
Conditional QR Code Routing Attacks
Over the summer, we saw a somewhat unexpected rise in QR-code based phishing attacks.
These attacks were all fairly similar. The main goal was to induce the end-user to scan the QR Code, where they would be redirected to a credential harvesting page.
Fairly simple, but it was successful as many email security solutions didn’t have QR code protection and many end-users are used to scanning QR codes. It’s why we saw a 587% increase between August and September of these attacks.
Security vendors furiously worked to develop new protections for these attacks. And, as always happens, threat actors responded in kind with a new variation on QR code attacks.
In these attacks, hackers are utilizing QR code in a different way. The initial ask is similar, but where the redirection chain goes is quite different. In short, the link looks for where the user is interacting with it and adjusts accordingly. If the user is using a Mac, one link appears. If the user is using an Android phone, another one pops up.
The end-goal is the same—install malware on the end-user endpoint, while also stealing credentials. But by adjusting the destination based on how the end-user is accessing it, the rate of success is much higher.
In a span of two weeks in January, we saw just under 20,000 of these attacks.
In this attack brief, Harmony Email researchers will discuss how hackers are taking QR code attacks to the next level.
Attack
In this attack, hackers are sending QR codes with conditional routing based on device.
- Vector: Email
- Type: QR Code, Conditional Redirection, Credential Harvesting
- Techniques: Social Engineering, BEC 3.0
- Target: Any end-user
Email Example
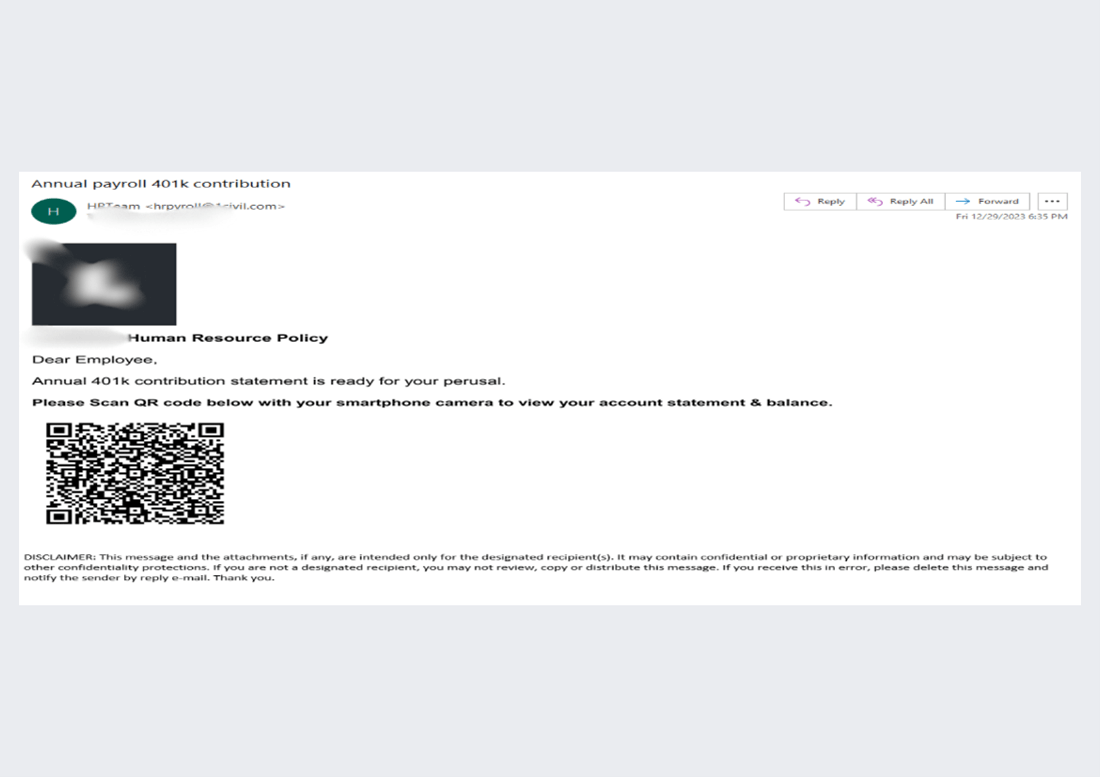
This email starts as a fairly standard QR code based phishing attack. The ask is to look at the annual 401K contribution statement by scanning the QR code. It will give you your account balance for the year.
What’s neat about this attack is what happens next.
The QR Code has a conditional destination point, based on browser, device, screen size and more. Depending on the parameters, the QR code would direct to a different page.
The link in the email is all the same:
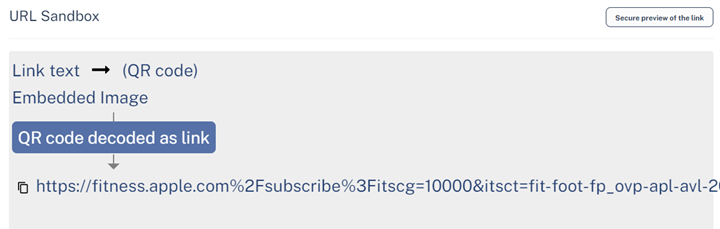
However, depending on the destination, the result changes:
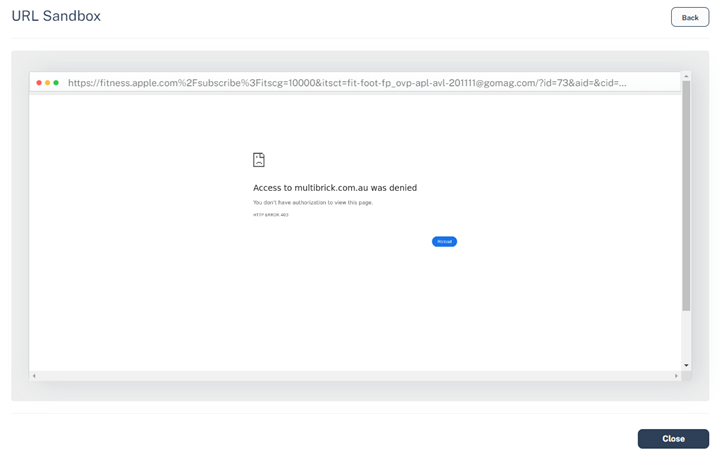
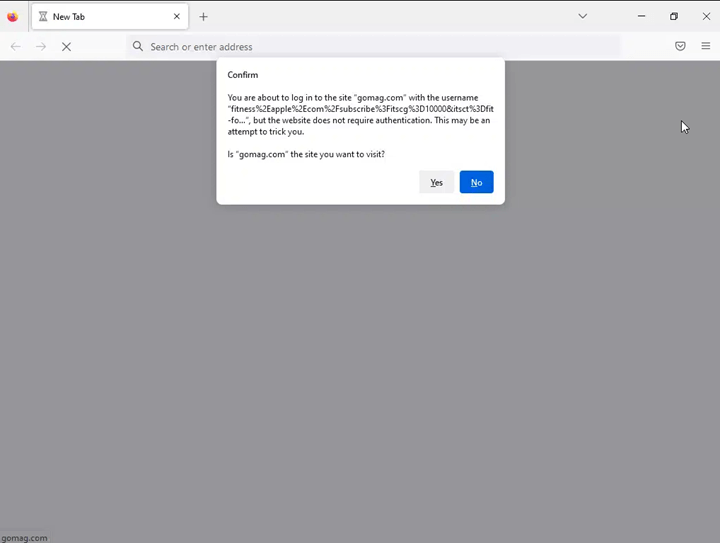
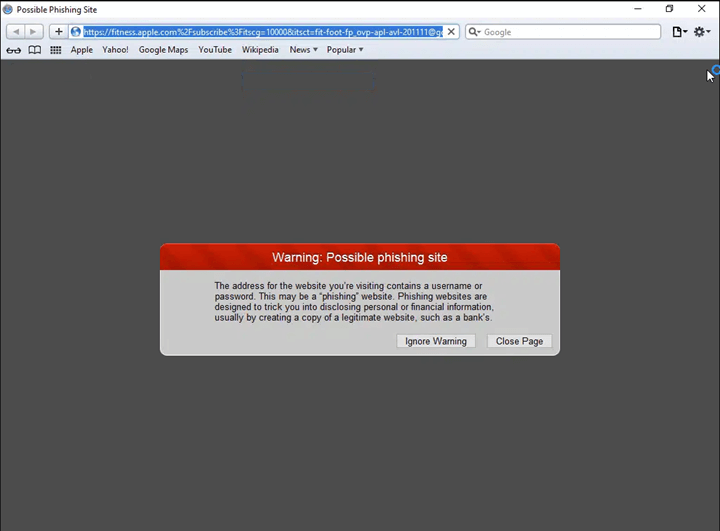
Essentially, there are four layers of obfuscation. One is the QR code itself. The URL embedded within the QR code looks like it’s going to a domain of Apple’s, but is instead redirected elsewhere. Then there’s a blind redirect to another domain. That domain has automatic checks to see if you are coming from a browser or a scanning engine, and would redirect accordingly.
There’s also a payload in there that has anti-reverse engineering techniques so that if you try to de-obfuscate it, it would consume infinite resources.
Here’s another example. This embeds the QR code in an PDF, attached to the email.
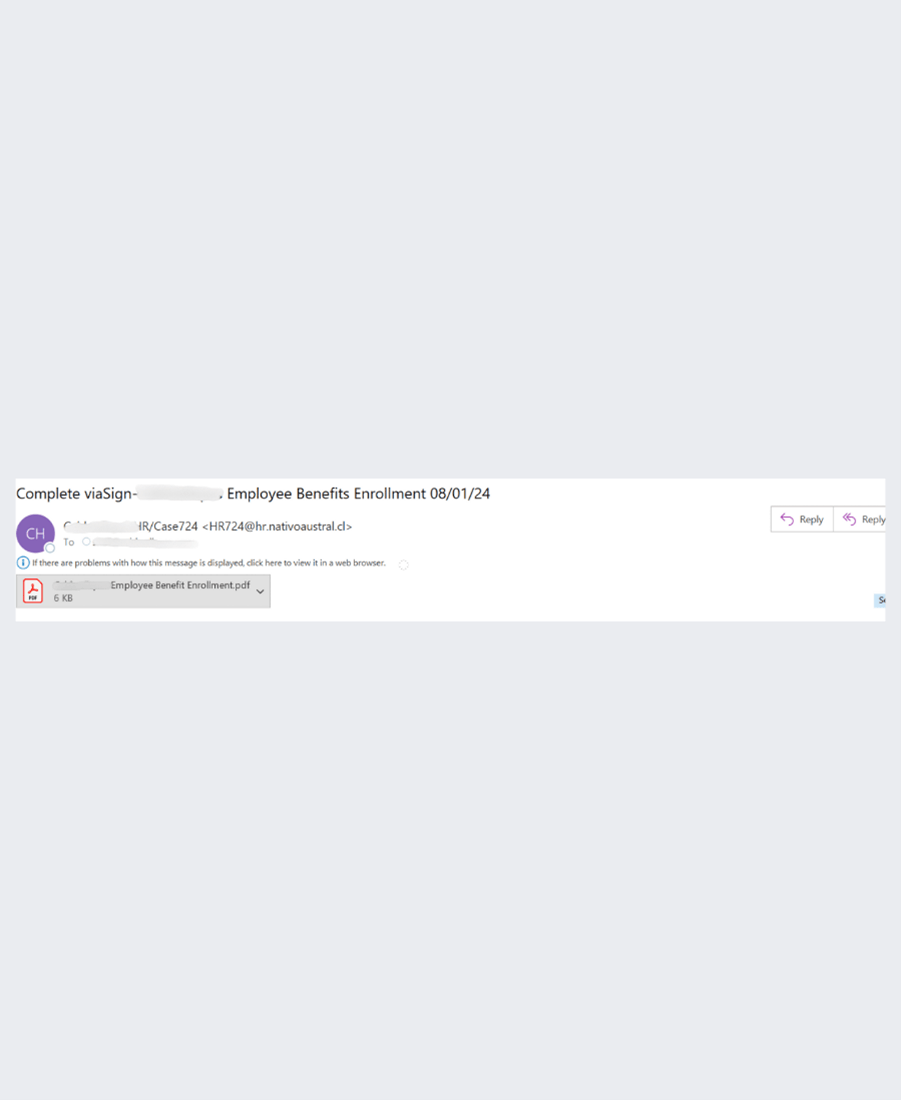
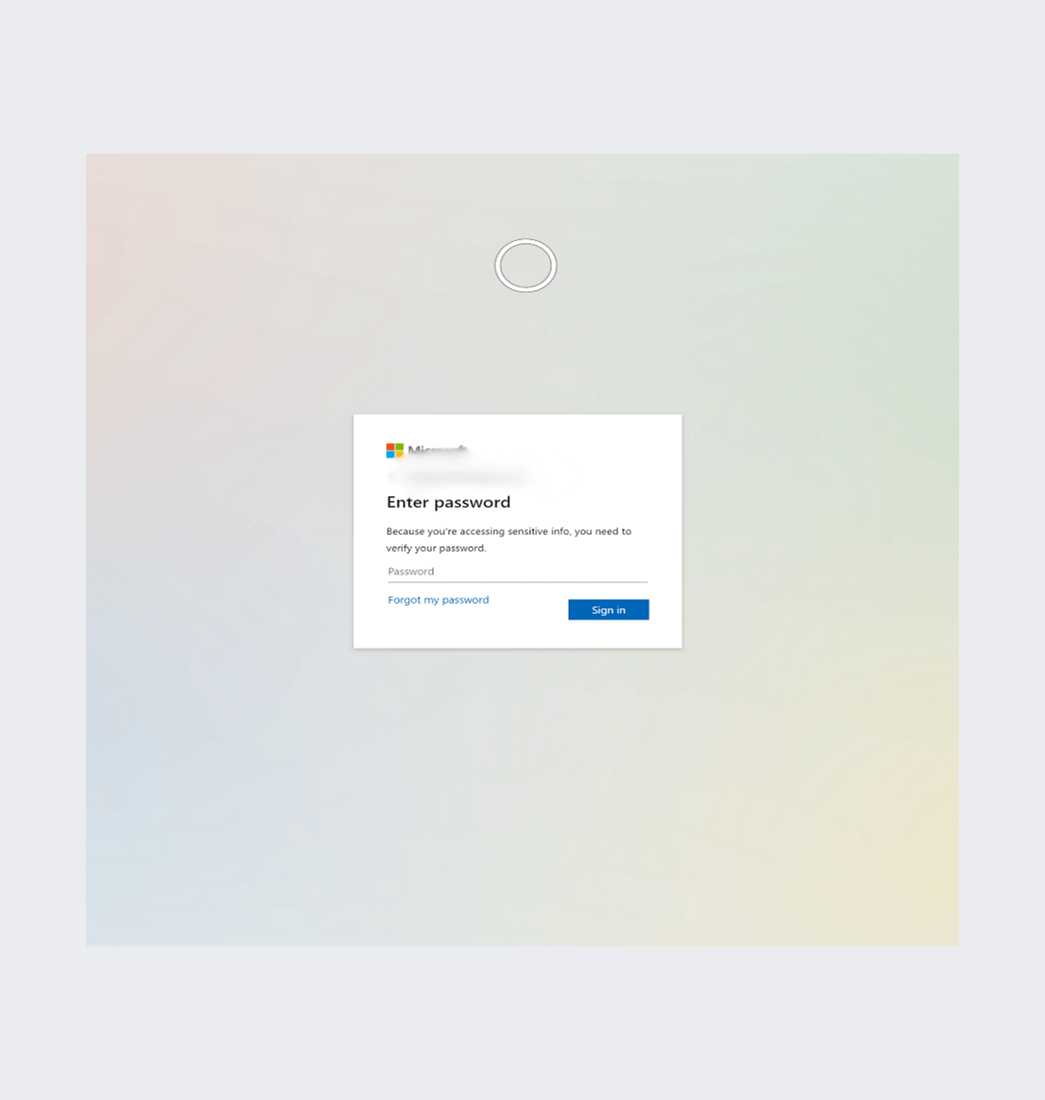
This has a number of suspicious activities attached to it, again around hooking to a program to continually drain resources. It also leads you to a fake Microsoft login page.
And here’s another variation:
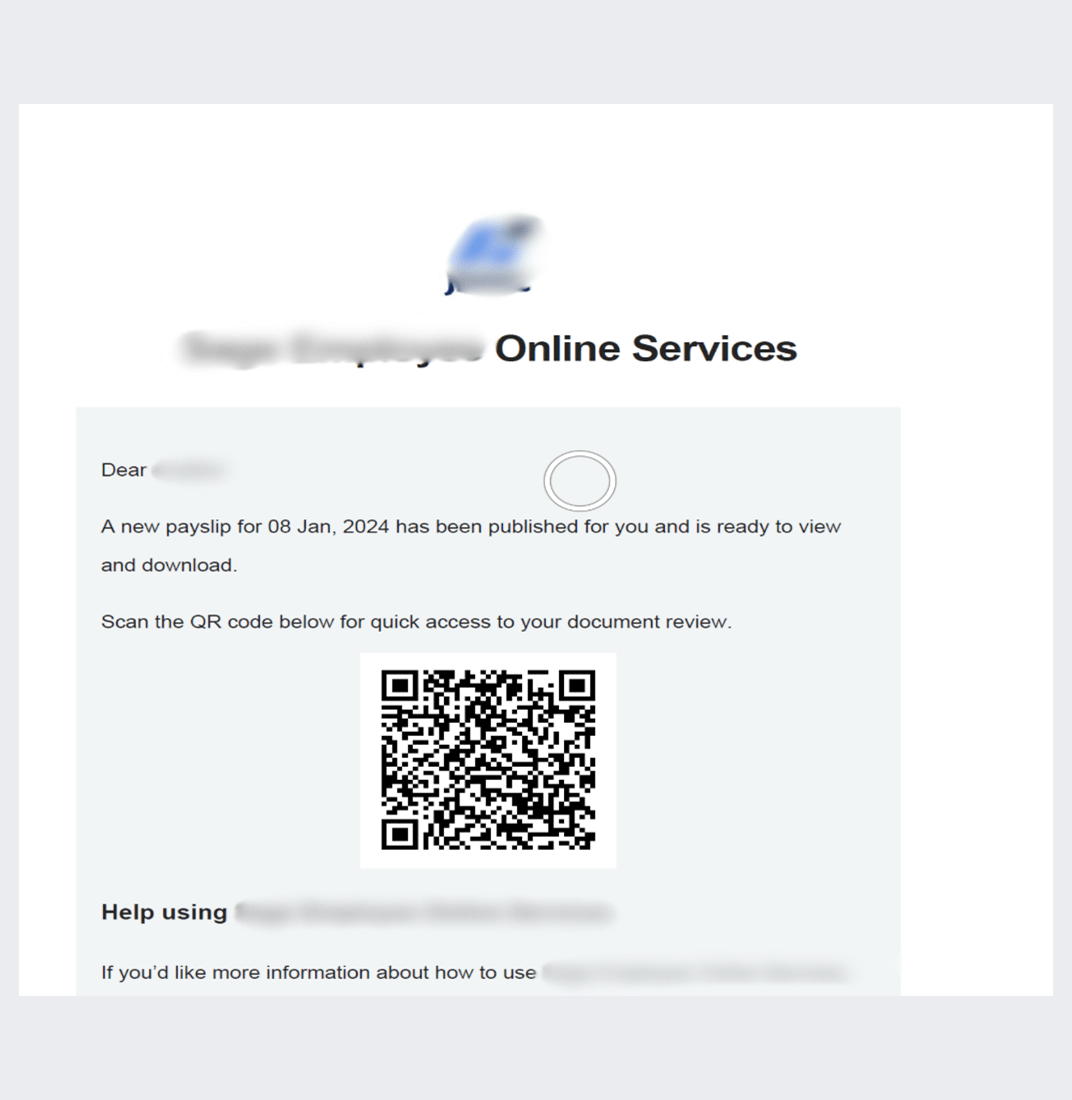
In all of these, the link in the QR code and the link that it redirects you to are different.
Techniques
Redirection in an attack is not necessarily new, although the use of it in QR Codes is fascinating.
By navigating conditional redirection, hackers are able to increase their ability to succes. Typically, default layers of security will look at a redirection and if the first one is clean, they will let it go. (That’s what happened on this attack).
This is where the power of complete security solution comes into play. With a complete security solution, multiple layers can work to prevent these attacks.
In this example, an email security solution can block it by looking at suspicious behavior, such as first-time sender, text analysis and more. Browser security can block it by inspecting the website and emulating any actions. Mobile security can block it upon the actual scanning of the QR code. Anti-malware can emulate the file and understand what will happen. Post-delivery security can continually look at new information, continually scanning and emulating the URL.
These attacks are difficult to stop because they compromise so many different layers. Have all the layers, though, and the ability to stop the attack increase.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that uses AI to look at multiple indicators of phishing
- Implement security with the ability to decode QR code attacks
- Implement security with multiple layers of protection.









