
The Tipping Point: Exploring the Surge in IoT Cyberattacks Globally
Check Point Research flags a sharp increase in cyberattacks targeting IoT Devices
Highlights:
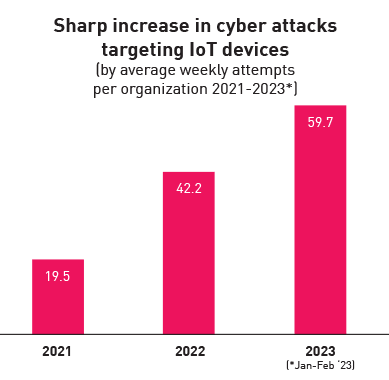
- The first two months of 2023 have seen a 41% increase in the average number of weekly attacks per organization targeting IoT devices, compared to 2022.
- On average, every week 54% of organizations suffer from attempted cyber attacks targeting IoT devices
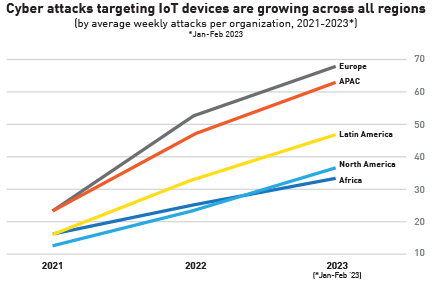
- IoT devices in European organizations are the most targeted, followed by those in APAC and Latin America-based organizations.
The Internet of Things (IoT) has become an integral part of our daily lives. However, with the growing use of IoT devices, there has been an increase in cyberattacks against these devices in recent years, using various exploitable vulnerabilities. One contributing factor to this increase is the rapid digital transformation that occurred in various sectors, such as education and healthcare, during the pandemic. This transformation, driven by the need for business continuity, often took place without proper consideration of security measures, leaving vulnerabilities in place.
Cybercriminals are aware that IoT devices are notoriously one of the most vulnerable parts in the networks, with most not properly secured or managed. With IoT devices like cameras and printers, its vulnerabilities and other such unmanaged devices can allow direct access and significant privacy violation, allowing attackers an initial foothold into corporate networks, before propagating inside the breached network.
In the first 2 months of 2023, almost every week, on average 54% of organizations were targeted by these attack attempts, with an average of almost 60 attacks per organization per week targeting IoT devices – 41% higher than in 2022, and more than triple the number of attacks from 2 years ago. These IoT devices attacked range from a variety of common IoT devices like routers, IP cameras, DVRs (digital video recorders) to NVRs (network video recorders), printers and more. IoT devices such as speakers and IP cameras have become increasingly common in remote work and learning environments, providing cybercriminals with a wealth of potential entry points.
This trend was observed across all regions and sectors. Europe is the region currently suffering from the most attacks targeting IoT devices, with an average of almost 70 such attacks per organization every week, followed by APAC with 64, Latin America with 48, North America with 37 (and the largest increase from 2022, with 58%), and Africa with 34 weekly IoT cyber-attacks per organization.
The education and research sector is currently facing an unprecedented surge in attacks targeting IoT devices, with 131 weekly attacks per organization—more than twice the global average and a staggering 34% increase from the previous year. Other sectors are also witnessing a surge in attacks, with most sectors experiencing double-digit growth compared to 2022 as per the table below:
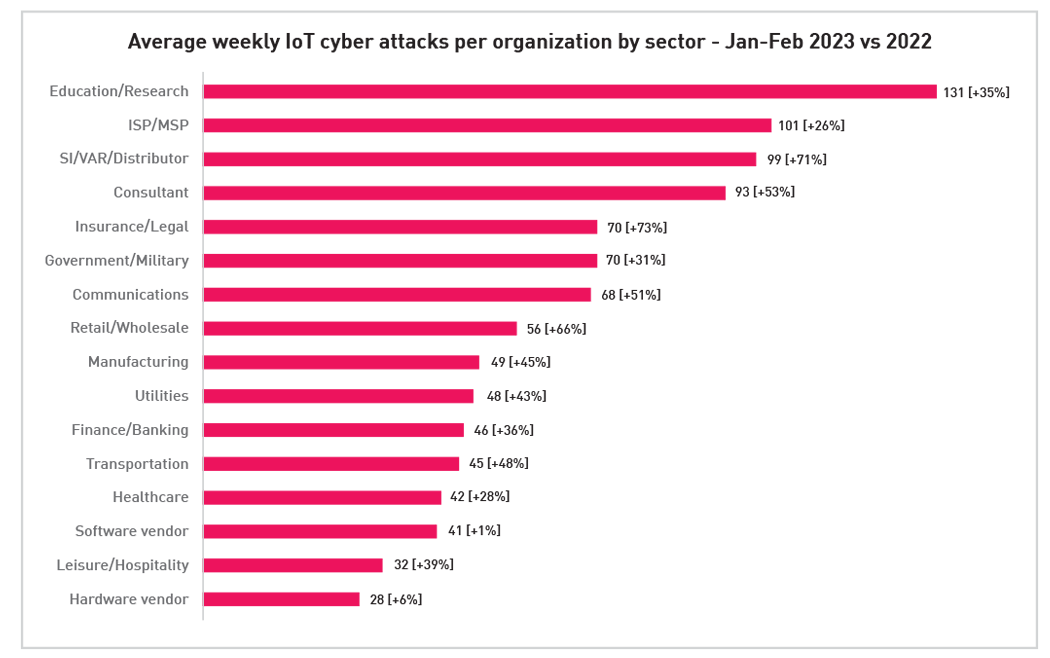
Prior reports by Check Point Research revealed that hackers prefer to target schools as “soft targets” due to the abundance of personal data stored on school networks, making both students and schools vulnerable. The shift to remote learning has significantly expanded the attack surface for cybercriminals, as the introduction of numerous unsecured IoT devices into school networks has made it easier for hackers to breach these systems. Additionally, the lack of investment in robust cybersecurity prevention and defense technologies by schools makes it even simpler for cybercriminals to carry out phishing attacks and deploy ransomware.
Top Attacks
While the threat landscape for IoT vulnerability exploits contains hundreds of vulnerabilities, some are seen widely more than others in scanning and attack attempts against corporate networks. These are the top 5 exploits that have been seen in the wild since the beginning of 2023:
- MVPower DVR Remote Code Execution: This exploit impacts an average of 49% of organizations every week.
- Dasan GPON Router Authentication Bypass (CVE-2018-10561): impacts 38% of organizations weekly.
- NETGEAR DGN Command Injection: impacts 33% of organizations weekly
- D-Link Multiple Products Remote Code Execution (CVE-2015-2051): impacts 23% of organizations weekly.
- D-Link DSL-2750B Remote Command Execution: impacts 14% of organizations weekly.
Prevalent Injection Attacks on IoT Devices
Command Injection represents a critical and frequently exploited vulnerability in IoT devices. Attackers can inject commands into the program, taking advantage of the vulnerable application’s privileges. The widespread adoption of IoT devices has made this type of vulnerability a prime target for cybercriminals.
Vulnerability scanners are widely used to identify and exploit weaknesses in web applications and APIs. While these tools have legitimate uses, attackers may also employ them for malicious purposes. Two increasingly popular tools include Out-of-band security testing (OAST) and “Interact.sh.”
The scanning technique serves as a filtering tool to pinpoint potential victims. When attack complexity is low, scanning has become a favored initial step for attackers. The process entails sending a simple payload to a large group, with vulnerable targets responding to the initial request, confirming their vulnerability. This method falls under active scanning, the first step in the MITRE Matrix for Enterprise—a hierarchical framework of attack tactics and techniques used by cybercriminals.
Scanning enables attackers to verify the vulnerability of their targets and ensure only they receive the actual malicious payload. Research findings indicate that during a one-week testing period, at least 3% of networks were affected by this scanning method. The top exploits employing this attack method on IoT devices include:
- NETGEAR DGN Command Injection
- Netgear R7000 and R6400 cgi-bin Command Injection (CVE-2016-6277)
- FLIR AX8 Thermal Camera Command Injection (CVE-2022-37061)
- Multiple IoT Command Injection
How can organizations protect themselves against IoT attacks
With the increase reliance that organizations have on IoT devices for daily operations, it is crucial that they remain vigilant and proactive in securing these devices. Some steps that can be taken to improve IoT security include:
- Purchasing IoT devices from reputable brands that prioritize security, implementing security measures inside the devices before distribution to market.
- Practicing password complexity policies and using multi-factor authentication (MFA) when applicable.
- Ensuring connected devices are updated with the latest software and maintaining good device health.
- Enforcing zero-trust network access profiles for connected assets.
- Separating networks for IT and IoT when possible.
Check Point recently announced Check Point Quantum IoT Protect as part of the Quantum ‘Titan’ release R81.20, which revolutionizes network security by blocking the most evasive zero-day DNS, phishing, and IoT attacks. Check Point Quantum IoT Protect assists organizations in automatically discovering and protecting IoT assets within minutes.
As technology continues to advance, so will the sophistication and frequency of cyberattacks. By implementing robust security measures and staying informed about the latest threats and best practices, organizations can better protect themselves and their IoT devices from cybercriminals.
The statistics and data used in this report present data detected by Check Point’s Threat Prevention technologies, stored and analyzed in Check Point’s ThreatCloud AI. Check Point ThreatCloud AI provides real-time threat intelligence derived from hundreds of millions of sensors worldwide, over networks, endpoints, mobiles and IoT devices. The intelligence is enriched with AI-based engines and exclusive research data from the Check Point Research – the intelligence and research arm of Check Point Software. The data on this report has been analyzed looking back from the beginning of 2021, all through March 2023.









