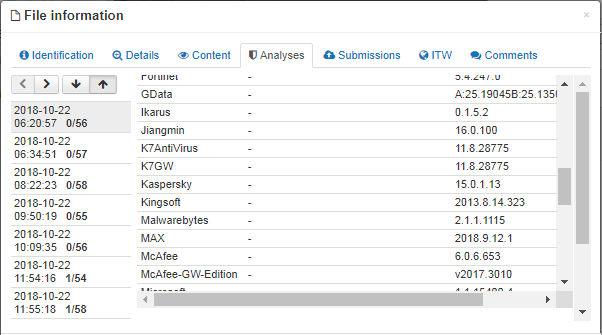
Figure 2. First five analyses on VirusTotal score of 0/57 for AV test scans
This attack continued for the next two days with only 13 out of 56 AVs successful. Malicious files are usually discharged only once to avoid detection by signature-based system; however, this attack persisted due to its low detection rate and its effectiveness against numerous Microsoft Office versions.
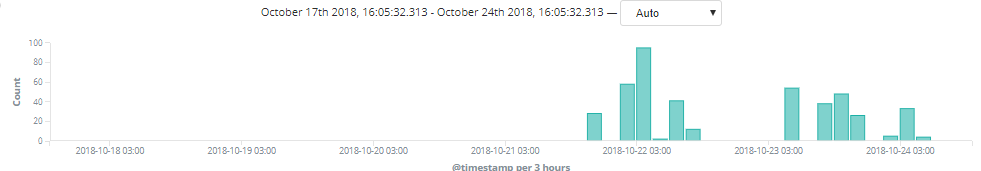
Figure 3. AV results over a three-day period
Threat analysts then determined this exploit used the popular Microsoft Equation Editor, a capability in Microsoft Word dating back to 2000. It was found to have been used in different malicious files blocked in over 50,000 events during the previous four-month period, but it remained with a relatively low detection rate by cybersecurity products.
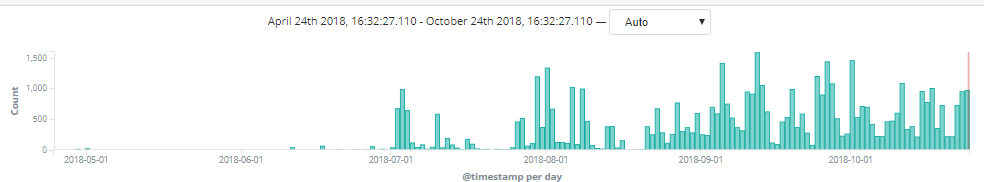
Figure 4. Equation Editor CVE-2018-0802 exploit popular over last 4 months
This exploit used the Equation Editor’s vulnerabilities to evade detection. An additional Equation Editor exploit (CVE-2017-11882) has seen similar growth this year:
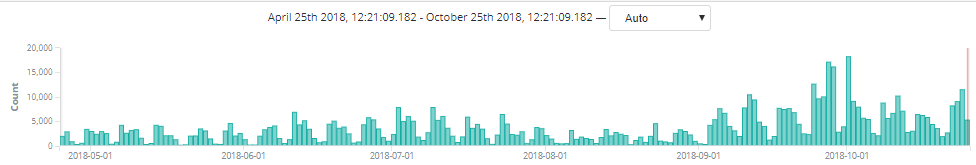
Figure 5. Another active Equation Editor exploit (CVE-2017-11882)
A catch for SandBlast Network, but what about other vectors?
The Check Point Infinity Architecture offers protection against multi-vector mega attacks across networks, endpoint, cloud, and mobile. How did our architecture fare against this exploit?
With today’s mobile workforce outside the protected network, we ran the exploit file in our emulation lab on a host with SandBlast Agent, our advanced threat prevention solution for endpoints. We purposely set the protection level to “detect only” and not full prevention. SandBlast Agent would serve as our test sandbox. This quick summary of the SandBlast Agent forensic execution tree will help you see how the attack unfolded:
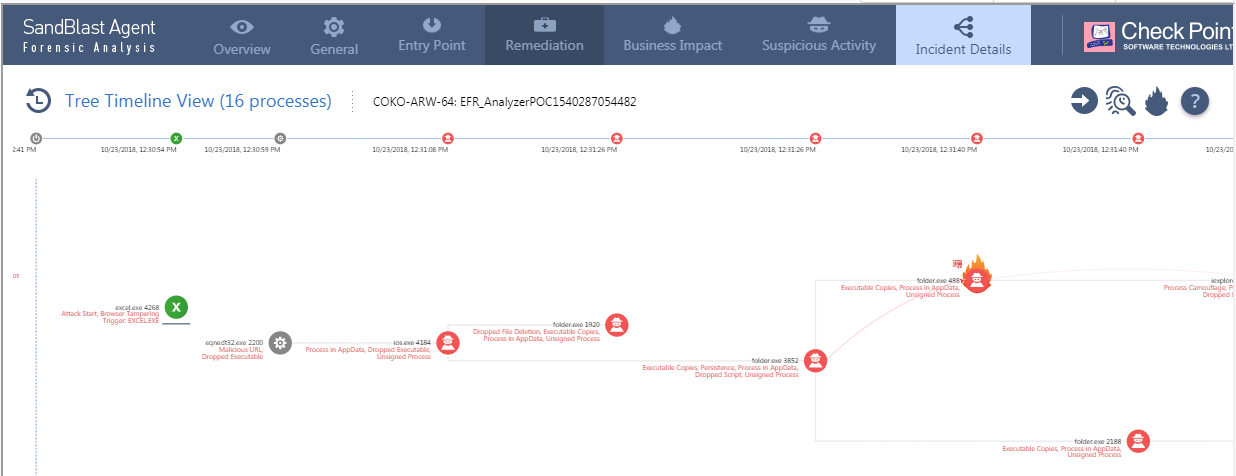
Figure 6. Summary of the execution tree from SandBlast Agent forensic report
Since we intentionally allowed the malware to penetrate our forensic host, the first prevention layer to block this attack was SandBlast Agent Anti-Exploit. This prevention facility detects an unauthorized query by the attack shellcode to Import Address Table (IAT) of loaded modules to obtain memory address of specific system functions.
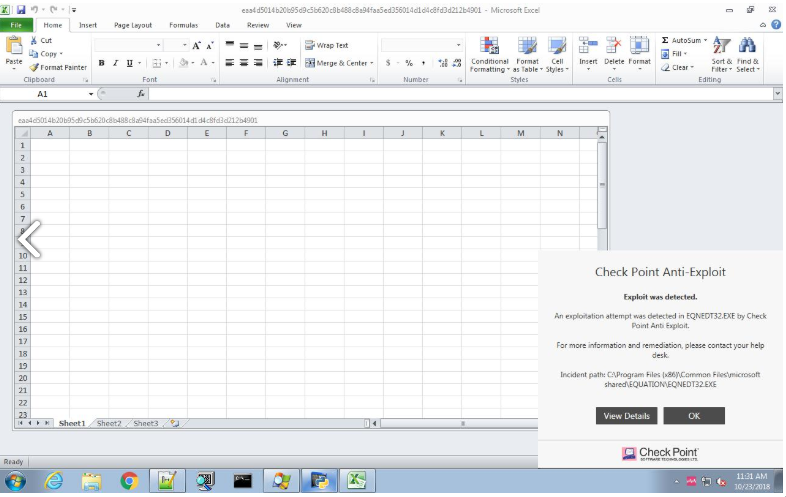
Figure 7. Anti-Exploit triggers on the infecting Excel file
As we allowed the attack to unfold, we get to a second layer of prevention. The shell code running inside the Equation Editor communicates to the known Command and Control that we gathered from the dynamic emulation in the Sandblast Sandbox. Now that it is connected to malicious activity, it would trigger prevention and remediation by the Anti-Bot integration into SandBlast Agent.
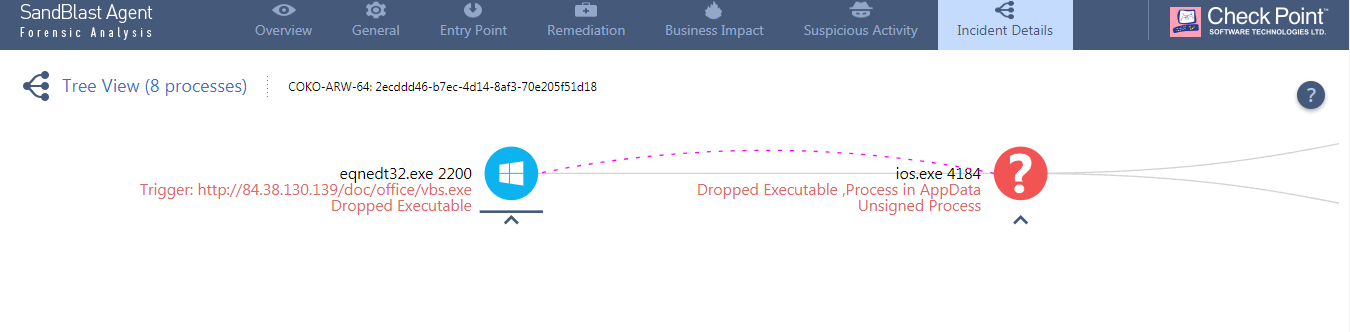
Figure 8. Infected Equation Editor communicates to download the payload
Next, we allowed the dropper to get through to the host with SandBlast Network and Anti-Bot and it continued to monitor the attack. When written to the disk, SandBlast Agent will pick it up. Then it will send it to SandBlast Threat Emulation for analysis. In real life, this malicious attack would have been blocked and remediated, but in order to gather more intelligence, we allowed the attack to “penetrate” our previous layers of defense.
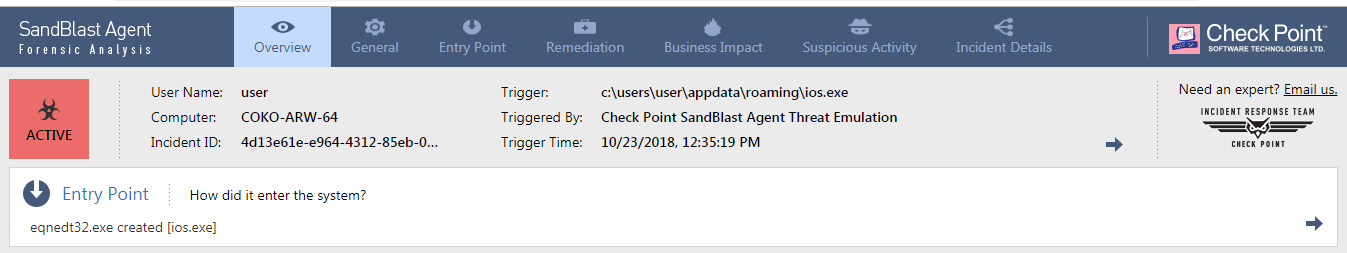
Figure 9. SandBlast threat emulation event when detecting the dropped file ios.exe on disk
As the dropper is allowed to run in our sandbox, the malware’s attempt to create multiple copies of itself triggers our “hash copy” heuristic behavior detection. This detection is part of our SandBlast Agent Behavioral Guard protection layer. Our behavioral detection locates a common set up action by malware that write itself to numerous directories and executes itself simultaneously.
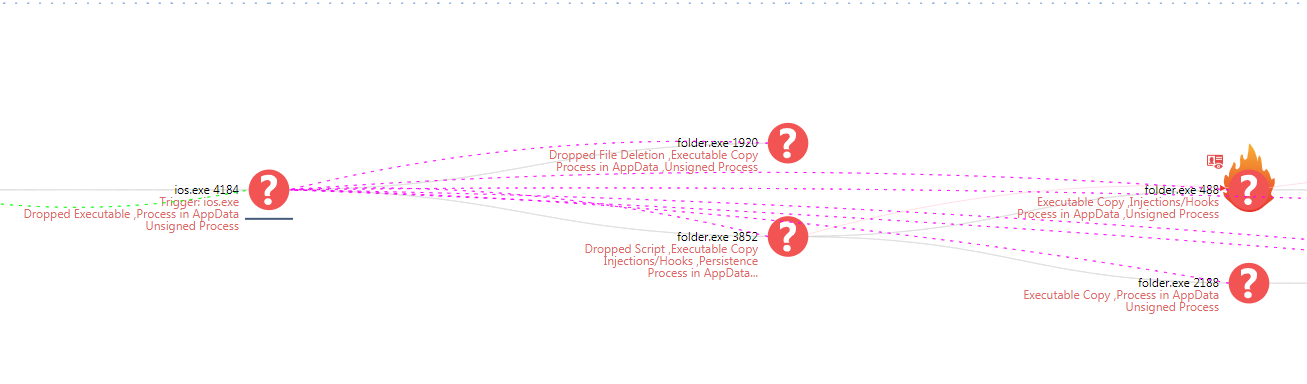
Figure 10. SandBlast Agent forensic report shows the dropper copying and executing itself
The Power Realized by the Check Point Infinity Architecture and SandBlast Threat Prevention
Using a real attack scenario, we’ve demonstrated how Check Point’s advanced threat prevention with signature-free, zero-day engines was able to detect an unknown malware. The shared threat intelligence, consolidated security management, and multi-vector security technologies are a few ways our Check Point Infinity Architecture helps secure your organization from today’s sophisticated Gen V mega cyberattacks and the constant threats from known and unknown zero-day malware.









