Check Point Forensic Files: Proving Ranscam ransomware does not provide a way to recover files
Every week we see new ransomware variants as cyber criminals continue to generate revenue from holding victims’ files for ransom. In July, a new ransomware was discovered that is an out-and-out scam. It does not encrypt any files; it simply deletes all user files. It then demands a ransom for recovery of the files, but infected users cannot recover the files even if they pay the ransom. Researchers at Cisco did an analysis of the ransomware dubbed “Ranscam,” which can be read here.
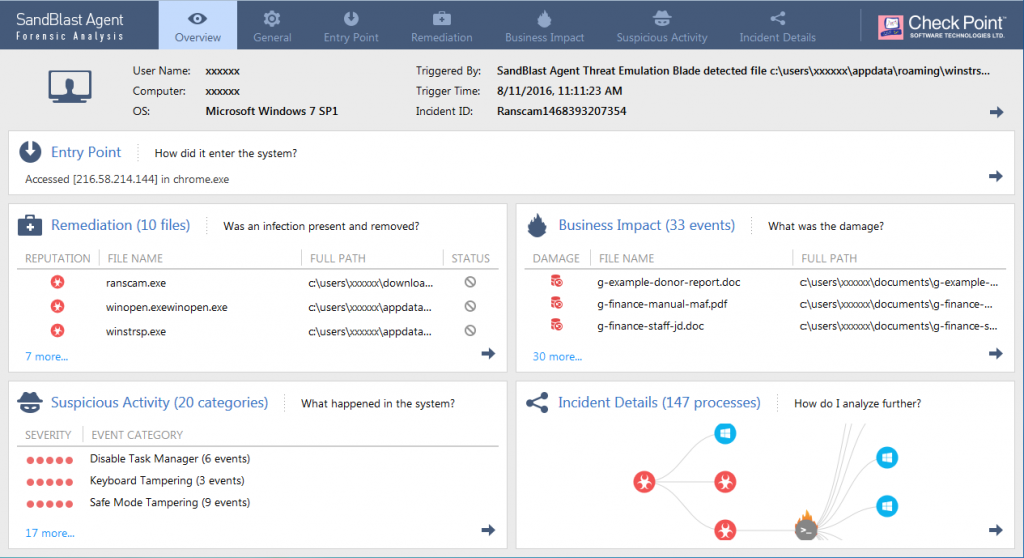
Figure 1: Forensic Analysis Overview. Click to open the interactive report.
The forensic report is best viewed on wide screens with resolutions greater than 1280 x 768. The ideal browsers to view the report are Chrome and Firefox. However, the report should display correctly in Safari, Internet Explorer 11 and Edge. Older versions of IE will not display the report correctly.
We ran Ranscam through SandBlast Agent Forensics with all security preventions disabled. Let’s take a look at what the forensics report shows us.
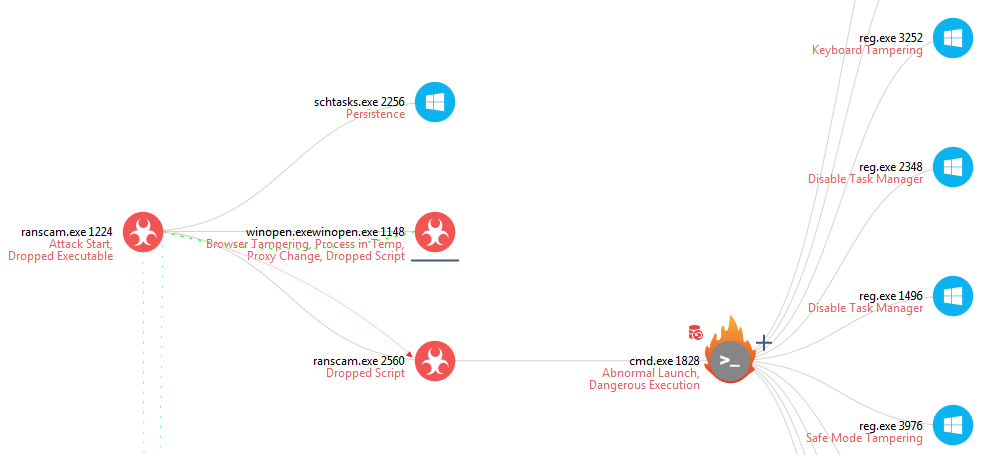
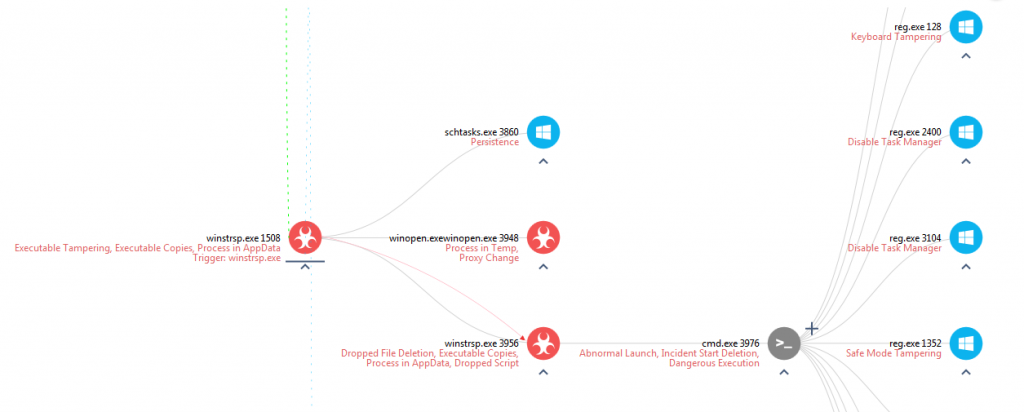
Figure 2. Ramscan tree view. Click to open the interactive report with the full tree.
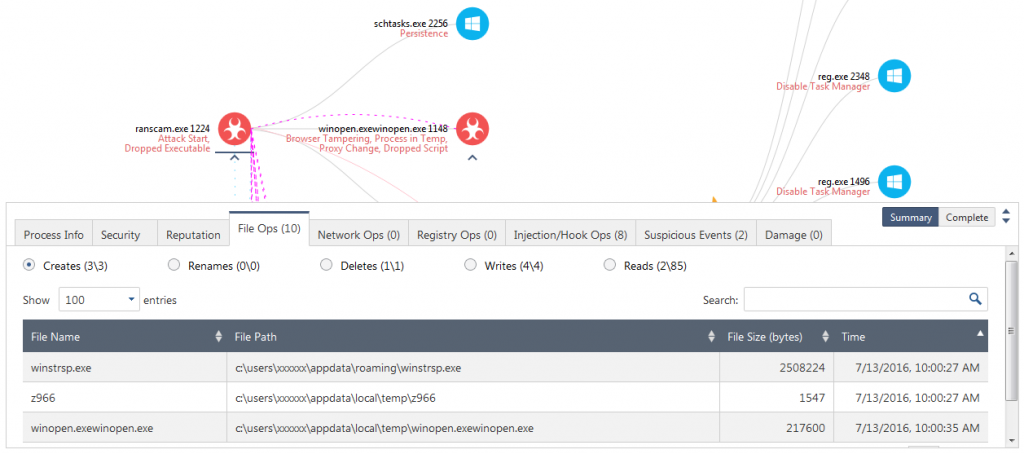
The attack starts with the execution (double click) of ranscam.exe (PID 1224). Once run, it creates three separate files as shown in Figure 3. Two of the files created are executables: winstrp.exe and winopen.exewinopen.exe.
Figure 3. Files created by Ranscam. Click to view all files in the interactive report.
The first child process executed by ranscam.exe (PID 1224) is Windows Scheduled Tasks. This is used by Ranscam to persist across boots. Looking at the arguments of the process schtasks.exe we see the following:
/Create /TN “Update\WVGtpmEUlXdWVGtpmEUlXdhuSpCpqZGMuTRLhuSpCpqZGMuTRL” /XML “C:\Users\xxxxxx\AppData\Local\Temp\z966”
The information about the process to load after boot is stored in the XML file C:\Users\xxxxxx\AppData\Local\Temp\z966 created earlier. The XML file contains configuration data that is used by Windows Task Scheduler to execute winstrsp.exe after boot. Of note is the fact that winstrsp.exe has the exact same contents as ranscam.exe as shown by the suspicious event “Executable Copies”.
After this ranscam.exe (PID 1224) executes winopen.exewinopen.exe and then executes a copy of itself: ranscam.exe (PID 2560).
Ranscam.exe (PID 2560) drops a batch file, which is then used as the argument to the cmd.exe (PID 1828) that eventually deletes all the user files. The process cmd.exe (PID 1828) actually launches multiple copies of itself in order to browse folders with the argument “dir /b”.
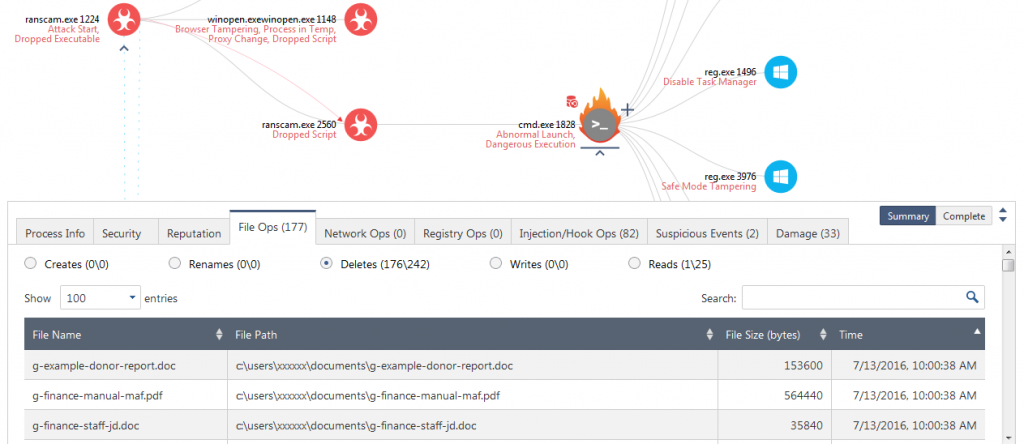
Figure 4 shows that cmd.exe (PID 1828) only deletes files; it does not create, write or rename any files. There are no other bulk file changes in any of the other processes involved in the attack. This implies that the malware was not encrypting any files and that the ransom payment request is a definite scam.
Figure 4. No files were created, renamed or written. Files were only deleted. Click to open the interactive report.
The process cmd.exe (PID 1828) also executes the reg.exe Windows process in an attempt to make changes to the registry. This can be seen through the suspicious events Keyboard Tampering, Disable Task Manager and Safe Mode Tampering.
After all user files are deleted, powershell.exe (PID 2476) is executed with the following arguments:
-ExecutionPolicy bypass -noprofile -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile(‘http://s3-us-west-1.amazonaws.com/docs.pdf/anon.jpg’,’C:\Users\xxxxxx\Desktop\Payment_Instructions.jpg’); cmd /c ‘C:\Users\xxxxxx\Desktop\Payment_Instructions.jpg’
In essence the file anon.jpg is downloaded from amazonaws.com and saved on the system as payment_instructions.jpg. The JPEG file is then displayed using cmd.exe (PID 2456). A screenshot of the payment instructions is shown in Figure 5.
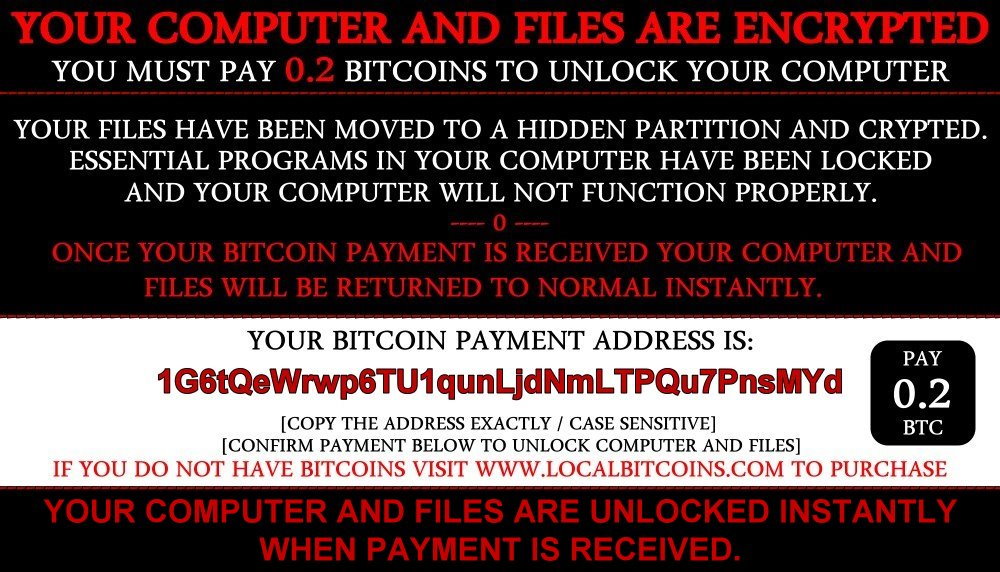
Figure 5. Ranscam Ransomware Message
Finally, by scrolling down in the interactive graph we can see the behavior on reboot (Figure 6.) and it looks exactly like the behavior from before reboot, without the damage icon (fire). This is not surprising as winstrsp.exe and ranscam.exe have the same hash, i.e. are the same files. They are just stored in different locations with different names.
Figure 6. Ranscam behavior after boot is similar to behavior before. Click to open the interactive report.
Read our Ranscam Interactive Forensics Report, generated by SandBlast Agent, for a more detailed look at the Ranscam ransomware. For more information on protecting your organization against ransomware, and our forensics capabilities, please visit our SandBlast Zero-Day Protection and SandBlast Agent webpages.