
Phishing Through Venmo
Introduction
Venmo is one of the most popular payment apps in the world. Owned by PayPal, Venmo is an easy way for friends to send money back and forth. It’s also used by many businesses, and the app’s social network feature adds another dimension.
In Q3 of 2023, the total payment value on the app was $68 billion, a YoY growth of seven percent. Further, according to Statista, it is among the top three payment brands in the US.
It is, however, primarily a US-focused brand, with over 97% of its customers from the US.
With its popularity in the US—62.8 million active users, or about one in every five US consumers–scams are bound to happen.
Over the last few years, we have written extensively about how threat actors are using PayPal for phishing purposes.
There are two types of attacks that are popular: One is a standard spoof of PayPal. The email does not come from PayPal, but instead looks like it does. The sender address and links are all different.
The other type actually comes from PayPal. Hackers create accounts in PayPal, and send invoices directly from PayPal. The email comes from PayPal and any links come from PayPal. The tip-off in the attack is that the memo box offers a phone number to call—that number is associated with a scam, and if you do call, they will try to gather credit card and other personal information.
Now, we’re seeing similar attacks coming directly from Venmo. (Venmo is owned by PayPal.)
These attacks involve sending payment notifications from Venmo. There is a scam phone number attached to the email that the threat actor wants you to call.
In this attack brief, Harmony Email researchers will discuss how hackers are sending invoices from Venmo in the hopes of getting a call back to steal credit card information.
Harmony Email Researchers notified Venmo of this campaign on February 13th.
Email Example
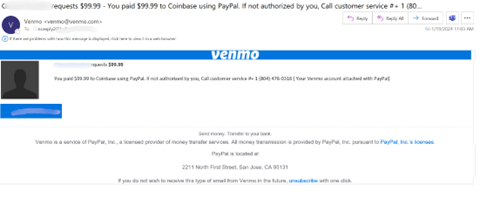
The email starts as a notification, directly from Venmo, that the end-user has paid $99.99 to Coinbase. The user will note that’s not accurate, and, the threat actor hopes, will call the number listed.
If you Google that number, nothing comes up and is not associated with Venmo, PayPal or Coinbase.
The hacker is hoping that, when you call, you’ll confirm personal information to “reverse” the charge. This can include credit card information or other banking info.
Here’s another example.

This purports to come from Norton, but again, the phone number is not associated with Venmo, PayPal or Norton.
Techniques
The challenge with spotting these attacks is that these emails are not, in and of themselves, malicious. In fact, in the case of the particular organization that this was sent to, there’s a significant sender history with Venmo.
Let’s go deeper. It passes SPF checks and DKIM checks. The link is legitimate. There is no suspicious text.
It has all the hallmarks of a clean email because it is a clean email. Venmo is a safe organization and so are their emails.
Like many of these BEC 3.0 attacks, however, it pays to go a little deeper. In this case, the phone number is a tell for our AI engines. The phone number is not legitimate, and instead is directed to a number that scammers control.
It’s a small detail. And it’s probably not going to be caught by many services. But small details count.
This attack also lends itself to further attacks. It uses what we call “phone number harvesting.” When you call the number listed in the email, they can easily obtain it through called ID. Once they obtain the phone number, they can carry out further attacks, whether it’s through SMS, WhatsApp or phone calls. Just one attack—even if not fully successful—can lead to dozens of others.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that uses AI to look at multiple indicators of phishing
- Implement security with robust URL protection to scan and emulate webpages
- Implement security that can scan phone numbers in addition to traditional indicators of phishing









