
Microsoft and Google Top the List in Q1 2024 Phishing Attacks: Check Point Research Highlights a Surge in Cyber Threats
Airbnb’s Entry into Top 10 Imitated Brands Signals Expanding Cybercriminal Horizons
In the ever-evolving landscape of cyber threats, phishing attacks continue to pose a significant risk to individuals and organizations worldwide. Check Point Research (CPR), the Threat Intelligence arm of Check Point® Software Technologies Ltd., has recently released its latest Brand Phishing Ranking for the first quarter of 2024. This ranking shed light on the brands most frequently imitated by cybercriminals in their relentless attempts to deceive and steal personal information or payment credentials.
During the first quarter of 2024, Microsoft continued to be the most imitated brand in phishing attacks, accounting for a staggering 38% of all brand phishing attempts. Google made a modest advance to the second spot, capturing 11% of attempted brand phishing attacks, up slightly from its previous third-place position. Similarly, LinkedIn also saw a rise to third place, with 11% of such attempts, marking a notable increase from the previous quarter.
In a remarkable turn of events, Airbnb made its debut in the top brands list, securing the 10th position. This impressive climb is likely influenced by the Easter season, a period associated with increased travel and holiday bookings. The seasonal surge in vacation planning could have amplified Airbnb’s visibility and appeal, particularly among travelers seeking unique accommodations.
The Technology sector remained unchanged as the most impersonated industry in brand phishing, followed by Social Networks and Banking. The technology brands lead in phishing attacks, likely due to their widespread usage in corporate and remote work environments, making them a lucrative entry point into company assets. In many cases they are used with the employee’s internal credentials, and their exposure poses an even larger risk than the disclosure of an individual’s personal details used in social media, shipping or banking platforms.
In light of the persistent threat posed by brand impersonation, it is imperative for users to maintain a heightened level of vigilance and exercise caution when engaging with emails or messages purportedly from trusted brands. By remaining vigilant and adopting proactive cybersecurity practices, individuals can mitigate the risk of falling victim to cybercriminal tactics.
Top Phishing Brands for Q1 2024:
- Microsoft (38%)
- Google (11%)
- LinkedIn (11%)
- Apple (5%)
- DHL (5%)
- Amazon (3%)
- Facebook (2%)
- Roblox (2%)
- Wells Fargo (2%)
- Airbnb (1%)
DHL Phishing Email – Shipping Information Scam
In the first quarter of 2024, we observed a phishing campaign involving a deceptive email, purportedly from DHL EXPRESS, claiming to provide critical updates regarding DHL shipments.Sent from the address message-system-express@shipping.com, the email urged recipients to take immediate action, featuring a subject line indicating the importance of the contained information: “Important: Latest Information Regarding DHL Shipments.”
The phishing link embedded in the email directed recipients to a fraudulent website: nangrong.ac.th/shiping. This website, claiming to be a legitimate DHL service, presents itself under the title “Package Protection Center.” It displays a simulated shipping process for a package supposedly in “Pending” status and asks for a small payment to resume delivery (figure).
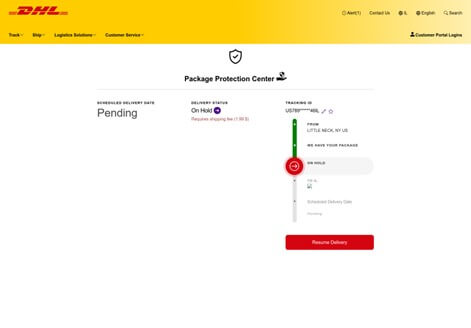
The phishing website: nangrong\.ac\.th/shiping
Microsoft Phishing Campaign – Deceptive Email Notifications
This phishing campaign utilizes a variety of false email subjects and sender identities to deceive recipients. The deceptive emails include subjects such as “Message Failure Delivery Notice”, “Outlook Info Replacement”, “Annual Leave Compliance Report for 2024” and “Please Complete: Invoice from DocuSign Electronic Signature Service.”
The phishing website (b542df20-c26b-4c27-8ab9-9584ed34b2f4-00-16s5vbpwefi3f.riker.replit.dev) resembles a typical Outlook login page, aiming to trick users into providing their credentials (see figure). This campaign is intended to deceive recipients into revealing sensitive information, posing a significant security threat for organizations.
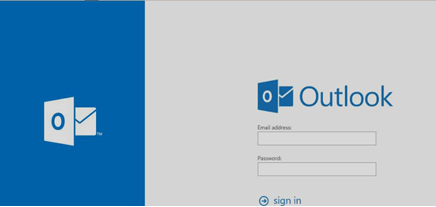
The phishing website: b542df20-c26b-4c27-8ab9-9584ed34b2f4-00-16s5vbpwefi3f\.riker\.replit\.dev
As these threats increase, it’s become even more important to adopt proactive security solutions. Utilizing advanced AI and ML, Check Point Harmony Email & Collaboration is able to block these phishing campaigns from reaching inboxes. One way it does this is through a specific brand spoofing AI engine. Looking at a number of features, such as domain, favicon, title, HTML properties and more, we are able to identify and block spoofed phishing campaigns.









