
Spoofing Temu for Credential Harvesting
Introduction
Temu, an international online e-commerce store that has quickly gained prominence, offers discounted goods directly shipped to consumers without intermediate distributors. Launched in 2022 and owned by Pindouduo, it has attracted a large audience, with 40% of its downloads originating from the United States. Presently, Temu is available in 48 countries worldwide, spanning Europe, the Middle East, Southeast Asia, and Australia.
As reported by AppMagic, the following is the geographical distribution of Temu’s downloads.
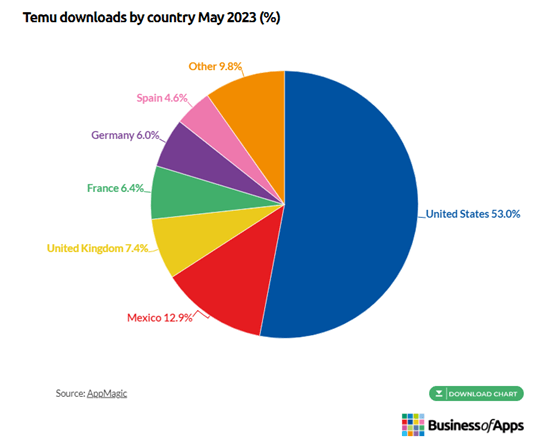
As of February 7, 2024, Temu is ranked as the number one shopping app on Google Play Store and holds the second spot on the Apple App Store. It stands out as one of the most widely downloaded apps in the United States and has gained substantial popularity on TikTok and other social media networks. According to a recent Bloomberg article with sources from Attain, Temu’s most frequent shoppers are in the 59 and older age bracket, while 18 to 26 year olds the least likely to shop on the app.
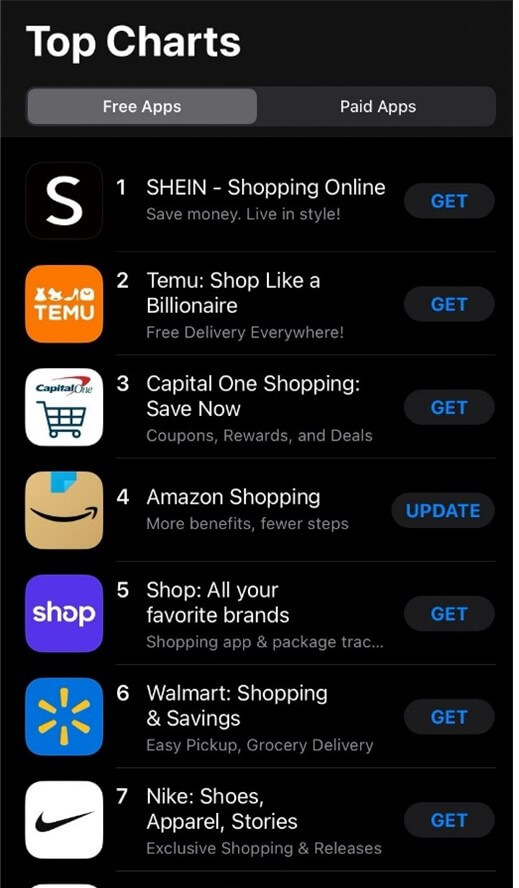

The popularity of the site has led to scams, including fake giveaway codes.
This leads us to our attack today. Temu codes are like a currency—the more someone refers a code, the more rewards they get. Rewards include discounts and free items.
Harmony Email researchers will discuss how hackers are utilizing fake Temu rewards to entice users to give over credentials. In the last two weeks, we’ve seen dozens of these scams. Further, Check Point Research reports that, in the last three months, there have been over 800 new domains registered with the name “Temu” in it.
Email Example
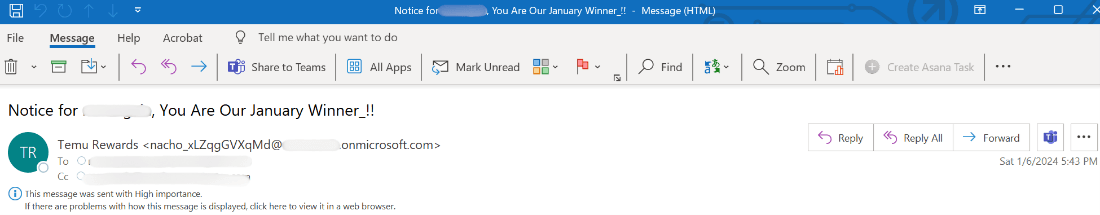
The email starts with a notice saying that the user is the January winner. The email purports to come from Temu rewards—but in fact, the email comes from an onmicrosoft.com email address.
There’s a blank image with a link in the body of the email. That goes to a credential harvesting page.
This is a pretty straight forward phishing email. It’s hoping to get the user’s attention by stating that they are a winner. With Temu as the “sender”, the threat actors are hoping the brand name will get the user to act.
Of course, if an eagle-eyed user saw that the sender address had nothing to do with Temu, or that the links didn’t go to a Temu page, they would know to stay away.
Techniques
Like many credential harvesting scams, threat actors try to take advantage of brand names and the latest trends. In this case, the brand name is Temu.
There are plenty of classic signs that this email is not what it says it is. First, there’s a ton of fake urgency, surrounding being named the January winner.
Second, the email comes from a generic onmicrosoft.com, not from Temu. Third, the image does not load, it’s just blank. And the link in that image does not go to a Temu page, but rather a phishing website.
Still, even what seems like the most obvious threats can get through defenses and can entice users to click. That’s why it’s important to emphasize the basics with users and ensure you have security that can stop all threats—simple and sophisticated.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that uses AI to look at multiple indicators of phishing
- Implement security with robust URL protection to scan and emulate webpages
- Implement full-suite security that can also scan documents and files









